Tag Archives: OpenSecurityTraining.info
Day 1 Part 6: Rootkits: What they are, and how to find them
bootkitsclassescomputer securitycomputer security classcyber securityDKOMeducationhookingHost SecurityIAT hookingIDT hookinginline hooksIRP hookingKOHmalwaremalware detectionmulti-day-classmulti-day-trainingOpenSecurityTraining.inforootkit detectionRootkitsSSDT hookingstealth malwaretrainingWindows rootkitsx86 assembly
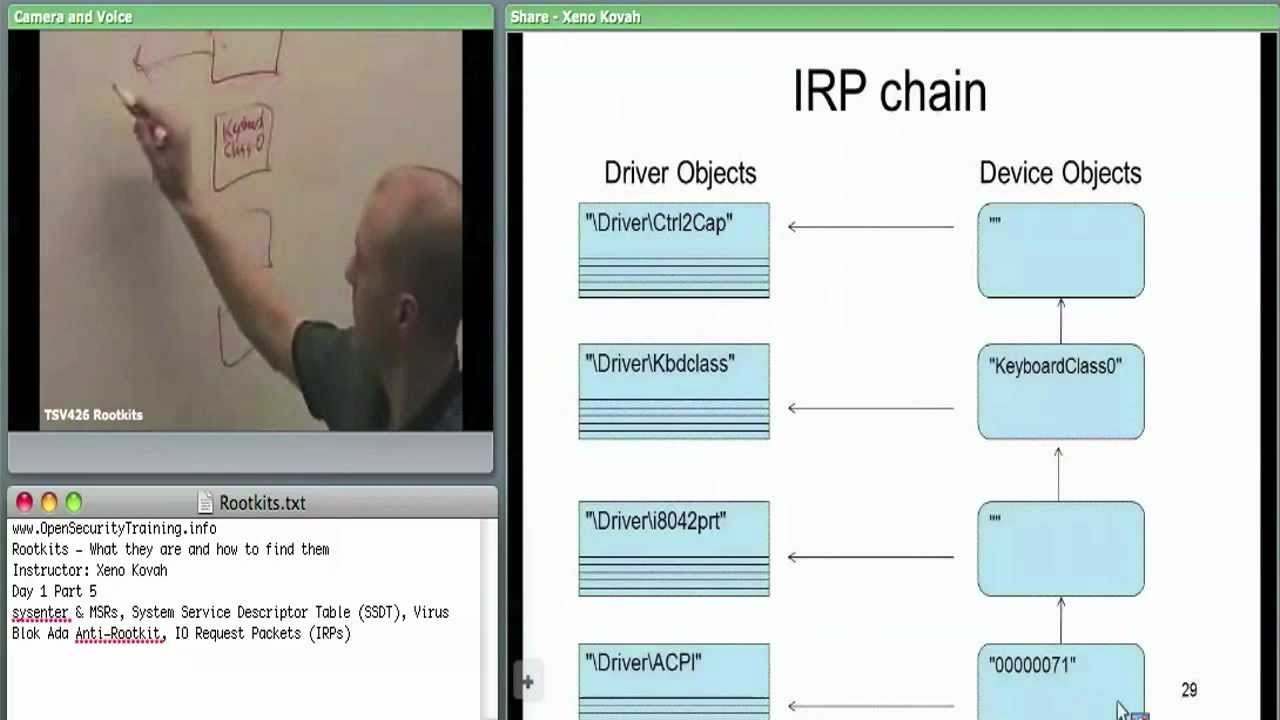
Day 1 Part 5: Rootkits: What they are, and how to find them
bootkitsclassescomputer securitycomputer security classcyber securityDKOMeducationhookingHost SecurityIAT hookingIDT hookinginline hooksIRP hookingKOHmalwaremalware detectionmulti-day-classmulti-day-trainingOpenSecurityTraining.inforootkit detectionRootkitsSSDT hookingstealth malwaretrainingWindows rootkitsx86 assembly

Day 1 Part 2: Intro Trusted Computing
attestationAuthenticationclassesComputercomputer securitycomputer security classcryptographycyber securityCybersecuritydecryptiondigital signaturesDRTMdynamic root of trusteducationencryptionOpenSecurityTraining.infoPCRPCRsSecuritySRTMstatic root of trustTPMtrainingtrustTrusted ComputingTrusted Computing Grouptrusted hardwareTrusted Platform Module
Recent Posts
- Office error: “We weren’t able to register your device and add your account to Windows.”
- #azureadministrator #azurearchitect #azuredevops Realtime training starts 30/Oct 06:30 AM IST
- DevOps & SysAdmins: Cannot run without administrator privileges
- What to do when inbox DSC Resources don’t cover your goal – Ben Gelens
- What’s New in Parallels RAS 18.1
