Tag Archives: public key

Basics of Cryptography
artAugurBinancebitcoinBitSharesblockblockchainBlocknetBytesCardanoCashClassicCreditscryptocryptocurrencycryptographyCryptonexDashdtubeElectroneumEnigmaeosethereumEthosgameGoldGolemGXShareshashiconIconomiIOTALedgerlifeLiskLitecoinMoneromoneyNEOnetworkOmiseGOphotographyPIVXPowerproducerspublic keyPublic-key CryptographyQuantstampRipplescienceSiacoinsteemsteemitTechnologyTokensVeChainVERGEVertcoinZCoin

Cryptography and Cyber Security || Full Course
block ciphersblockcypherblockcypher tutorialcryptographycryptography basicscryptography tutorialcyber securitycyber security careerCyber Security Coursecyber security training for beginnersDESdes exampledes example (encryption + decryption)des example in cryptographyDigital Certificatesencryptionencryption explainednumbers theoryopensslpasswordspublic keyPublic-key Cryptographyrsarsa algorithmrsa key generationSecuritystream cyphers
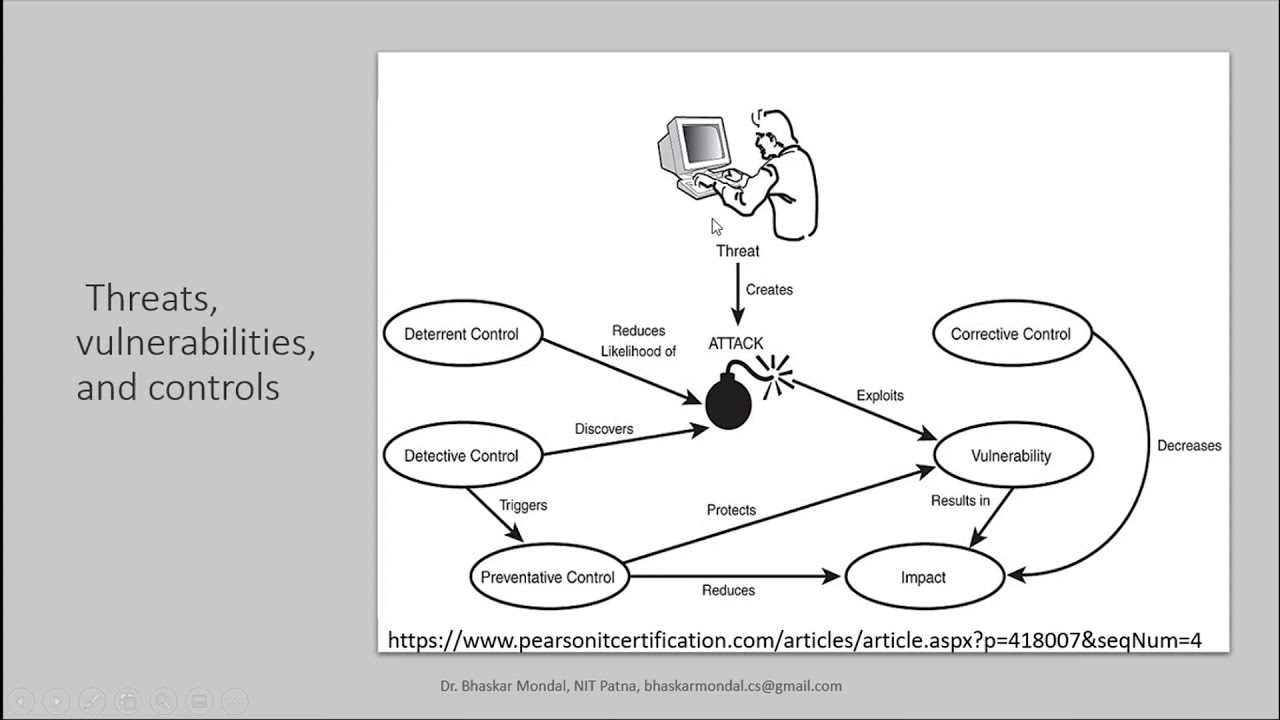
Threats, vulnerabilities, and controls in Information Security
Access ControlAESAIassignmentcode for beginners tutorialcomputecrypto systemcryptographycyber attackcyber securityDBMSdecryptiondeep learningDESdiyECCencryptionFLATguideHow toIDSinformation securityinstallintrusion detectionLATEXlearn to programlecturemachine learningMLNetwork Securityprivate keyprogrammingpublic keypythonrsascientific computingSecuritySHASQLTOCtutorial“computer laboratory” computer science GATE
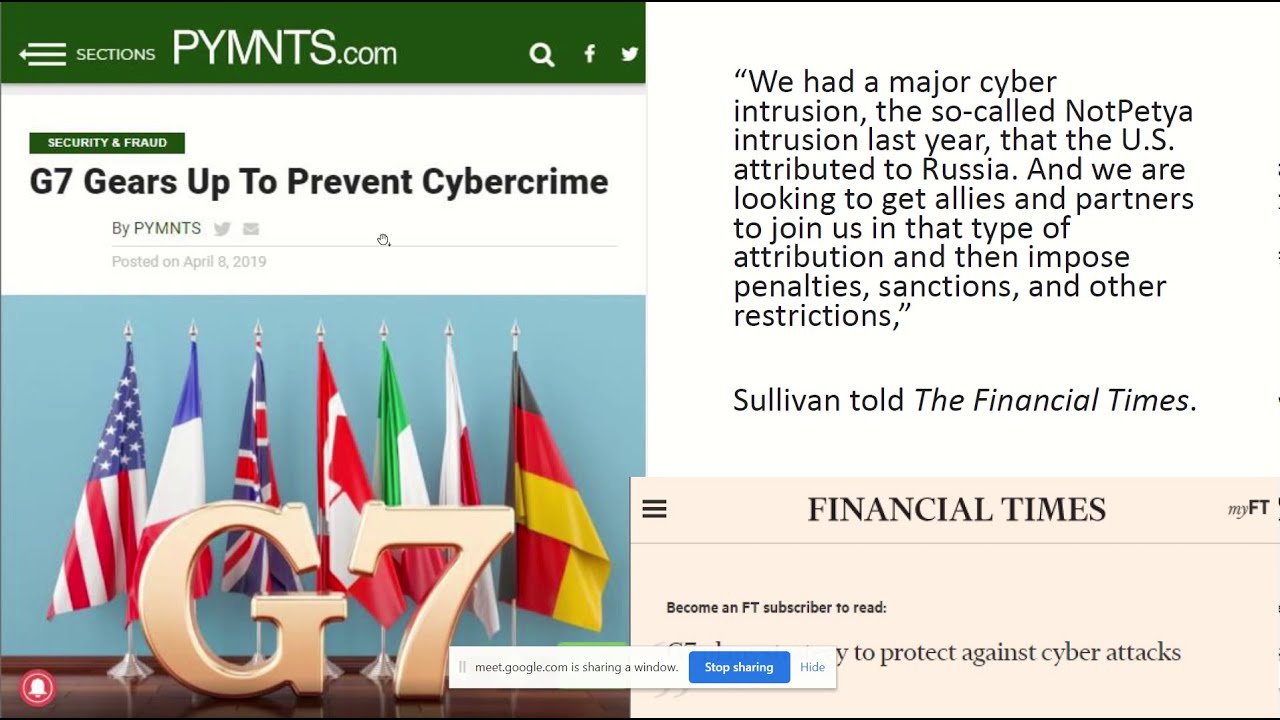
Keynote Talk on Cyber Security and Symmetric Key Encryption
Access ControlAESAIassignmentcode for beginners tutorialcomputecrypto systemcryptographycyber attackcyber securityDBMSdecryptiondeep learningDESdiyECCencryptionFLATguideHow toIDSinformation securityinstallintrusion detectionLATEXlearn to programlecturemachine learningMLNetwork Securityprivate keyprogrammingpublic keypythonrsascientific computingSecuritySHASQLTOCtutorial“computer laboratory” computer science GATE
Recent Posts
- Difference between Clustered Columnstore Index Table in Azure SQL and Table in Azure Data Warehouse
- Streamlining E2E Test Automation with Azure DevOps Build/Release Pipelines by Anand #SeleniumConf 24
- Session 3: CFAIL 2020; The Evolution of IPsec (invited talk by Steven Bellovin)
- Unix & Linux: Get common name (CN) from SSL certificate? (3 Solutions!!)
- DevOps & SysAdmins: How to update Group policy for the whole domain? (3 Solutions!!)
