Tag Archives: encryption
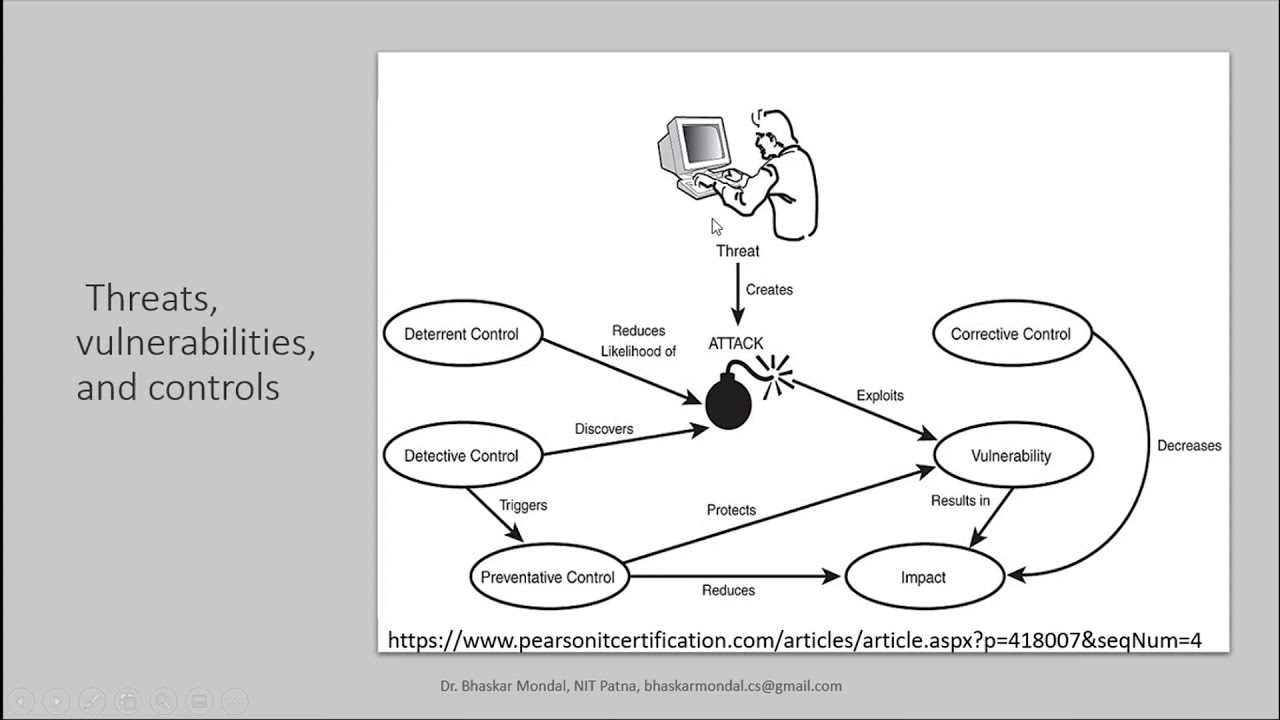
Threats, vulnerabilities, and controls in Information Security
Access ControlAESAIassignmentcode for beginners tutorialcomputecrypto systemcryptographycyber attackcyber securityDBMSdecryptiondeep learningDESdiyECCencryptionFLATguideHow toIDSinformation securityinstallintrusion detectionLATEXlearn to programlecturemachine learningMLNetwork Securityprivate keyprogrammingpublic keypythonrsascientific computingSecuritySHASQLTOCtutorial“computer laboratory” computer science GATE


Day 1 Part 2: Intro Trusted Computing
attestationAuthenticationclassesComputercomputer securitycomputer security classcryptographycyber securityCybersecuritydecryptiondigital signaturesDRTMdynamic root of trusteducationencryptionOpenSecurityTraining.infoPCRPCRsSecuritySRTMstatic root of trustTPMtrainingtrustTrusted ComputingTrusted Computing Grouptrusted hardwareTrusted Platform Module
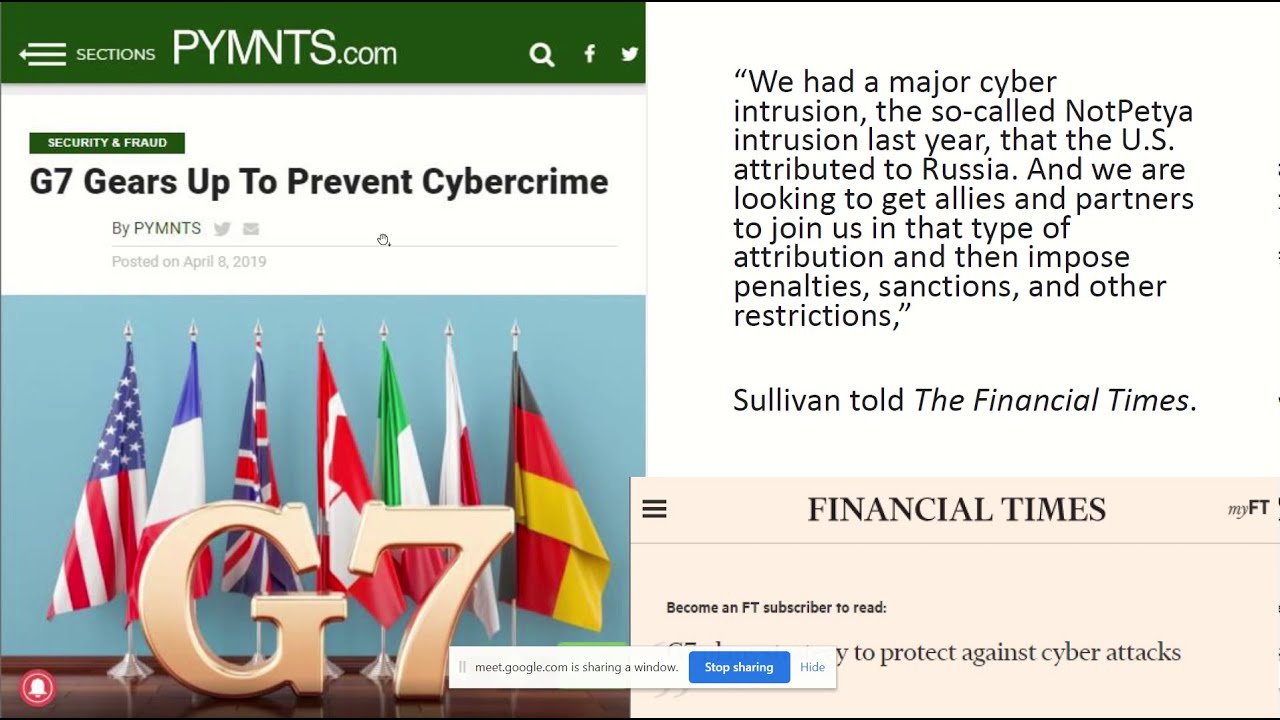
Keynote Talk on Cyber Security and Symmetric Key Encryption
Access ControlAESAIassignmentcode for beginners tutorialcomputecrypto systemcryptographycyber attackcyber securityDBMSdecryptiondeep learningDESdiyECCencryptionFLATguideHow toIDSinformation securityinstallintrusion detectionLATEXlearn to programlecturemachine learningMLNetwork Securityprivate keyprogrammingpublic keypythonrsascientific computingSecuritySHASQLTOCtutorial“computer laboratory” computer science GATE

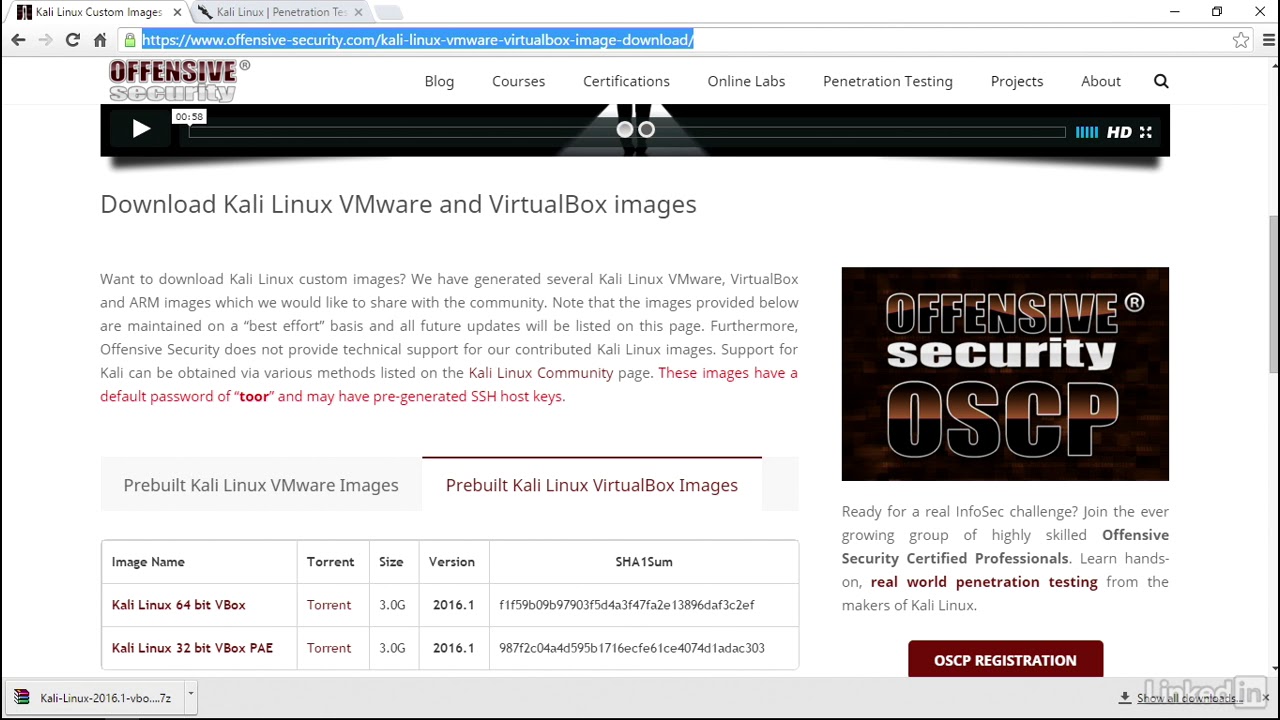
5 Installing appliances | Ethical Hacking
access pointaircrack-ngalfa cardapbacktrack linuxciscoComputercomputer securityencryptionfor beginnershackerhacking kalihacking wirelessInjectionKalikali linuxkali linux 2.0kali linux 2017.1kali linux 2017.2kali linux androidkali linux wifiklai linux 2017.2linksysLinuxlinux installmonitor modepasswordpassword crackingrouterSecuritytutorialwalkthroughwirelesswpa2
Using Pod Security Policies to harden your Kubernetes cluster
2019alertingArchitectureautomatebountybugcertificatecloudclusterdefenseDevopsDevSecOpsDistributedElixirencryptionengineeringfeedbackfunctionalhasgeekKafkakeykuberneteslogmaliciousmanagementmanagermonitoringmultinetworkOLAPOLTPOnionOpenopenscapOSINTpodpolarDBPolicyprogrammingpythonreliabilityremoterootconfroutingSecurityServersourceSRESSHstreamsSystemtenantTortrafficusabilityUserVitessWireshark

The Dark Side of the GDPR – Parte I: Compliance
cifraturaCybersecurityData breachdata protection officerdpoeducationalelearningencryptionendpoint protectionenterprise mobility managementfile encryptionformazione a distanzafull disk encryptionGdprIT Securitymobile device managementpar-tecprivacy complianceprotezione dei datiRansomwareregolamento europeoSecuritysicurezzasicurezza dei datisophossophos intercept xsophos mobile controlsophos safeguard enterprisethreat management


Scale MySQL beyond limits with ProxySQL
2019alertingArchitectureautomatebountybugcertificateclouddefenseDevopsDevSecOpsDistributedElixirencryptionengineeringfeedbackfunctionalhasgeekKafkakeylogmanagementmanagermonitoringOLAPOLTPOnionOpenopenscapOSINTpolarDBprogrammingpythonreliabilityremoterootconfroutingSecurityServersourceSRESSHstreamsSystemTorVitessWireshark
Recent Posts
- Azure AI Insights: Understanding the Core Principles of AI-900(Part 2)
- David Chou & Derrick Pledger, Leidos | AWS re:Invent 2021
- The Collective Project Setting A World Record
- DevOps & SysAdmins: AWS EC2 CPU Utilization vs PHP Performance – Autoscaling CPU Thresholds?
- Virtual Machine Configuration with Hyper-V Server 2012 R2
