Tag Archives: SQL

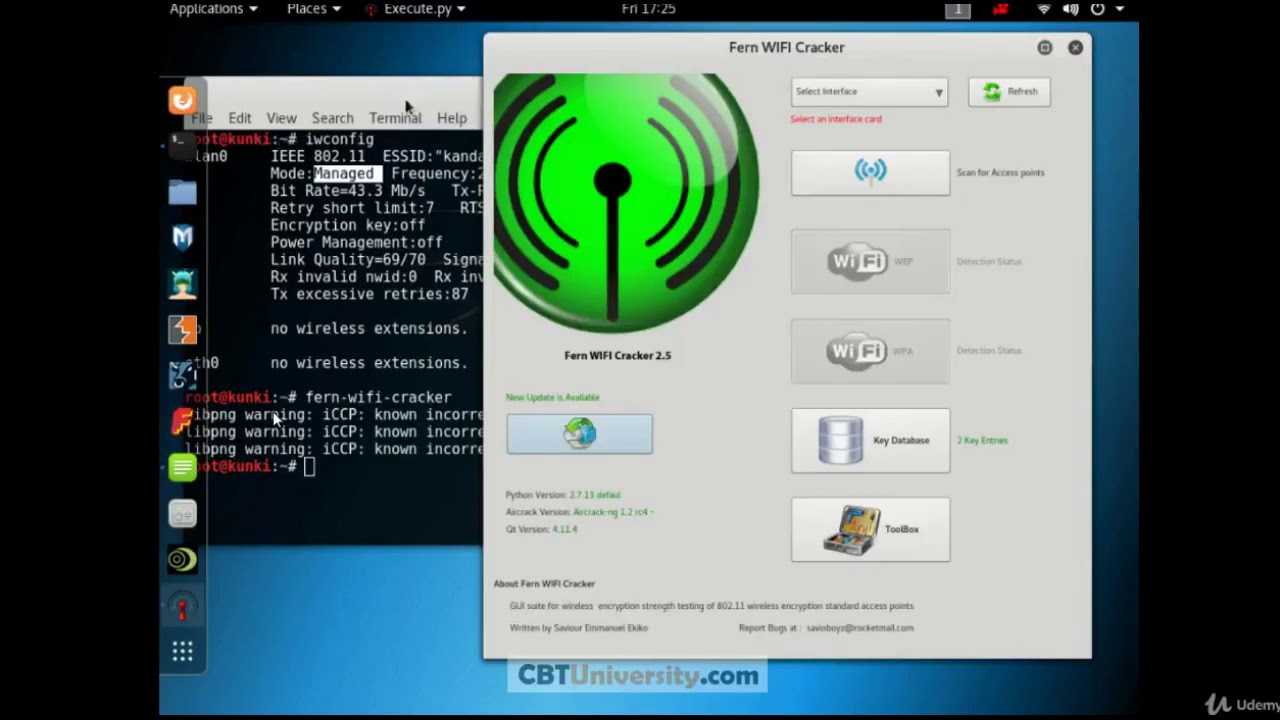
CEH 15 FERN wifi cracker
#Shells#TesteraircrackbasicsBeginnersburp suiteCompletecourseCybersecurityenumerationethicalethical hackerexpertfootprintingfreehackingHacking CourseHacking For Beginnershacking tutorialinformation securityInfosecitlearn hacking in banglamacchangermetasploitnmaponlinepass the hashpenetrationpenetration testerPentesterport scanningproxychainsreport writingreverse shellSecuritySQLtestingtrainingUdemyZero to Hero
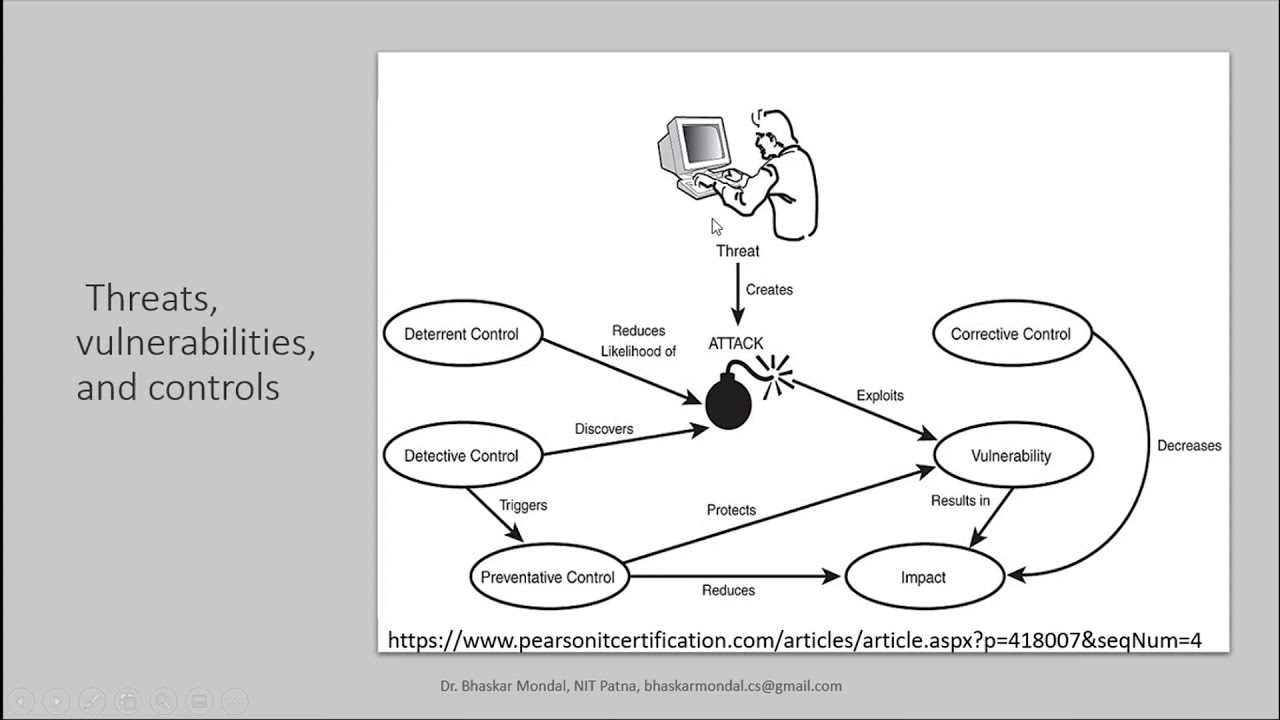
Threats, vulnerabilities, and controls in Information Security
Access ControlAESAIassignmentcode for beginners tutorialcomputecrypto systemcryptographycyber attackcyber securityDBMSdecryptiondeep learningDESdiyECCencryptionFLATguideHow toIDSinformation securityinstallintrusion detectionLATEXlearn to programlecturemachine learningMLNetwork Securityprivate keyprogrammingpublic keypythonrsascientific computingSecuritySHASQLTOCtutorial“computer laboratory” computer science GATE

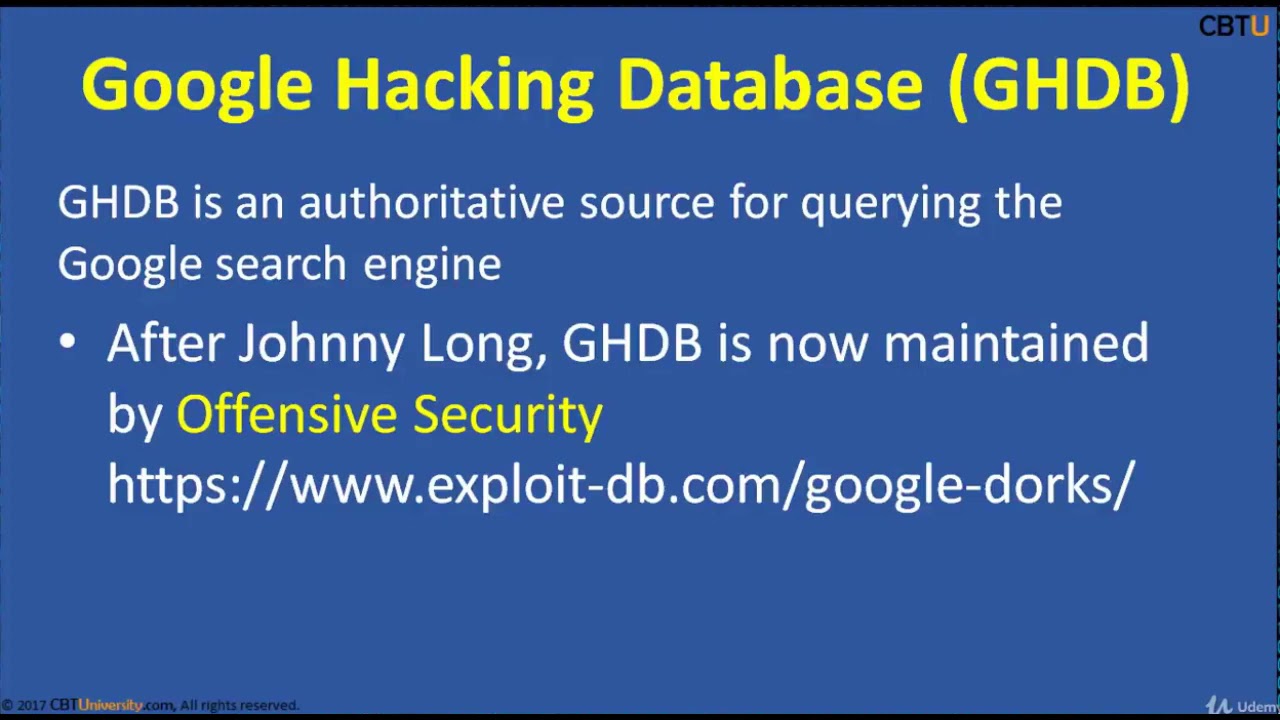
CEH2-3 Google Hacking Dorking
2015additionsaircrackbasicsBeginnersblackclicommandCompletecoursecrackcrackingenvironmentethicalexpertfootprintingforfreegreyguesthackhackerHacker (Interest)hackershackingHackshathdinstallinterfaceitKalikeylearn hacking in banglalineLinuxliveloggersmacchangernetworknmaponlinepenetrationprivateproxychainsreaverSecurityskillsSQLtermstestingtrainingUdemyvirtualvirtualboxVirtualBox (Software)vpnvpswhitewifiWindowswpawpa2
Recent Posts
- Jsp directives | Directive tags in Jsp | hindi | Servlet #30
- Java Programming for Beginners – Part 2 | Loops, Collections & Final Project | Complete Java Course
- LifeCycle of Servlet in Hindi – Servlet & JSP #7
- Are we making our engineers blue? TASH NORRIS
- What is ISO ? ISO-9001, ISO-14001, ISO-45001- IMS
