Tag Archives: identity security

Introduction to WSO2 Identity Server 7.0 | an Overview
Access ManagementAPI authorizationAPI Securityapp authenticationapp user authorizationAsgardeoB2B capabilitiesb2b CIAMdigital identity managementEnterprise SecurityIAM solutioniam tutorialIdentity Managementidentity management tutorialidentity securityIdentity Server 7.0identity server tutorialsecurity solutionssocial login integrationWSO2 Identity ServerWSO2 tutorial
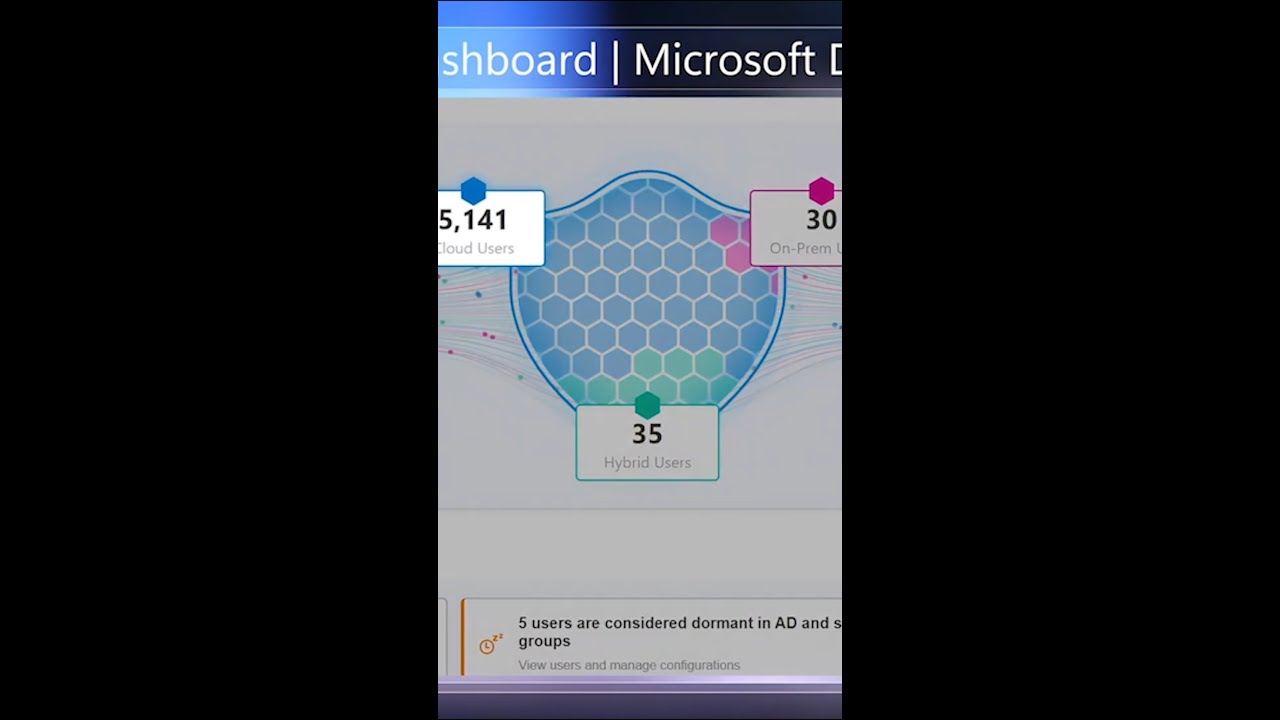
Protect against identity-based attacks.
Access ManagementActive Directoryadvanced huntingCloud SecurityConditional Access PoliciesCopilotCopilot for Securitycyber attackcyber securityIAMIdentity and Access Managementidentity based attacksIdentity Postureidentity securityIdentity threat detectionidentity threat detection and responseITDRMicrosoft Defender XDRMicrosoft EntraMicrosoft securityprivileged identitysecure score in microsoft defender for cloudthreat detectionXDR

Keynote: Take Control of Identity – Devday 2023
appAuth0cloud identitycloud identity summitCloud Securitycloud security communitycustomer identitydevdevice securityDigital Identitydigital securityidentityIdentity and Access Managementidentity governanceIdentity Managementidentity securityintelligent securityKeynoteloginnanolock securityopening keynoteping identitysecureSecuritysecurity (software)security as a servicesecurity essentialsworkforce identityzero trust security
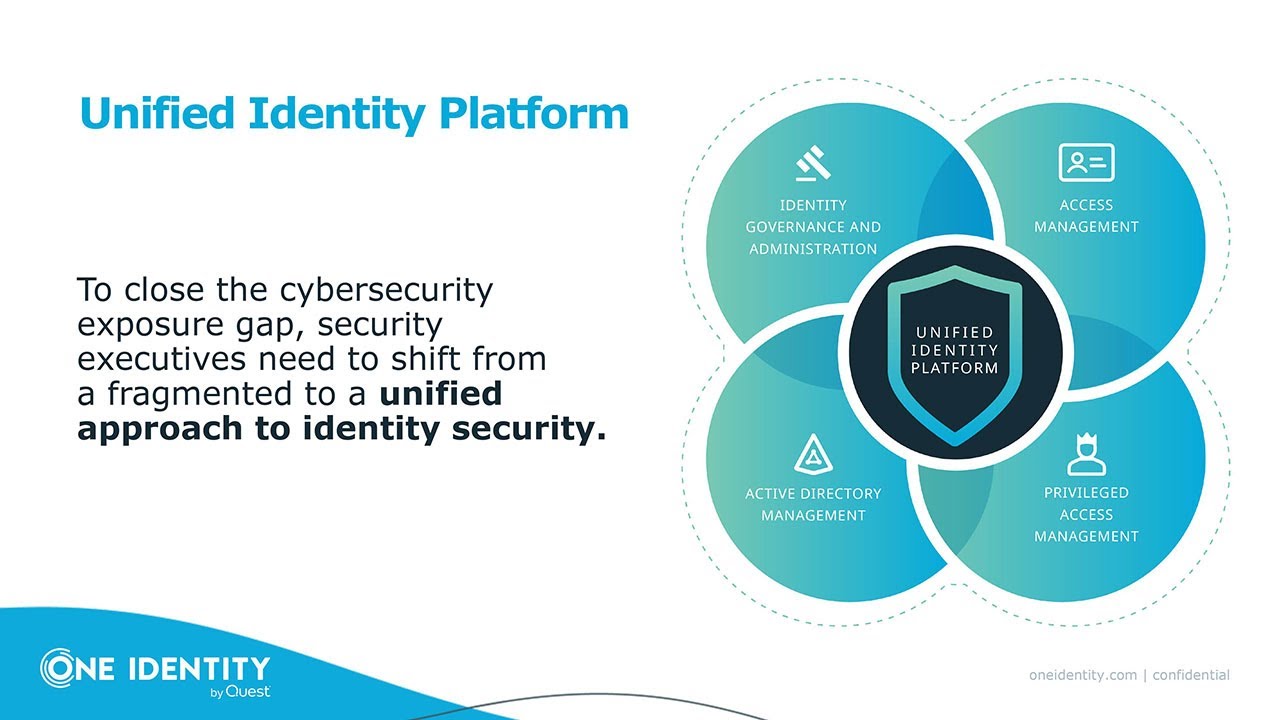
One Identity e la gestione unificata delle identità
Access Managementactive rolesamApplication Securitycloudcyber gangCybersecuritygestione unificata identitàIAMIdentity & Access Managementidentity correlationidentity governance administrationidentity securityidentity sprawligajust-in-time privilegedmassimiliano micuccimicrosoft active directory managementone identitypampar-tecprivileged access managementproliferazione identitàRansomwareSaaSsafeguardunified identity platformzero trust
Recent Posts
- IAM4NFDI quickly explained
- Steganography (1/2) BsidesCT CTF 2018
- Pentagon calls Turkish drone shot down in Syria by US forces a ‘regrettable incident’
- Sodinokibi Ransomware Encrypts Hundreds of Dental Practices via IT Provider PerCSoft.
- #19 Method in Java | what is method overloading in java | Tutorials for beginners
