Tag Archives: multi-day-training
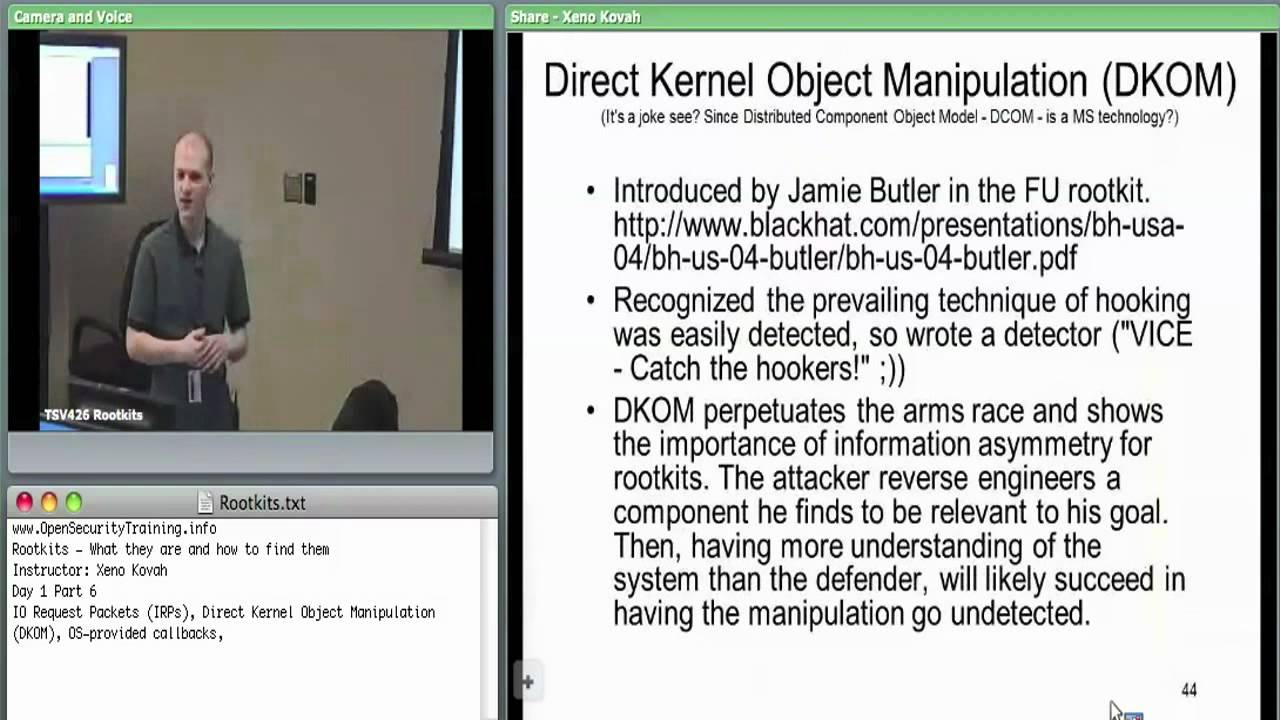
Day 1 Part 6: Rootkits: What they are, and how to find them
bootkitsclassescomputer securitycomputer security classcyber securityDKOMeducationhookingHost SecurityIAT hookingIDT hookinginline hooksIRP hookingKOHmalwaremalware detectionmulti-day-classmulti-day-trainingOpenSecurityTraining.inforootkit detectionRootkitsSSDT hookingstealth malwaretrainingWindows rootkitsx86 assembly
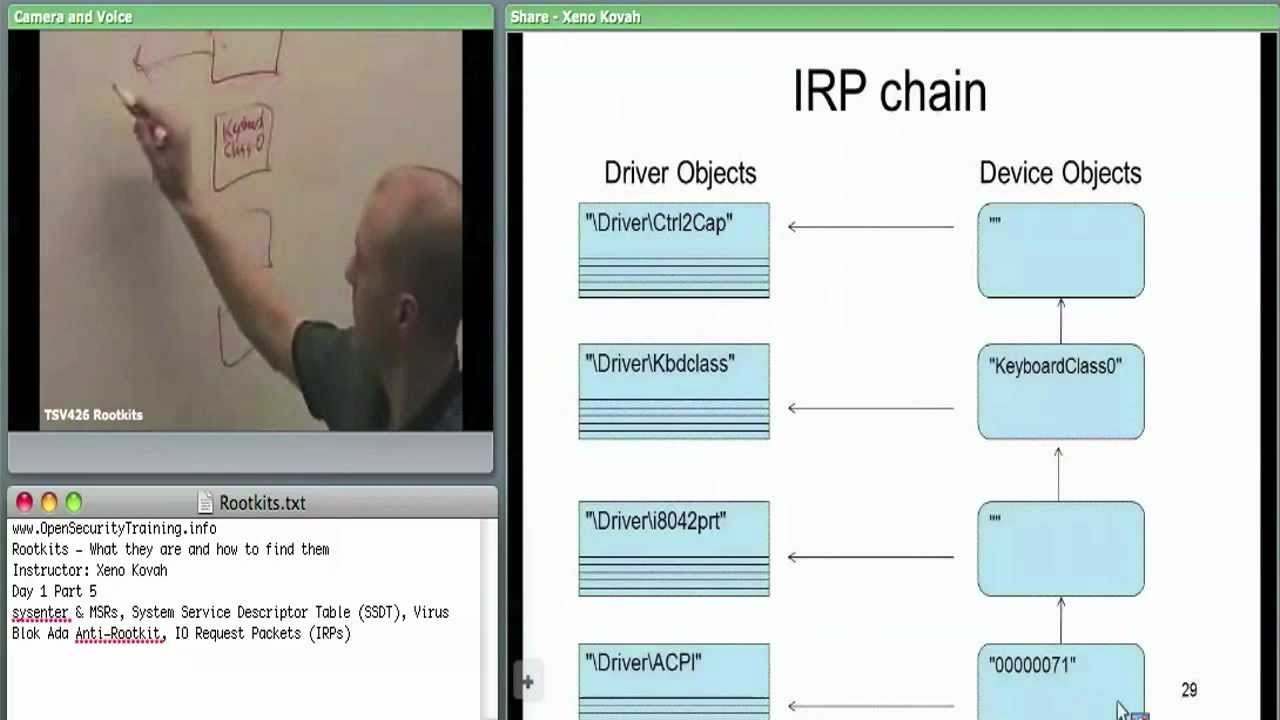
Day 1 Part 5: Rootkits: What they are, and how to find them
bootkitsclassescomputer securitycomputer security classcyber securityDKOMeducationhookingHost SecurityIAT hookingIDT hookinginline hooksIRP hookingKOHmalwaremalware detectionmulti-day-classmulti-day-trainingOpenSecurityTraining.inforootkit detectionRootkitsSSDT hookingstealth malwaretrainingWindows rootkitsx86 assembly
