Tag Archives: SHA
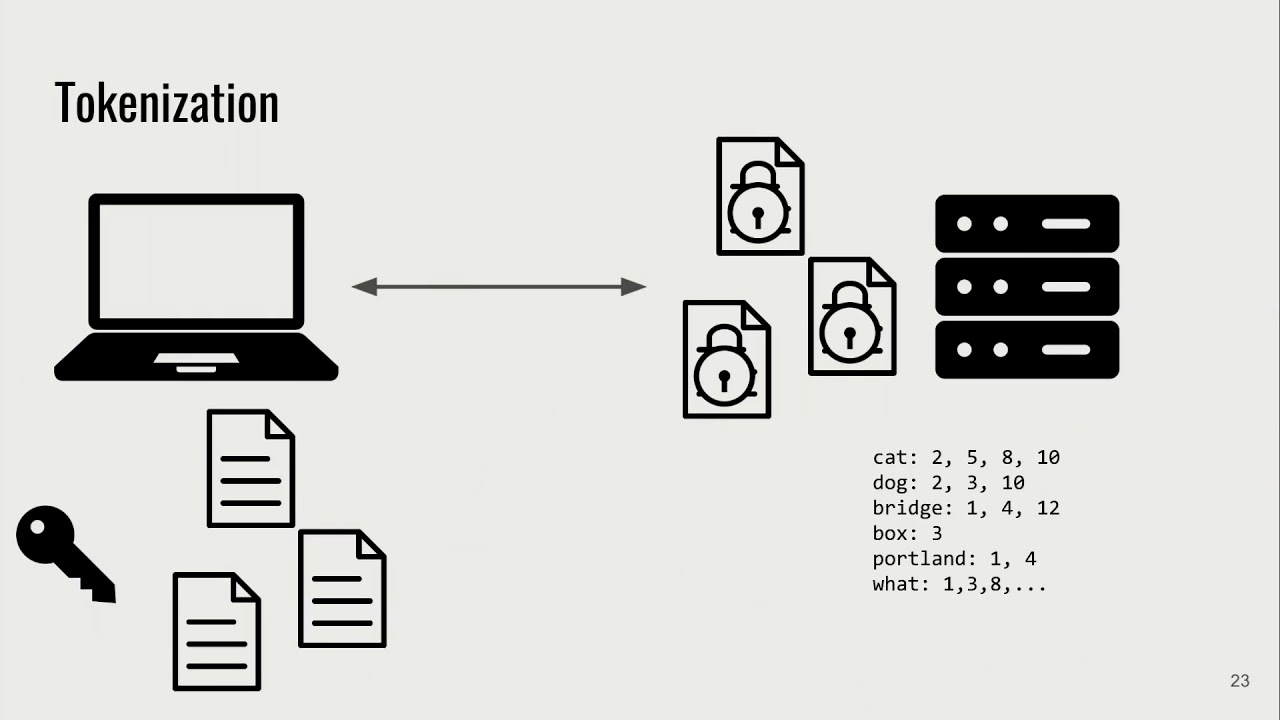
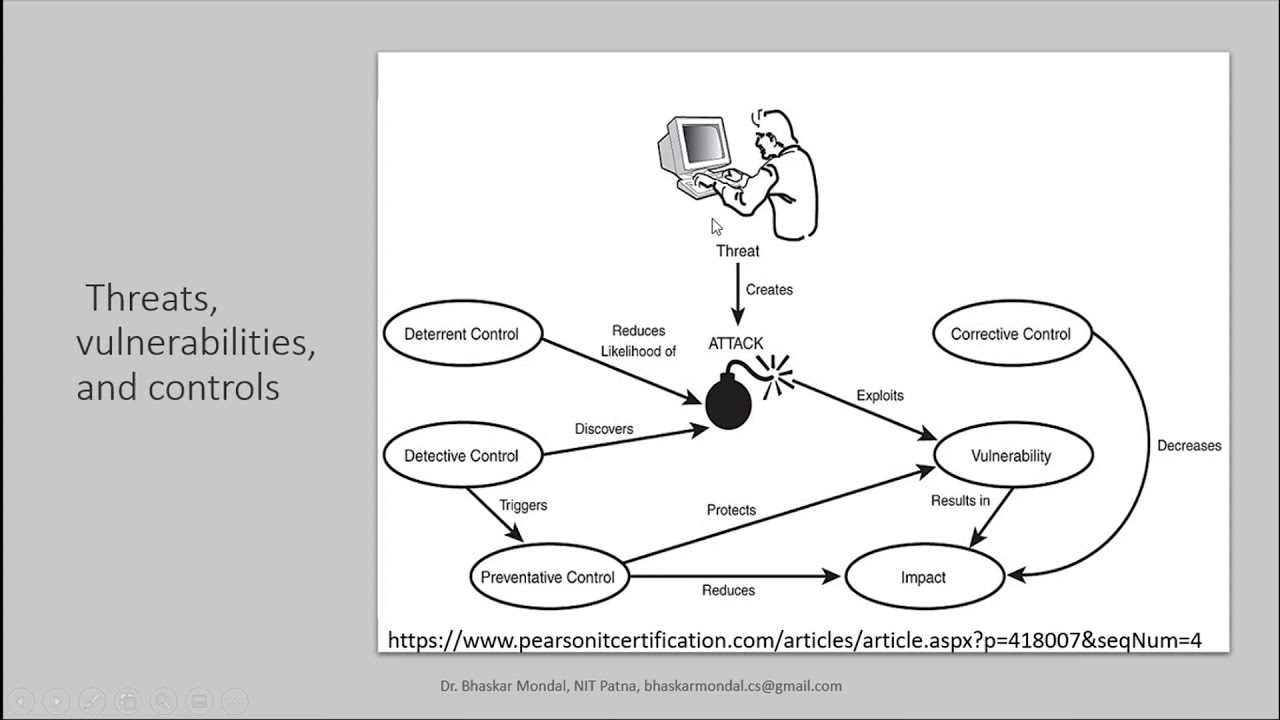
Threats, vulnerabilities, and controls in Information Security
Access ControlAESAIassignmentcode for beginners tutorialcomputecrypto systemcryptographycyber attackcyber securityDBMSdecryptiondeep learningDESdiyECCencryptionFLATguideHow toIDSinformation securityinstallintrusion detectionLATEXlearn to programlecturemachine learningMLNetwork Securityprivate keyprogrammingpublic keypythonrsascientific computingSecuritySHASQLTOCtutorial“computer laboratory” computer science GATE
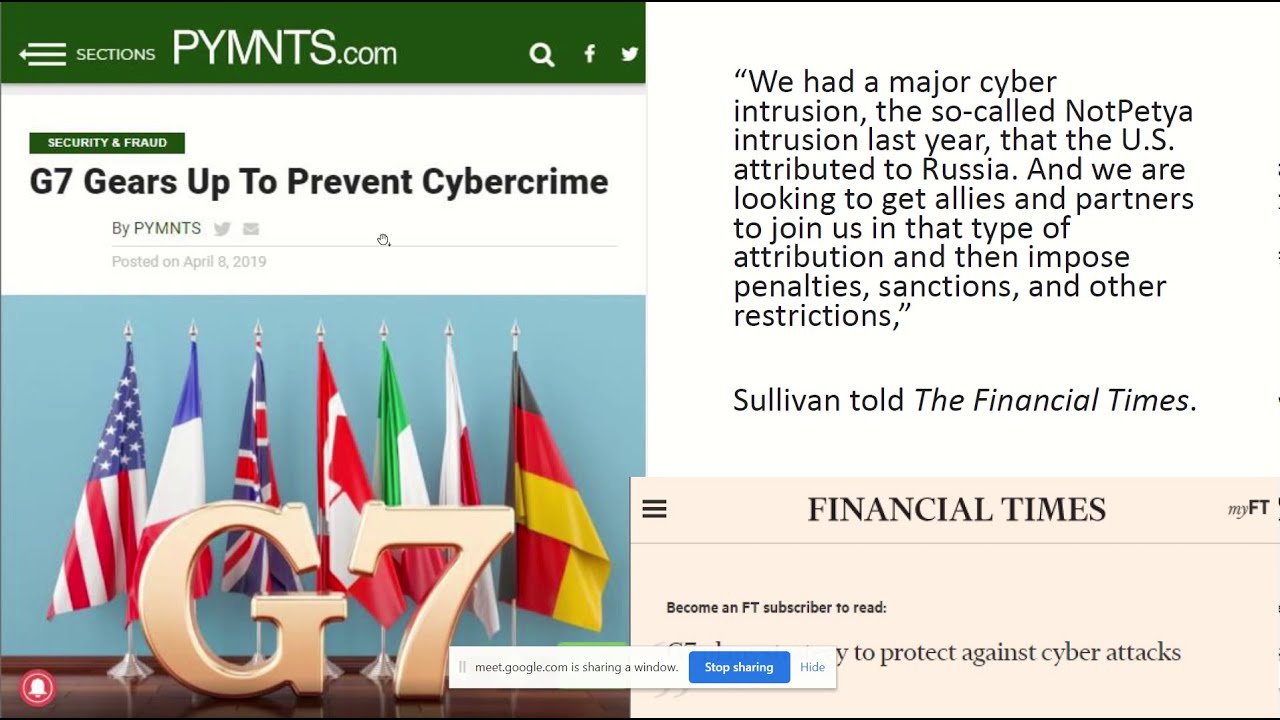
Keynote Talk on Cyber Security and Symmetric Key Encryption
Access ControlAESAIassignmentcode for beginners tutorialcomputecrypto systemcryptographycyber attackcyber securityDBMSdecryptiondeep learningDESdiyECCencryptionFLATguideHow toIDSinformation securityinstallintrusion detectionLATEXlearn to programlecturemachine learningMLNetwork Securityprivate keyprogrammingpublic keypythonrsascientific computingSecuritySHASQLTOCtutorial“computer laboratory” computer science GATE
Recent Posts
- Local Group Policy in Windows 7 – Roll back to default settings? (5 Solutions!!)
- DevOps & SysAdmins: How to configure auto-logon in Active Directory?
- DevOps & SysAdmins: How to configure windows group policy to limit browsing? (5 Solutions!!)
- Learn Live Implement hybrid identity with Windows Server
- DevOps & SysAdmins: Use of SSL in ADFS
