Tag Archives: install
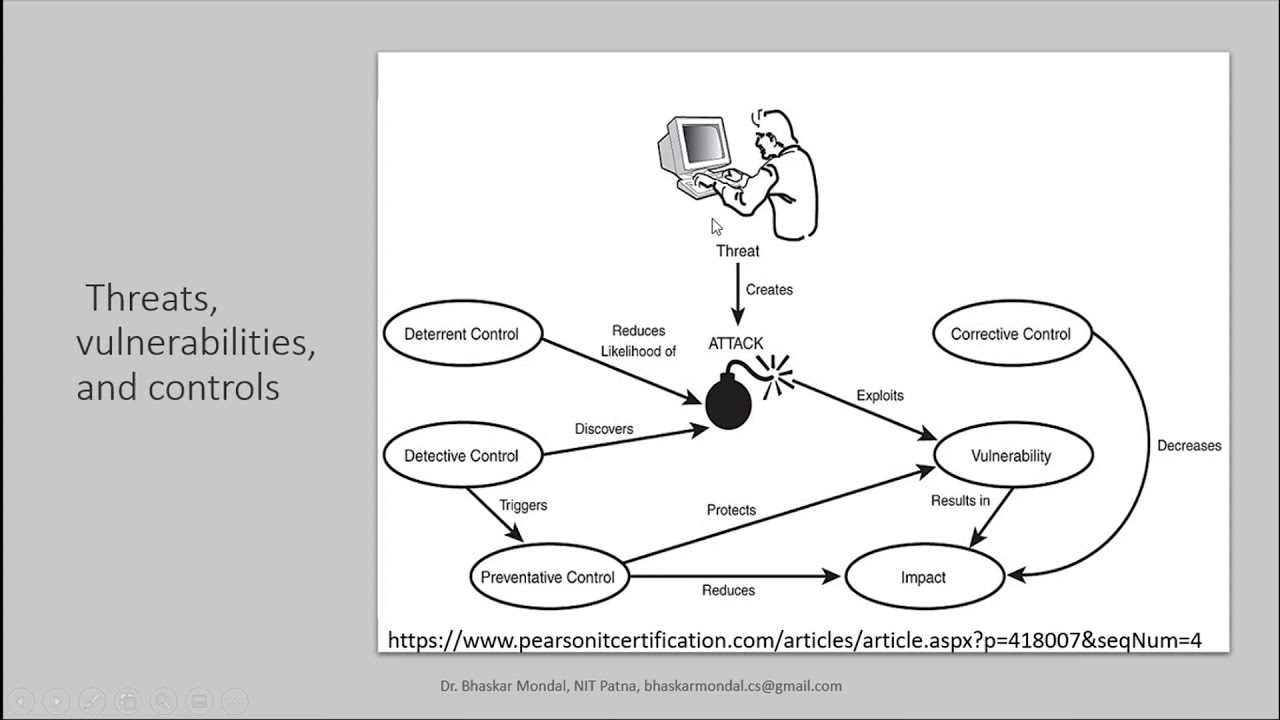
Threats, vulnerabilities, and controls in Information Security
Access ControlAESAIassignmentcode for beginners tutorialcomputecrypto systemcryptographycyber attackcyber securityDBMSdecryptiondeep learningDESdiyECCencryptionFLATguideHow toIDSinformation securityinstallintrusion detectionLATEXlearn to programlecturemachine learningMLNetwork Securityprivate keyprogrammingpublic keypythonrsascientific computingSecuritySHASQLTOCtutorial“computer laboratory” computer science GATE

CEH2-3 Google Hacking Dorking
2015additionsaircrackbasicsBeginnersblackclicommandCompletecoursecrackcrackingenvironmentethicalexpertfootprintingforfreegreyguesthackhackerHacker (Interest)hackershackingHackshathdinstallinterfaceitKalikeylearn hacking in banglalineLinuxliveloggersmacchangernetworknmaponlinepenetrationprivateproxychainsreaverSecurityskillsSQLtermstestingtrainingUdemyvirtualvirtualboxVirtualBox (Software)vpnvpswhitewifiWindowswpawpa2
Kali Linux – vid 7 – Getting Started with Kali Linux Forensics – Linux Academy
2017AcademyaircrackandroidApplicationsbackdoorbacktrackbasicsBeginnersbotnetbrutecommandComputercourseeliEnglishethicalfacebookforforcefullgamegnuhackerhackinghowtoindustryinstagraminstallitKalikdelearnLessonLinuxMacMsnMyspacepcpenpenetrationproSecurityskillsoftwaretesttestingtoolstuttutorialsupworkvideovirtualboxvmwarewifiyahooyoutube

CEH1-1 Introduction to hacking
2015additionsaircrackbasicsBeginnersblackclicommandCompletecoursecrackcrackingenvironmentethicalexpertfootprintingforfreegreyguesthackhackerHacker (Interest)hackershackingHackshathdinstallinterfaceitKalikeylearn hacking in banglalineLinuxliveloggersmacchangernetworknmaponlinepenetrationprivateproxychainsreaverSecurityskillsSQLtermstestingtrainingUdemyvirtualvirtualboxVirtualBox (Software)vpnvpswhitewifiWindowswpawpa2

Ethical Hacking | Part 2 | What is metasploit? | How to install metasploit on termux?
#ethical hacking on android#how to install metasploit on android using termux?#how to install metasploit-framework#how to install metasploit?#illustration#metasploit-framework#searchingandroidethical hackinggooglehackingHow tohow to use metasploitinstallmetasploitMetasploit projectSearch Engine OptimizationTERMUXtutorialtutorialsUCcjs0KK6V1YRqBPlo6aIpigwhite hat hackersyoutube
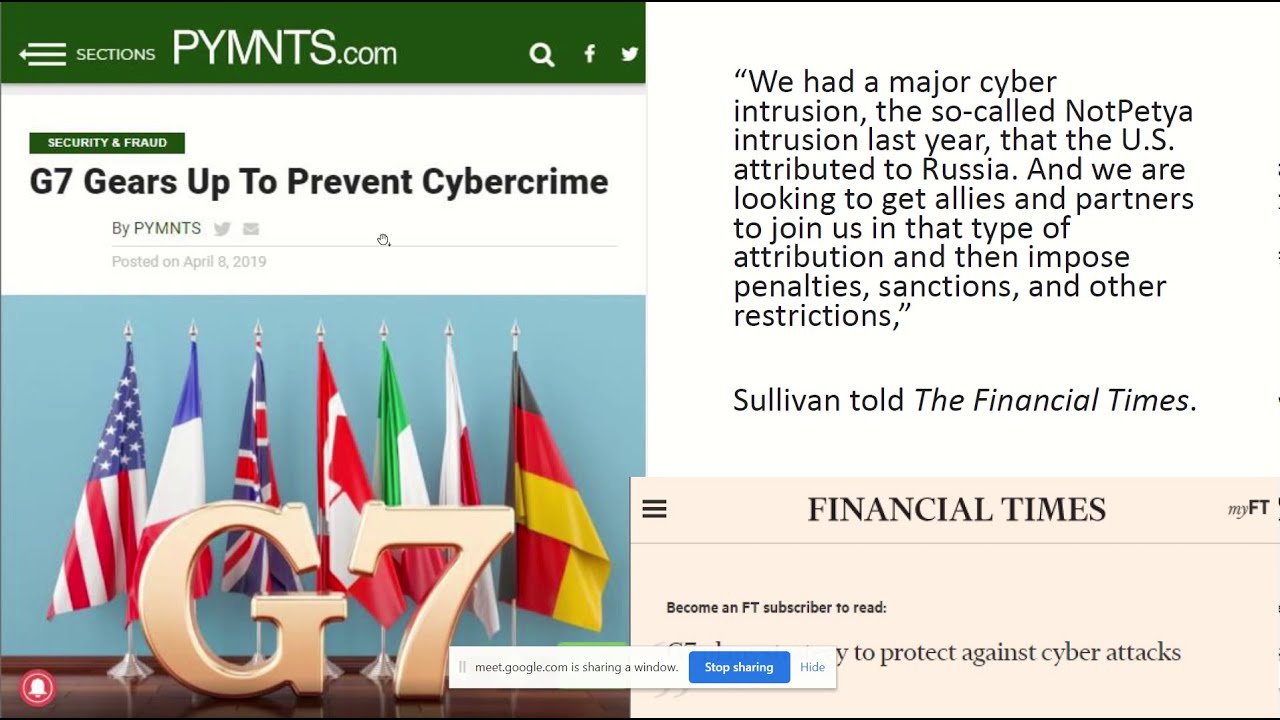
Keynote Talk on Cyber Security and Symmetric Key Encryption
Access ControlAESAIassignmentcode for beginners tutorialcomputecrypto systemcryptographycyber attackcyber securityDBMSdecryptiondeep learningDESdiyECCencryptionFLATguideHow toIDSinformation securityinstallintrusion detectionLATEXlearn to programlecturemachine learningMLNetwork Securityprivate keyprogrammingpublic keypythonrsascientific computingSecuritySHASQLTOCtutorial“computer laboratory” computer science GATE

Microsoft Azure backup & recovery for nonprofits
365andAssess”AuthenticationbackupBusinessBusiness technology servicescenter”cloudcloud migrationcommunicationcomputerscomputingcreativedatadc”deploydesigndisasterFirewall and securityInformation technology servicesinstallitIT Serviceslaptops”networknetworkingOfficePCI complianceprocure”recovery”SecurityServicesSupport“acrobat“adobe“Advanced“Consult“managed“unified

