Tag Archives: Rootkits

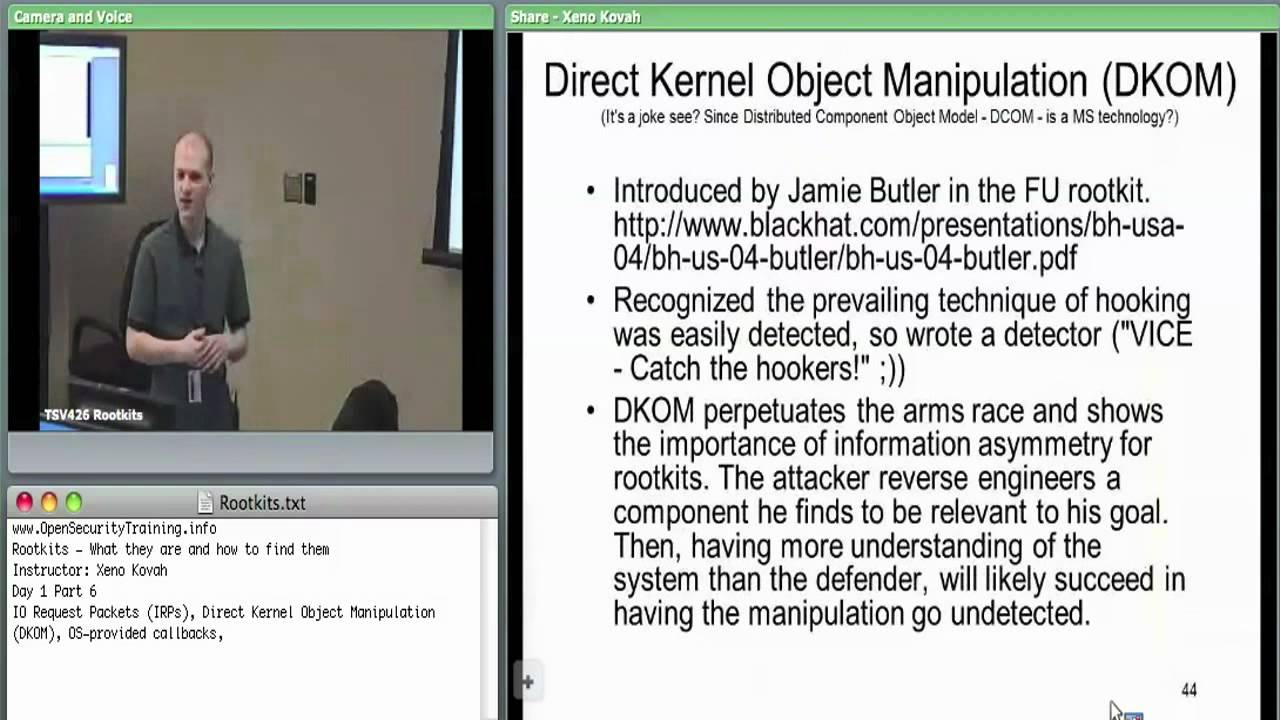
Day 1 Part 6: Rootkits: What they are, and how to find them
bootkitsclassescomputer securitycomputer security classcyber securityDKOMeducationhookingHost SecurityIAT hookingIDT hookinginline hooksIRP hookingKOHmalwaremalware detectionmulti-day-classmulti-day-trainingOpenSecurityTraining.inforootkit detectionRootkitsSSDT hookingstealth malwaretrainingWindows rootkitsx86 assembly
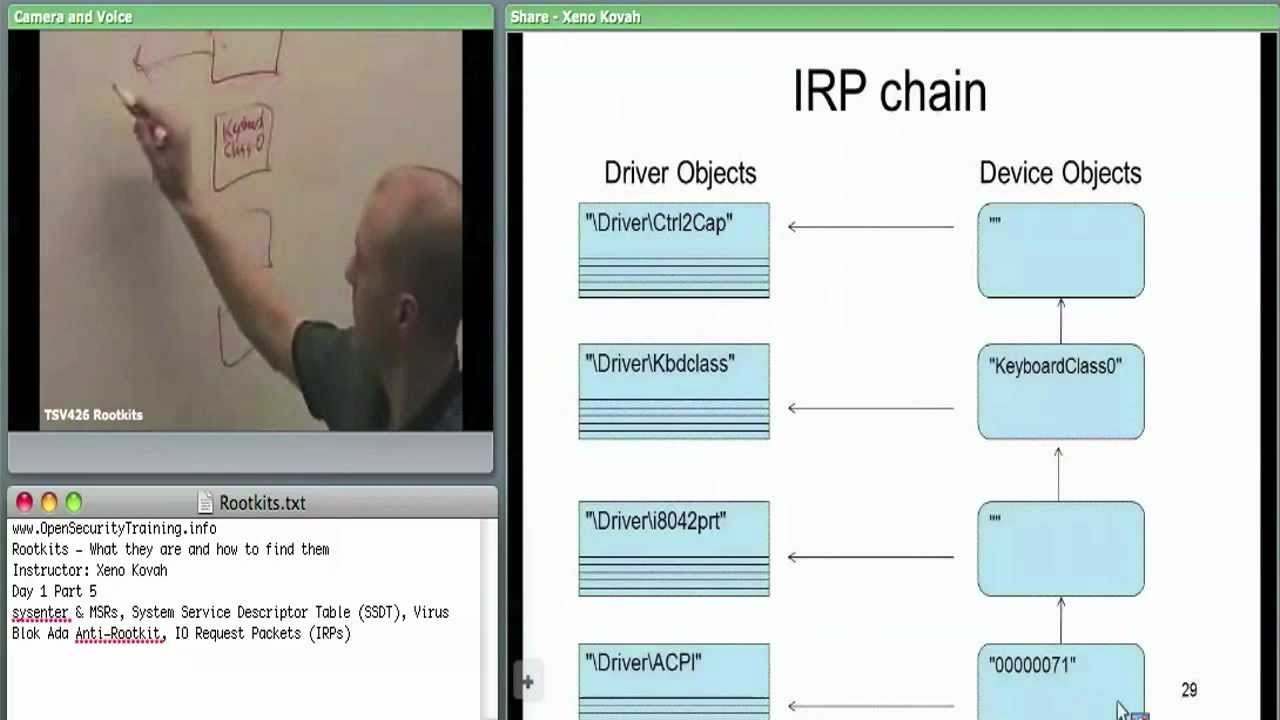
Day 1 Part 5: Rootkits: What they are, and how to find them
bootkitsclassescomputer securitycomputer security classcyber securityDKOMeducationhookingHost SecurityIAT hookingIDT hookinginline hooksIRP hookingKOHmalwaremalware detectionmulti-day-classmulti-day-trainingOpenSecurityTraining.inforootkit detectionRootkitsSSDT hookingstealth malwaretrainingWindows rootkitsx86 assembly
Recent Posts
- Windows HostProcess Containers For Configuration And Beyond – James Sturtevant & Mark Rossetti
- Dapr’s Road Ahead: GenAI APIs, Distributed Scheduling at Scale and What It Means for… Y. Schneider
- Akamai Regains Control Over Their Cloud
- Building portable cloud applications with Quarkus, Azure Radius, Skupper, and Backstage
- 2 Hour Data Analyst Interview Masterclass | Interview Better Than The Competition
