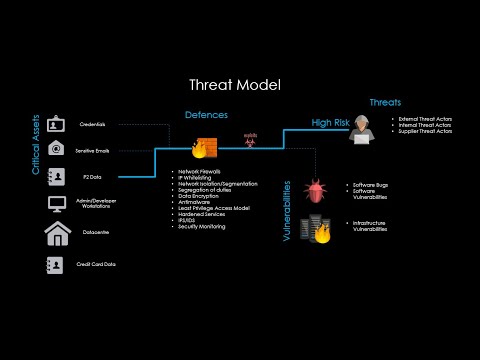
Tag Archives: rsa

Cryptography and Cyber Security || Full Course
block ciphersblockcypherblockcypher tutorialcryptographycryptography basicscryptography tutorialcyber securitycyber security careerCyber Security Coursecyber security training for beginnersDESdes exampledes example (encryption + decryption)des example in cryptographyDigital Certificatesencryptionencryption explainednumbers theoryopensslpasswordspublic keyPublic-key Cryptographyrsarsa algorithmrsa key generationSecuritystream cyphers
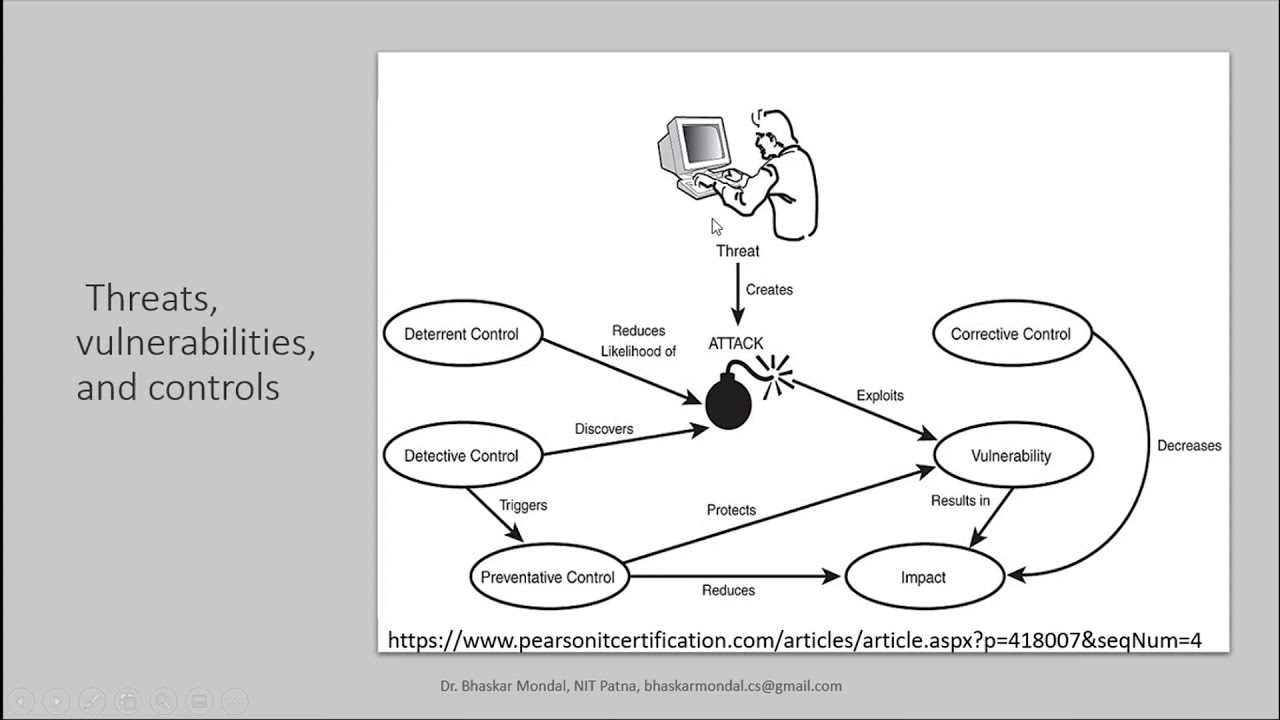
Threats, vulnerabilities, and controls in Information Security
Access ControlAESAIassignmentcode for beginners tutorialcomputecrypto systemcryptographycyber attackcyber securityDBMSdecryptiondeep learningDESdiyECCencryptionFLATguideHow toIDSinformation securityinstallintrusion detectionLATEXlearn to programlecturemachine learningMLNetwork Securityprivate keyprogrammingpublic keypythonrsascientific computingSecuritySHASQLTOCtutorial“computer laboratory” computer science GATE

Security Operations Center Training (SOC | SIEM) – The Hacktivists
arcsightAT&Tauditingblueteamcyber securityCybersecurityelearnsecurityevent managementExabeamfortinethackershoneypotIBM QRadarIncident responceinformation securityInfosecLogRhythmmalicious trafficmalware analysisMcAfeeMcAfee ESMMicro Focusoffensive securityoscpPentesterQRADARRapid7redteamrsaSecurity informationSecurity information and event managementSecuronixSIEMSIEM SolutionSOCSplunkspoofingTHREAT HUNTINGtrainingvulnerabilities
IOHK | Cardano whiteboard; Kaleidoscope, Dr Bernardo David.
ADAADA coinAggelosBernardo DavidbitcoinCardanoCardano HubCardano ProtocolCardano ReviewCardano whiteboardCardano whitepaperCharles Hoskinsonconsensus mechanismsCrypto 17DaedalusetcInput OutputIOHKJeremy WoodKaleidoscopeMax KeiserMental PokerNeil DavisNIPoPoWsOuroborosPeter GaziPNSolReal World CryptoRINARoyalersaSecure GamblingSidechainsTokyo Institute of TechnologyUniversally Composable
Keynote Talk on Cyber Security and Symmetric Key Encryption
Access ControlAESAIassignmentcode for beginners tutorialcomputecrypto systemcryptographycyber attackcyber securityDBMSdecryptiondeep learningDESdiyECCencryptionFLATguideHow toIDSinformation securityinstallintrusion detectionLATEXlearn to programlecturemachine learningMLNetwork Securityprivate keyprogrammingpublic keypythonrsascientific computingSecuritySHASQLTOCtutorial“computer laboratory” computer science GATE