Tag Archives: guide
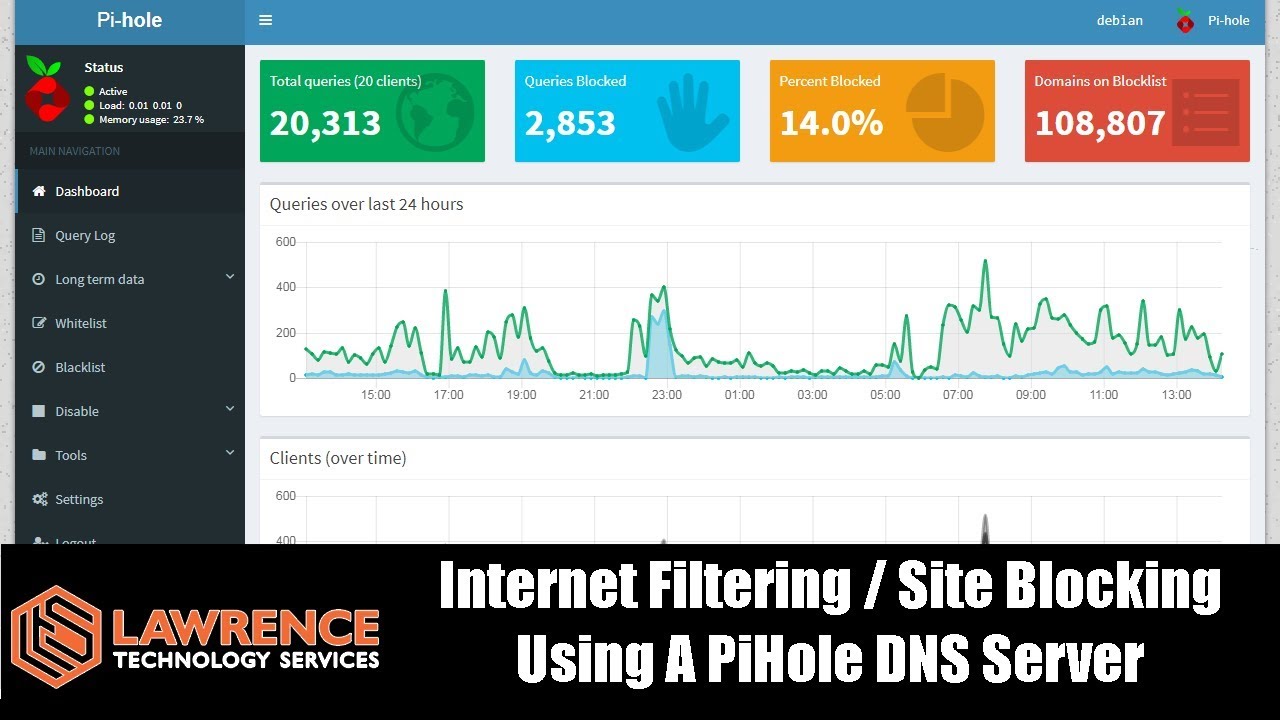
How To Setup Internet Filtering / Site Blocking Using A PiHole As A DNS Server
adad block ipadad blockerad blockingad blocking serverad blocking with raspberry pi 2advertismentblockerblockingConfigurationcontent filteringcontent filtering ipaddns server with raspberry pi 2domain name server raspberry pi 2guidenetworkingpipi-holepiholeprojectprojectsraspberryRaspberry piraspberry pi projectsraspirouterrpisetupunifiwhole home

2020 Getting started with pfsense 2.4 Tutorial: Network Setup, VLANs, Features & Packages
2018 Getting started with pfsenseFirewallGetting started with pfsenseguidehow to install pfsenseinstall pfsenselawrencesystemsNTEL PRO/1000 ET Quad Portpfsensepfsense (software)pfsense 2.3pfsense 2.4.5pfsense buildpfsense downloadpfsense firewallpfsense hardwarepfsense installpfsense installationpfsense routerpfsense setuppfsense tutorialroutertutorial
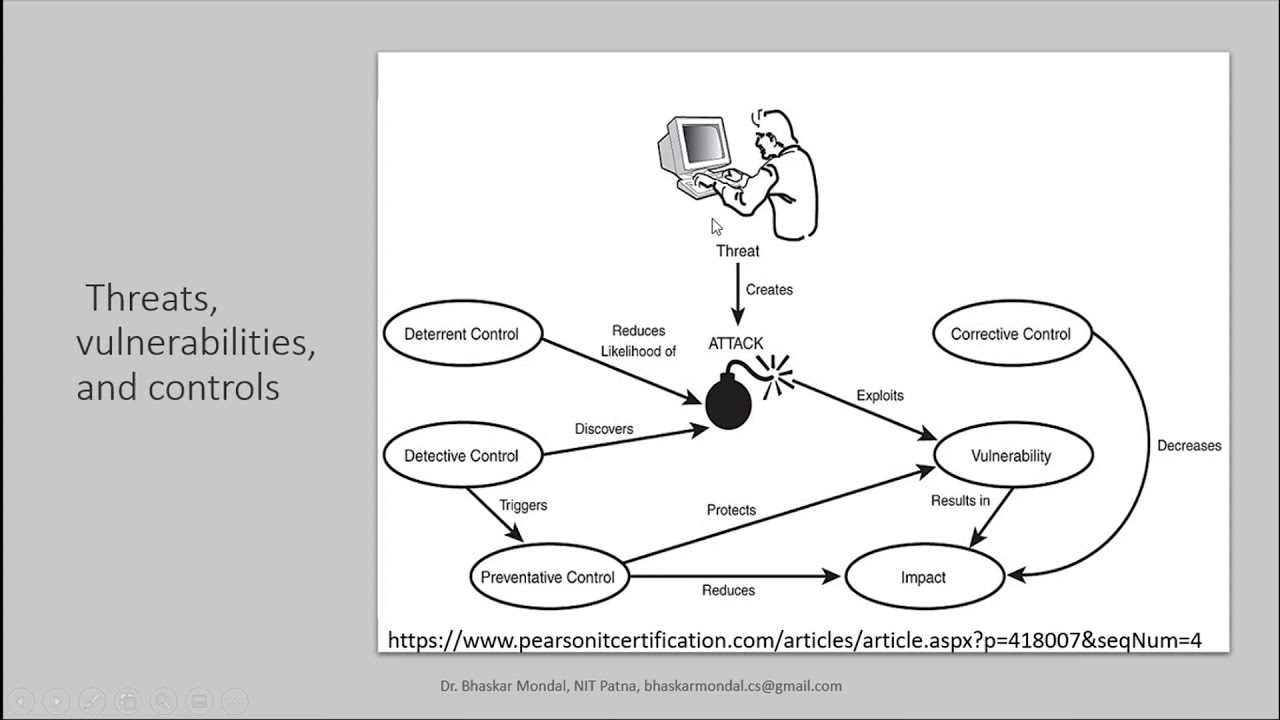
Threats, vulnerabilities, and controls in Information Security
Access ControlAESAIassignmentcode for beginners tutorialcomputecrypto systemcryptographycyber attackcyber securityDBMSdecryptiondeep learningDESdiyECCencryptionFLATguideHow toIDSinformation securityinstallintrusion detectionLATEXlearn to programlecturemachine learningMLNetwork Securityprivate keyprogrammingpublic keypythonrsascientific computingSecuritySHASQLTOCtutorial“computer laboratory” computer science GATE

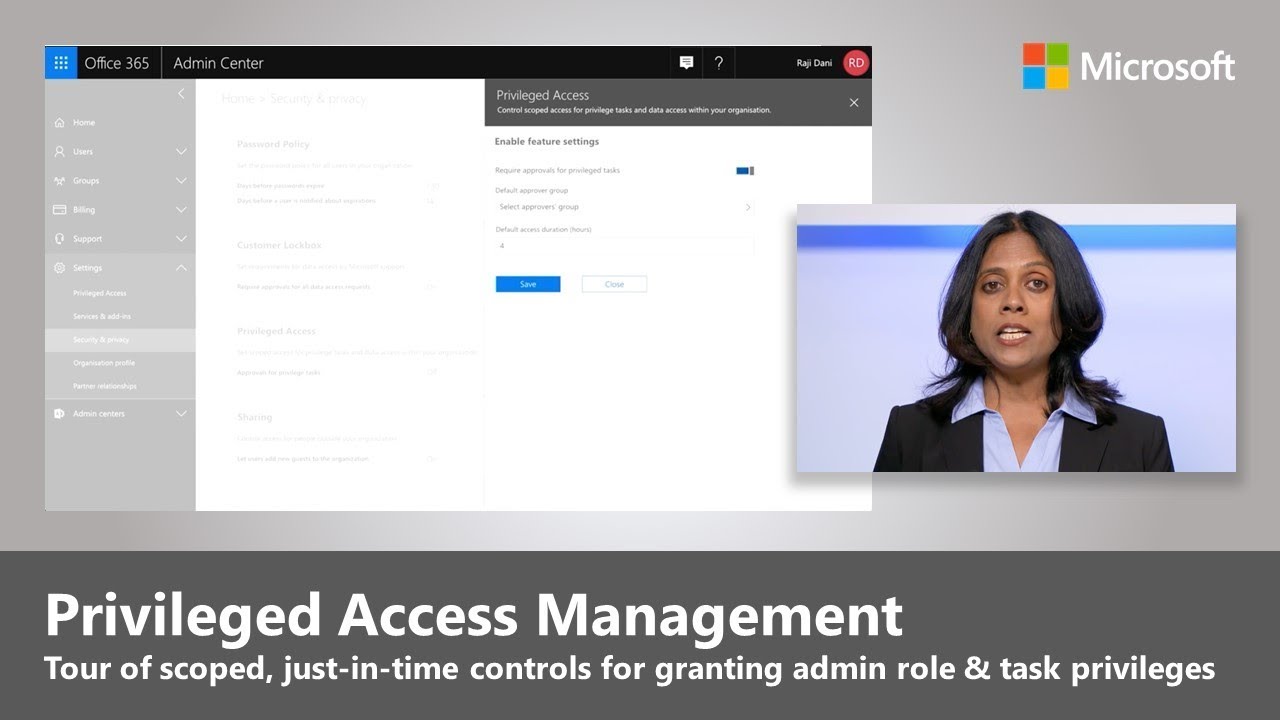
Introducing privileged access management in Office 365
Access ManagementAdminadministratorapprovalapproveAudit'azure adCloud SecurityCybersecurityData SecuritydemodemonstrationguideHow toidamidentityinformation securityIT SecurityJITjust enough accessjust in timelockboxOffice 365privilegeprivileged accountsSecuritystep-by-steptasktutorialzero standing accesszero standing privilege
Keynote Talk on Cyber Security and Symmetric Key Encryption
Access ControlAESAIassignmentcode for beginners tutorialcomputecrypto systemcryptographycyber attackcyber securityDBMSdecryptiondeep learningDESdiyECCencryptionFLATguideHow toIDSinformation securityinstallintrusion detectionLATEXlearn to programlecturemachine learningMLNetwork Securityprivate keyprogrammingpublic keypythonrsascientific computingSecuritySHASQLTOCtutorial“computer laboratory” computer science GATE

Exploring Microservices in Docker and Microsoft Azure
azureazure microservicesbuilddeployDockerdocker microservicesdocker tutorialdocker tutorial for beginnersguideintroductionmicroservice microsoftmicroservicesmicroservices architecturemicroservices azuremicroservices azure tutorialmicroservices dockermicroservices docker and azuremicroservices docker and kubernetesmicroservices in dockermicroservices tutorialmicrosoftMicrosoft Azuremicrosoft azure dockerMoriohtutorialwhat are microservices
Cloud Computing Tutorial For Beginners
Amazon Web Servicesaws cloudcloudCloud Computingcloud computing awscloud computing azurecloud computing basicscloud computing explainedcloud computing fundamentalscloud computing in hindicloud computing servicescloud computing tutorialcloud computing tutorial for beginnersguideintroduction to cloud computinglearnlearn cloud computingMoriohtrainingtutorialtypes of cloud computingwhat is cloud computingwhat is cloud computing with example

2018 Getting started with pfsense 2.4 from install to secure! including multiple separate networks
2018 Getting started with pfsenseFirewallGetting started with pfsenseguidehow to install pfsenseinstall pfsenseNTEL PRO/1000 ET Quad Portpfsensepfsense (software)pfsense 2.3pfsense downloadpfsense firewallpfsense hardwarepfsense installpfsense installationpfsense routerpfsense setuppfsense tutorialroutertutorial
Recent Posts
- IGF 2022 – Day 3 – PBR – WS #260 Protecting Shared Computation Cloud Security
- NEWS Tesla Powerwall: A Game-Changer for Replacing Gas Generators
- Privacy – Lecture7.1 Security Engineering COMP6441 (rerecorded lecture) – Richard Buckland UNSW
- Securing the Container Pipeline at Salesforce – Use Case Track
- What is IAAS in Cloud Computing? | IAAS #viralshorts #cloudcomputing #ytviralshorts #azuretraining
