Tag Archives: rootkit detection
Day 1 Part 6: Rootkits: What they are, and how to find them
bootkitsclassescomputer securitycomputer security classcyber securityDKOMeducationhookingHost SecurityIAT hookingIDT hookinginline hooksIRP hookingKOHmalwaremalware detectionmulti-day-classmulti-day-trainingOpenSecurityTraining.inforootkit detectionRootkitsSSDT hookingstealth malwaretrainingWindows rootkitsx86 assembly
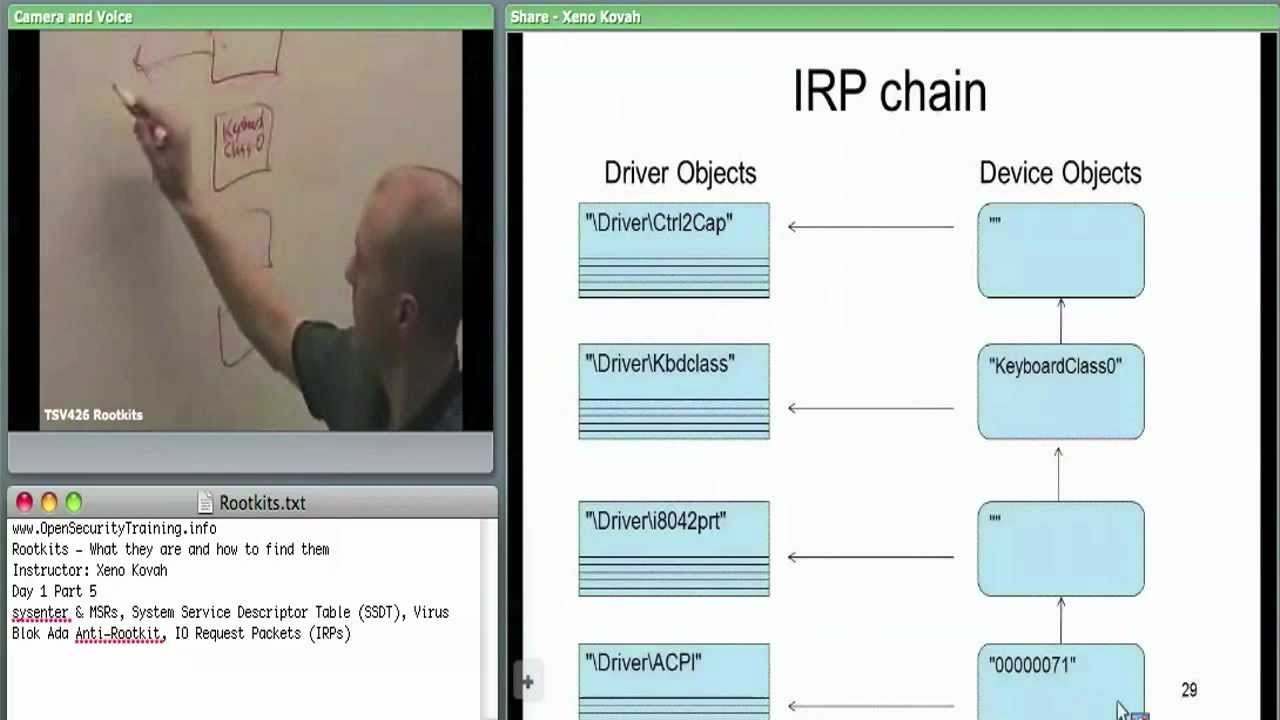
Day 1 Part 5: Rootkits: What they are, and how to find them
bootkitsclassescomputer securitycomputer security classcyber securityDKOMeducationhookingHost SecurityIAT hookingIDT hookinginline hooksIRP hookingKOHmalwaremalware detectionmulti-day-classmulti-day-trainingOpenSecurityTraining.inforootkit detectionRootkitsSSDT hookingstealth malwaretrainingWindows rootkitsx86 assembly
Recent Posts
- How to Become a Great Software Developer — Best Advice from Top-Notch Engineers
- Using FIDO for Multifactor authentication with WSO2 Identity Server #Identityin15
- Proof of possession for OAuth2 tokens(DPoP) with WSO2 Identity Server #Identityin15
- Lecture 2021 Numerical Methods: 37: Numerical Approximation of Partial Derivatives (3)
- Log Management with Monasca
