Tag Archives: Hacking For Beginners

CEH18-3 Cloud Security Alliance
#Shells#TesteraircrackbasicsBeginnersburp suiteCompletecourseCybersecurityenumerationethicalethical hackerexpertfootprintingfreehackingHacking CourseHacking For Beginnershacking tutorialinformation securityInfosecitlearn hacking in banglamacchangermetasploitnmaponlinepass the hashpenetrationpenetration testerPentesterport scanningproxychainsreport writingreverse shellSecuritySQLtestingtrainingUdemyZero to Hero

Learn Ethical Hacking from Scratch
codequscyber attackcyber securitycyber security analystCybersecurityddos atatckdos atatckethical hackerethical hackingethical hacking careerEthical Hacking Courseethical hacking tutorialhackerhackingHacking CourseHacking For Beginnershacking tutoriallearn ethical hackingLearn Ethical Hacking From Scratchmalware analysisMoriohnetwork scanningpenetration testerSecuritysql injectionsystem hackingvulnerability analysis

CEH16-2 Mobile Hacking tools
#Shells#TesteraircrackbasicsBeginnersburp suiteCompletecourseCybersecurityenumerationethicalethical hackerexpertfootprintingfreehackingHacking CourseHacking For Beginnershacking tutorialinformation securityInfosecitlearn hacking in banglamacchangermetasploitnmaponlinepass the hashpenetrationpenetration testerPentesterport scanningproxychainsreport writingreverse shellSecuritySQLtestingtrainingUdemyZero to Hero
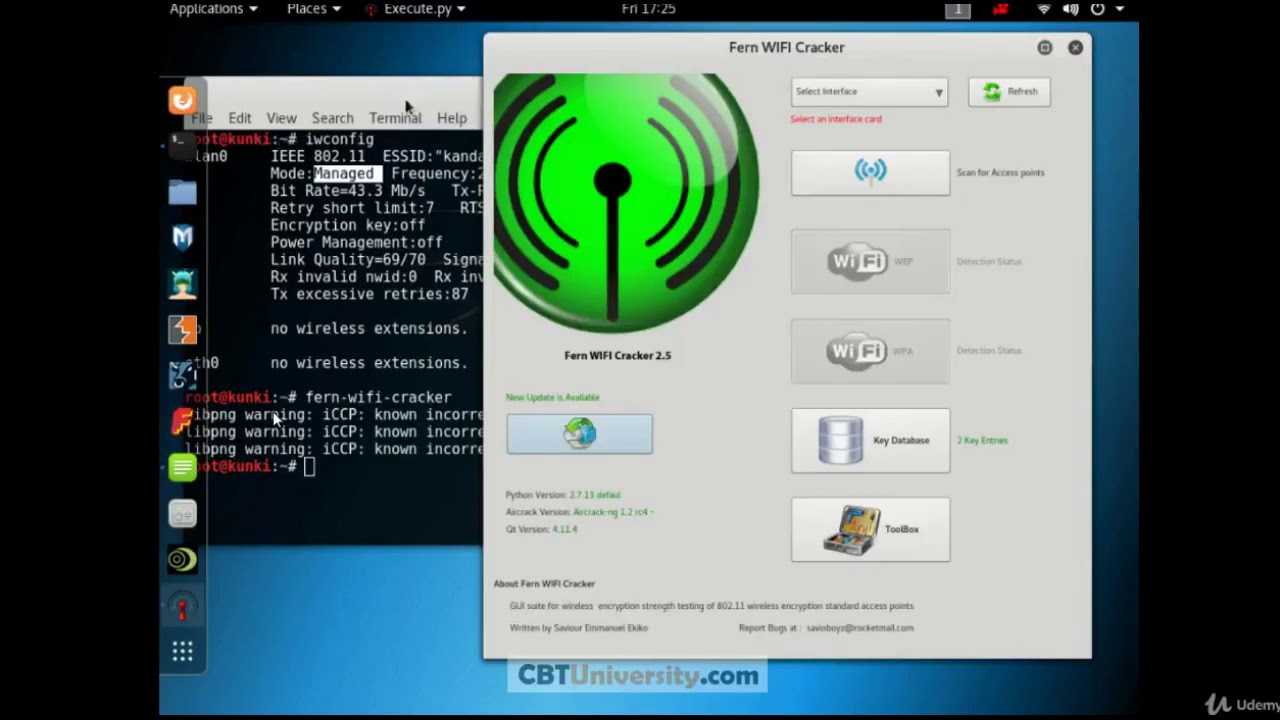
CEH 15 FERN wifi cracker
#Shells#TesteraircrackbasicsBeginnersburp suiteCompletecourseCybersecurityenumerationethicalethical hackerexpertfootprintingfreehackingHacking CourseHacking For Beginnershacking tutorialinformation securityInfosecitlearn hacking in banglamacchangermetasploitnmaponlinepass the hashpenetrationpenetration testerPentesterport scanningproxychainsreport writingreverse shellSecuritySQLtestingtrainingUdemyZero to Hero

Learn Ethical Hacking From Scratch Part-1
beginnercourseethical hackingethical hacking beginnerfreefree hacking coursefree hacking course beginnerfree hacking course for beginnerhackingHacking For Beginnerslearnlearn ethical hackingLearn Ethical Hacking From Scratchlearn hackinglearn hacking beginnerslearn hacking for beginnerlearn hacking for beginnersLearn Hacking From ScratchUdemy

Ethical Hacking using Kali Linux Tutorial | APT17
APT17ethical hackingethical hacking for beginnersethical hacking full courseethical hacking kali linuxethical hacking tutorialethical hacking tutorials for beginnersEthical Hacking using Kali Linux TutorialhackerhackingHacking For Beginnerskali linuxkali linux hackingkali linux hacking tutorialskali linux on androidkali linux raspberry pi 3Kali Linux Tutorialkali linux wifi hackProgrammingLanguagestvtutorial

Hacking For Beginners
cyber attackscyber securityCyber Security CourseCybersecurityethical hackinghackhackerhacker newshackingHacking 2018hacking classesHacking For Beginnershacking in historyhacking newshow to hackkali linuxkali linux hack wifikali linux hacking tutorialskali linux tutorialslearn ethical hackingLearn Website HackingNetwork SecurityUdemyWebsite Hacking
Recent Posts
- How to Become a Great Software Developer — Best Advice from Top-Notch Engineers
- Using FIDO for Multifactor authentication with WSO2 Identity Server #Identityin15
- Proof of possession for OAuth2 tokens(DPoP) with WSO2 Identity Server #Identityin15
- Lecture 2021 Numerical Methods: 37: Numerical Approximation of Partial Derivatives (3)
- Log Management with Monasca
