Tag Archives: System
Automate your IX’s RS Config
2019alertingArchitectureautomatebountybugcertificateclouddefenseDevopsDevSecOpsDistributedElixirencryptionengineeringfeedbackfunctionalhasgeekKafkakeylogmanagementmanagermonitoringOLAPOLTPOnionOpenopenscapOSINTpolarDBprogrammingpythonreliabilityremoterootconfroutingSecurityServersourceSRESSHstreamsSystemTorVitessWireshark

Learn ASP NET Core MVC NET 6 (complete tutorial for students and reference material for teachers)
AIanalysisandroidAnimationappararduinoAugmentedbeginnerbitcoinblockchainBusinesscapstonecentralizeclassclassroomcollegecryptoCSSDatabasedataminingDBMSdecentralizedigitalgamehtmlicoinformationinformation technologiesinternetitJavajQuerylanguagemachine learningmanagementmobilemysqlnftonlinephotoshopphpprogrammingprojectpythonschoolsmart contractSQLSTUDIOsubjectSystemTechnologythesistutorialUniversityvirtualvisualvrwebsiteWindows
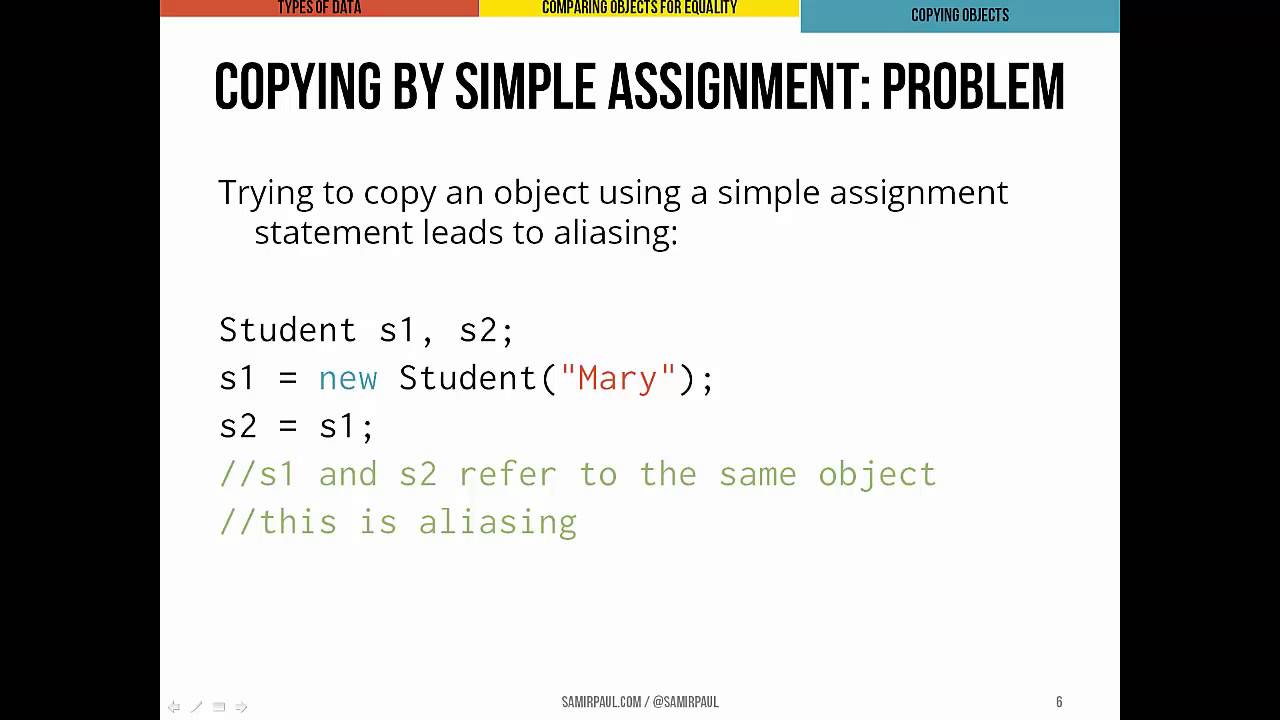
Access Tutorial in Hindi #SHORTS
Access ClassesAdviceComputerConditional FormattingdataeasyexcelExcel 2016Excel ClassesfreehandlinghelphowtoIdeasinformationInstructionlearnmanagementMicrosoft Excel (Software)Need HelpNeedsOfficePower BI ClassesprofessionalprogrammingprogramsquickSecretssoftwareSoftware TutorialSystemTableau ClassesTechniquesTechnologytipTipstrickstutorialuseUsingvalidationVBA ClassesVisual BasicWindowsyour“Advanced




Using Pod Security Policies to harden your Kubernetes cluster
2019alertingArchitectureautomatebountybugcertificatecloudclusterdefenseDevopsDevSecOpsDistributedElixirencryptionengineeringfeedbackfunctionalhasgeekKafkakeykuberneteslogmaliciousmanagementmanagermonitoringmultinetworkOLAPOLTPOnionOpenopenscapOSINTpodpolarDBPolicyprogrammingpythonreliabilityremoterootconfroutingSecurityServersourceSRESSHstreamsSystemtenantTortrafficusabilityUserVitessWireshark

Scale MySQL beyond limits with ProxySQL
2019alertingArchitectureautomatebountybugcertificateclouddefenseDevopsDevSecOpsDistributedElixirencryptionengineeringfeedbackfunctionalhasgeekKafkakeylogmanagementmanagermonitoringOLAPOLTPOnionOpenopenscapOSINTpolarDBprogrammingpythonreliabilityremoterootconfroutingSecurityServersourceSRESSHstreamsSystemTorVitessWireshark
Recent Posts
- #19 Method in Java | what is method overloading in java | Tutorials for beginners
- REST API Automation Project Setup From Scratch Using Java, Maven | Video Tutorial – 7
- [10/13] OOP Principles – Java Foundations Certification
- Print Alphabet Pattern in Java||#shorts||#shortsvideo
- CISSP 1 01 Sec Man roles & def 20230222 103658
