Tag Archives: cryptography

Cryptography and Cyber Security || Full Course
block ciphersblockcypherblockcypher tutorialcryptographycryptography basicscryptography tutorialcyber securitycyber security careerCyber Security Coursecyber security training for beginnersDESdes exampledes example (encryption + decryption)des example in cryptographyDigital Certificatesencryptionencryption explainednumbers theoryopensslpasswordspublic keyPublic-key Cryptographyrsarsa algorithmrsa key generationSecuritystream cyphers
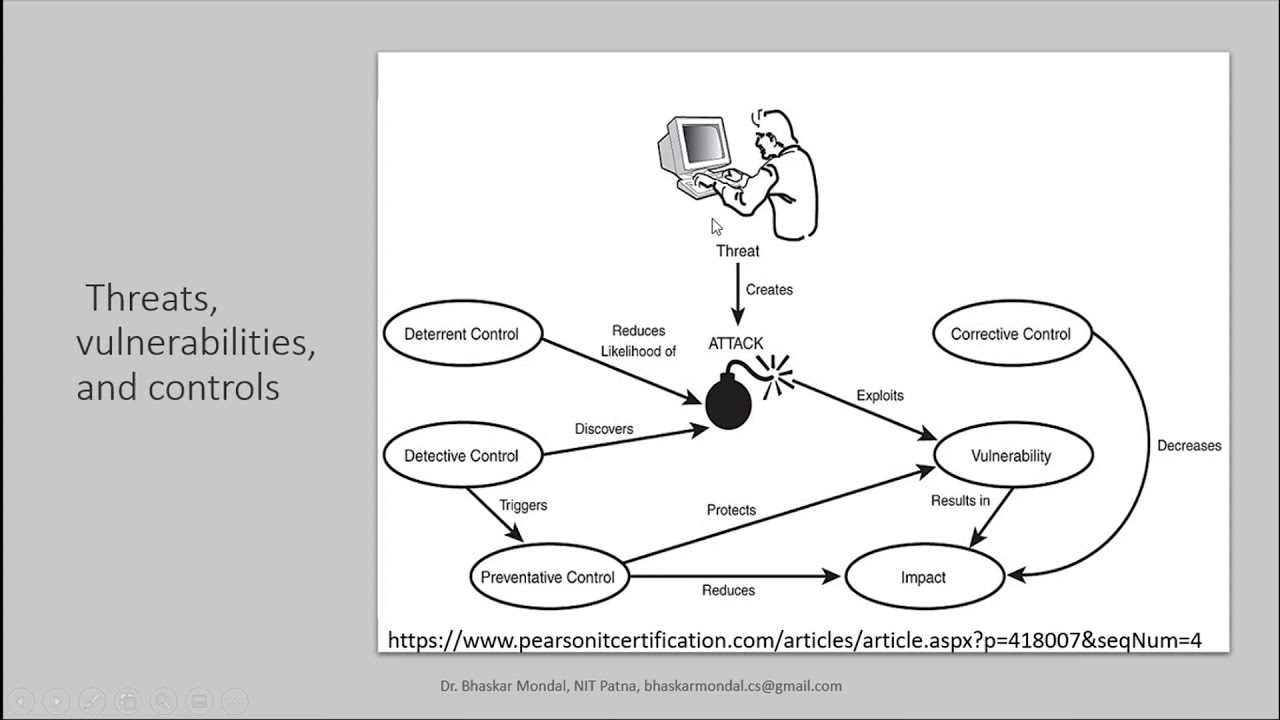
Threats, vulnerabilities, and controls in Information Security
Access ControlAESAIassignmentcode for beginners tutorialcomputecrypto systemcryptographycyber attackcyber securityDBMSdecryptiondeep learningDESdiyECCencryptionFLATguideHow toIDSinformation securityinstallintrusion detectionLATEXlearn to programlecturemachine learningMLNetwork Securityprivate keyprogrammingpublic keypythonrsascientific computingSecuritySHASQLTOCtutorial“computer laboratory” computer science GATE

Day 1 Part 2: Intro Trusted Computing
attestationAuthenticationclassesComputercomputer securitycomputer security classcryptographycyber securityCybersecuritydecryptiondigital signaturesDRTMdynamic root of trusteducationencryptionOpenSecurityTraining.infoPCRPCRsSecuritySRTMstatic root of trustTPMtrainingtrustTrusted ComputingTrusted Computing Grouptrusted hardwareTrusted Platform Module

Blockchain : Top 5 tips to secure job in Blockchain || How to really start || In Telugu(2020)
americaAndhra PradeshAngularartificial intelligencebest job marketblockchainBlockchain jobsCanadacrypto currencycryptographyCSScurrenciesdigitalDigital TransformationdynamicsEnglishhtmlIndiainformation technologyIT Jobsjob marketjobsmicroservicesmicrosoftproduct systemReactstatestechnologiesTelanganaTelugutop 5 Blockchainus
Keynote Talk on Cyber Security and Symmetric Key Encryption
Access ControlAESAIassignmentcode for beginners tutorialcomputecrypto systemcryptographycyber attackcyber securityDBMSdecryptiondeep learningDESdiyECCencryptionFLATguideHow toIDSinformation securityinstallintrusion detectionLATEXlearn to programlecturemachine learningMLNetwork Securityprivate keyprogrammingpublic keypythonrsascientific computingSecuritySHASQLTOCtutorial“computer laboratory” computer science GATE


Bitcoin Q&A: Incentivised cybersecurity & decentralization
andreas antonopoulosandreas antonopoulos bitcoinandreas antonopoulos blockchainandreas antonopoulos cryptocurrencyandreas m antonopoulosbitcoinbitcoin educationbitcoin newsbitcoin technologybitcoin technology educationblockchainblockchain educationblockchain walletcryptocurrencycryptocurrency educationcryptographyfinanceglobal economyhard moneyNetworksopen blockchainopen blockchain educationopen blockchain technologySecurity
Recent Posts
- Virtual Machine Configuration with Hyper-V Server 2012 R2
- Clojure cron job with AWS Lambda – Singapore Clojure Meetup
- Databricks DButils:How to mount/unmount AWS S3 bucket in DBFS (dbutils fs) #s3bucket #databricks
- What is the maximum number of security groups per EC2 instance?#shorts #viralshort #aws #awsservices
- 10 AWS S3 Part1
