Tag Archives: KOH
Day 1 Part 6: Rootkits: What they are, and how to find them
bootkitsclassescomputer securitycomputer security classcyber securityDKOMeducationhookingHost SecurityIAT hookingIDT hookinginline hooksIRP hookingKOHmalwaremalware detectionmulti-day-classmulti-day-trainingOpenSecurityTraining.inforootkit detectionRootkitsSSDT hookingstealth malwaretrainingWindows rootkitsx86 assembly
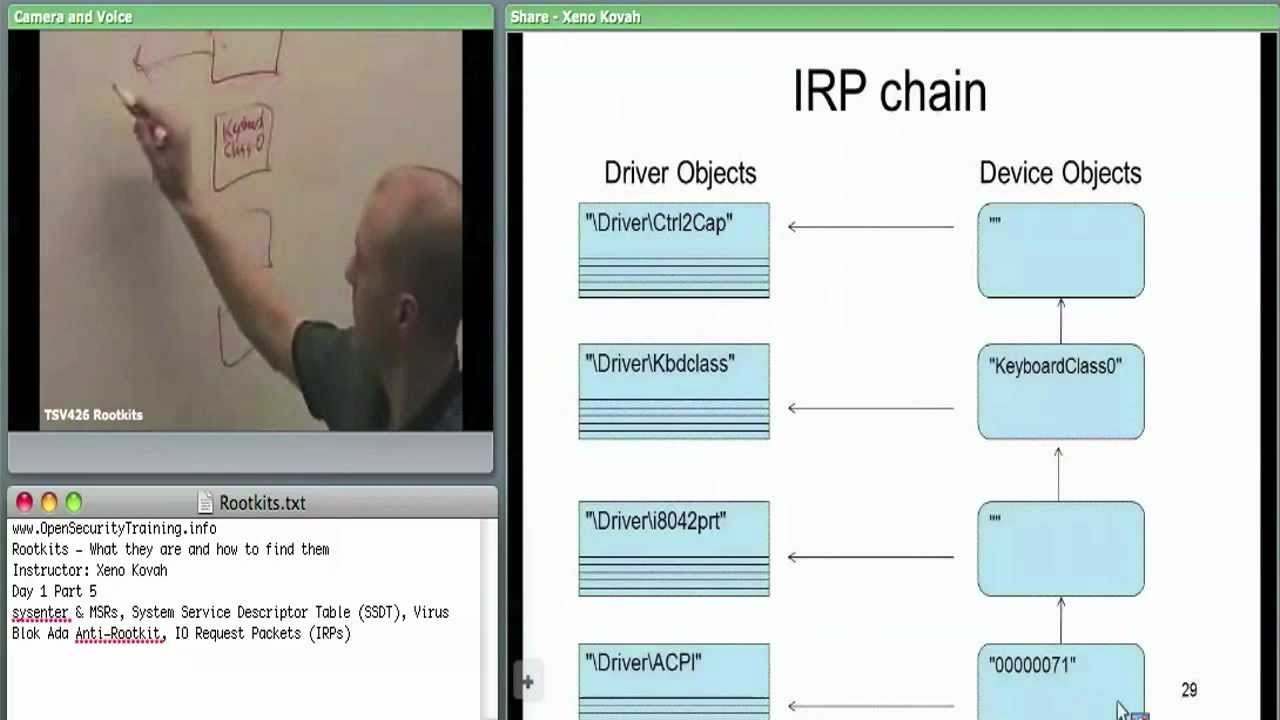
Day 1 Part 5: Rootkits: What they are, and how to find them
bootkitsclassescomputer securitycomputer security classcyber securityDKOMeducationhookingHost SecurityIAT hookingIDT hookinginline hooksIRP hookingKOHmalwaremalware detectionmulti-day-classmulti-day-trainingOpenSecurityTraining.inforootkit detectionRootkitsSSDT hookingstealth malwaretrainingWindows rootkitsx86 assembly
Recent Posts
- WSO2Con USA 2015 : End-to-end Microservice Architecture with WSO2 IS and WSO2 APIM
- SEC001: Securing Offline Web APIs with AAD
- Azure Backup Center – Governance and compliance
- DevOps & SysAdmins: Unable to enroll Device into Azure AD using 3rd Party On-Premise MDM
- Understanding azure virtual machine lab#youtube
