Tag Archives: Host Security
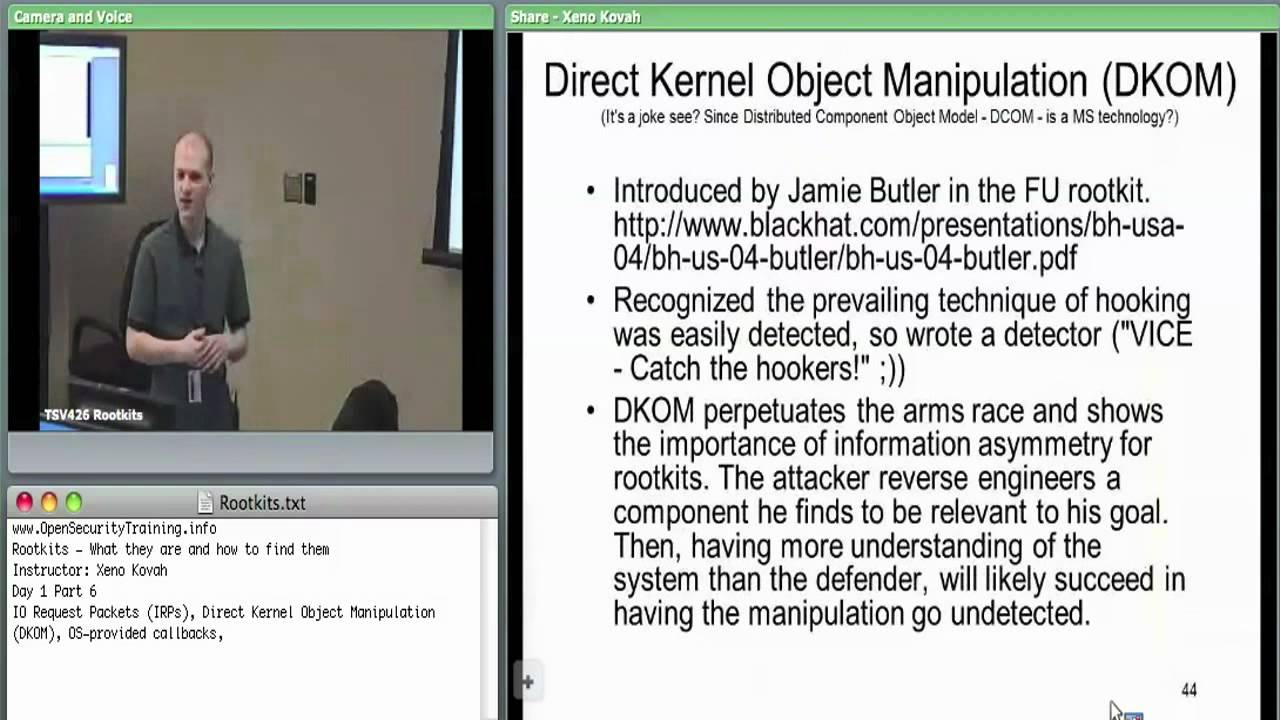
Day 1 Part 6: Rootkits: What they are, and how to find them
bootkitsclassescomputer securitycomputer security classcyber securityDKOMeducationhookingHost SecurityIAT hookingIDT hookinginline hooksIRP hookingKOHmalwaremalware detectionmulti-day-classmulti-day-trainingOpenSecurityTraining.inforootkit detectionRootkitsSSDT hookingstealth malwaretrainingWindows rootkitsx86 assembly

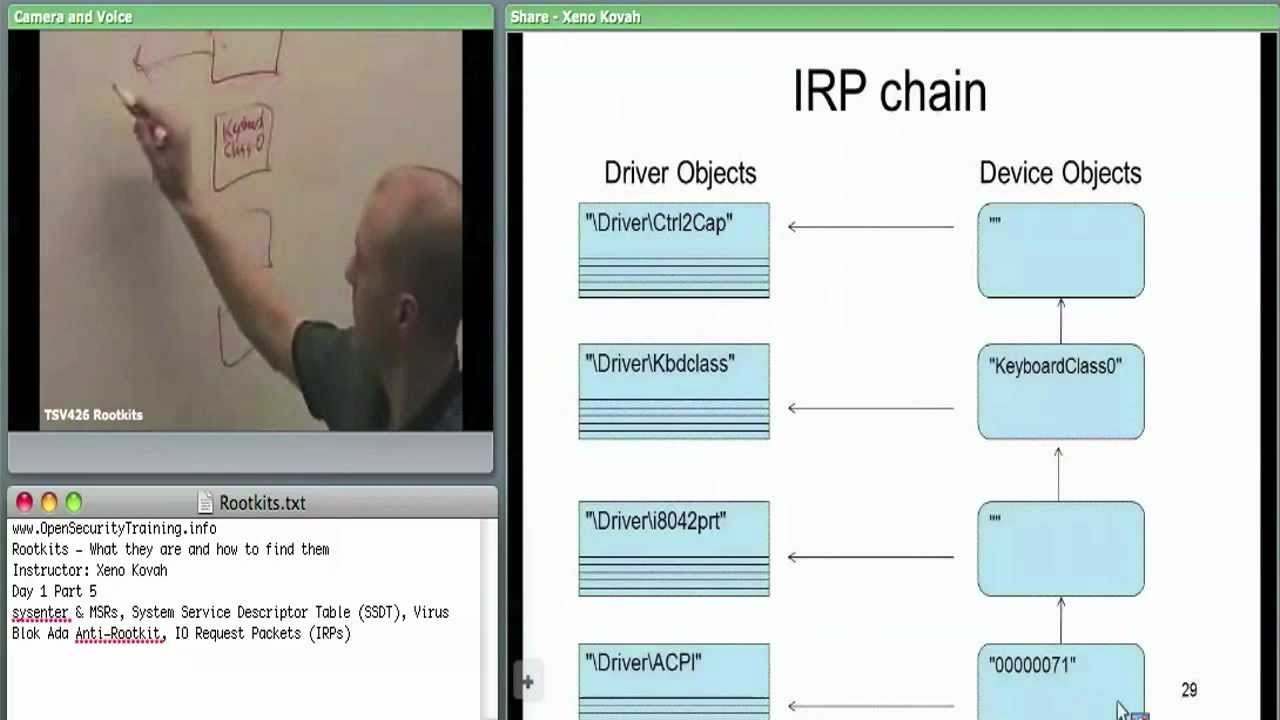
Day 1 Part 5: Rootkits: What they are, and how to find them
bootkitsclassescomputer securitycomputer security classcyber securityDKOMeducationhookingHost SecurityIAT hookingIDT hookinginline hooksIRP hookingKOHmalwaremalware detectionmulti-day-classmulti-day-trainingOpenSecurityTraining.inforootkit detectionRootkitsSSDT hookingstealth malwaretrainingWindows rootkitsx86 assembly
Recent Posts
- Addition: Java 11 For Complete Beginners 013
- M365 Transformations: Awareness Training
- New Interview Questions ISO 27001 #iso27001 #ISO27002 #ISOaudit #ISO27001exam #ISO27001course
- Breaking Elon Musk Unveils 2025 Tesla Bot Gen 3 with Major Upgrades and Impressive New Abilities!
- NEWS UPDATE BREAKING Philadelphia plane crash, 6 dead, explosions reported
