Tag Archives: cyber attack



Learn Ethical Hacking from Scratch
codequscyber attackcyber securitycyber security analystCybersecurityddos atatckdos atatckethical hackerethical hackingethical hacking careerEthical Hacking Courseethical hacking tutorialhackerhackingHacking CourseHacking For Beginnershacking tutoriallearn ethical hackingLearn Ethical Hacking From Scratchmalware analysisMoriohnetwork scanningpenetration testerSecuritysql injectionsystem hackingvulnerability analysis
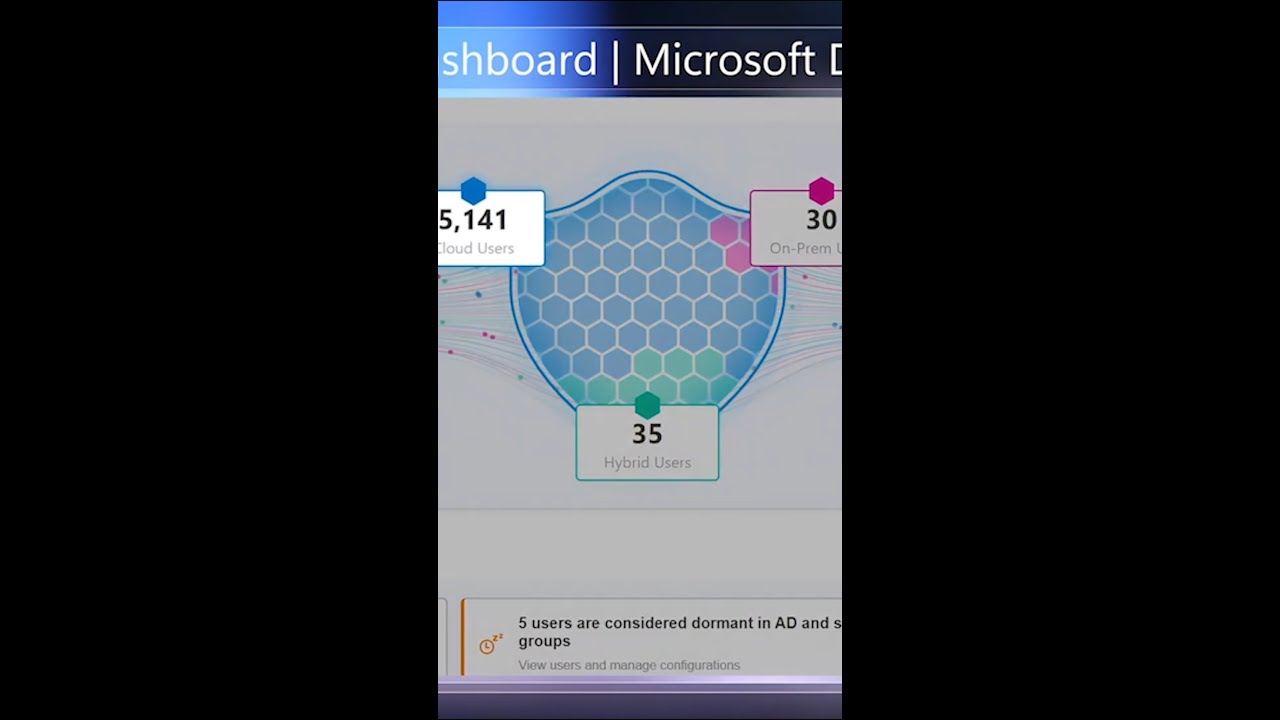
Protect against identity-based attacks.
Access ManagementActive Directoryadvanced huntingCloud SecurityConditional Access PoliciesCopilotCopilot for Securitycyber attackcyber securityIAMIdentity and Access Managementidentity based attacksIdentity Postureidentity securityIdentity threat detectionidentity threat detection and responseITDRMicrosoft Defender XDRMicrosoft EntraMicrosoft securityprivileged identitysecure score in microsoft defender for cloudthreat detectionXDR



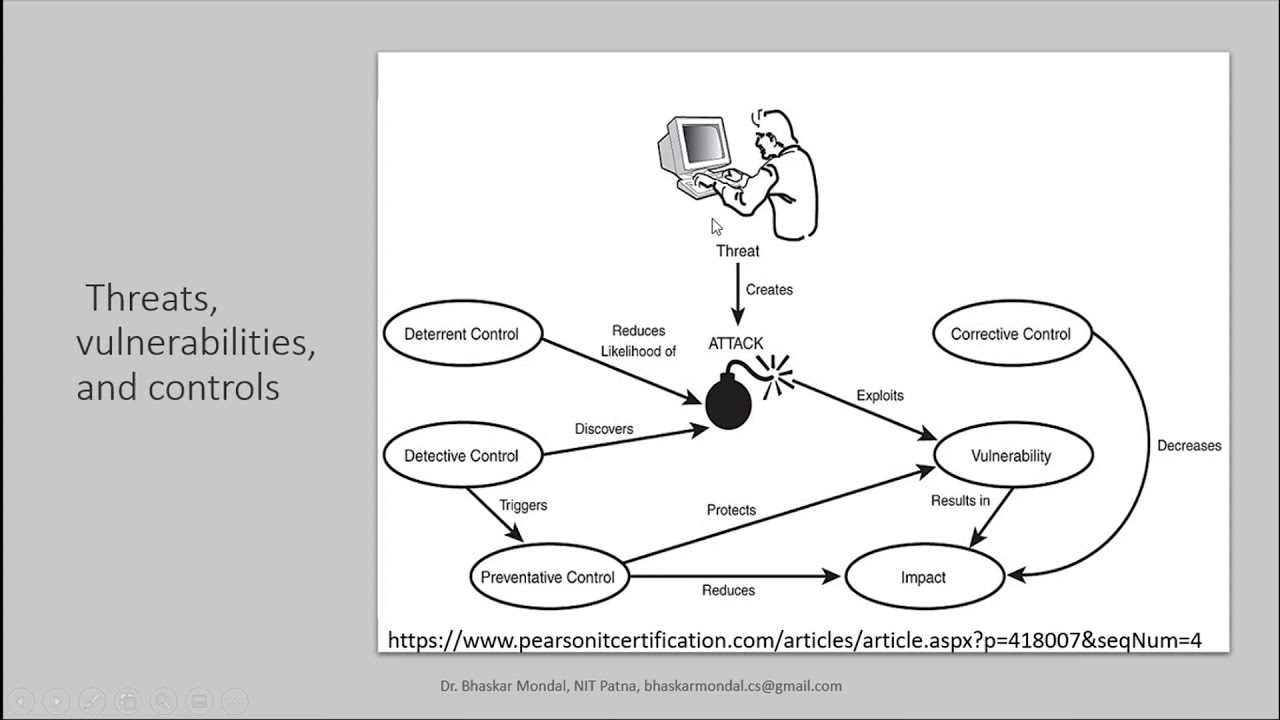
Threats, vulnerabilities, and controls in Information Security
Access ControlAESAIassignmentcode for beginners tutorialcomputecrypto systemcryptographycyber attackcyber securityDBMSdecryptiondeep learningDESdiyECCencryptionFLATguideHow toIDSinformation securityinstallintrusion detectionLATEXlearn to programlecturemachine learningMLNetwork Securityprivate keyprogrammingpublic keypythonrsascientific computingSecuritySHASQLTOCtutorial“computer laboratory” computer science GATE
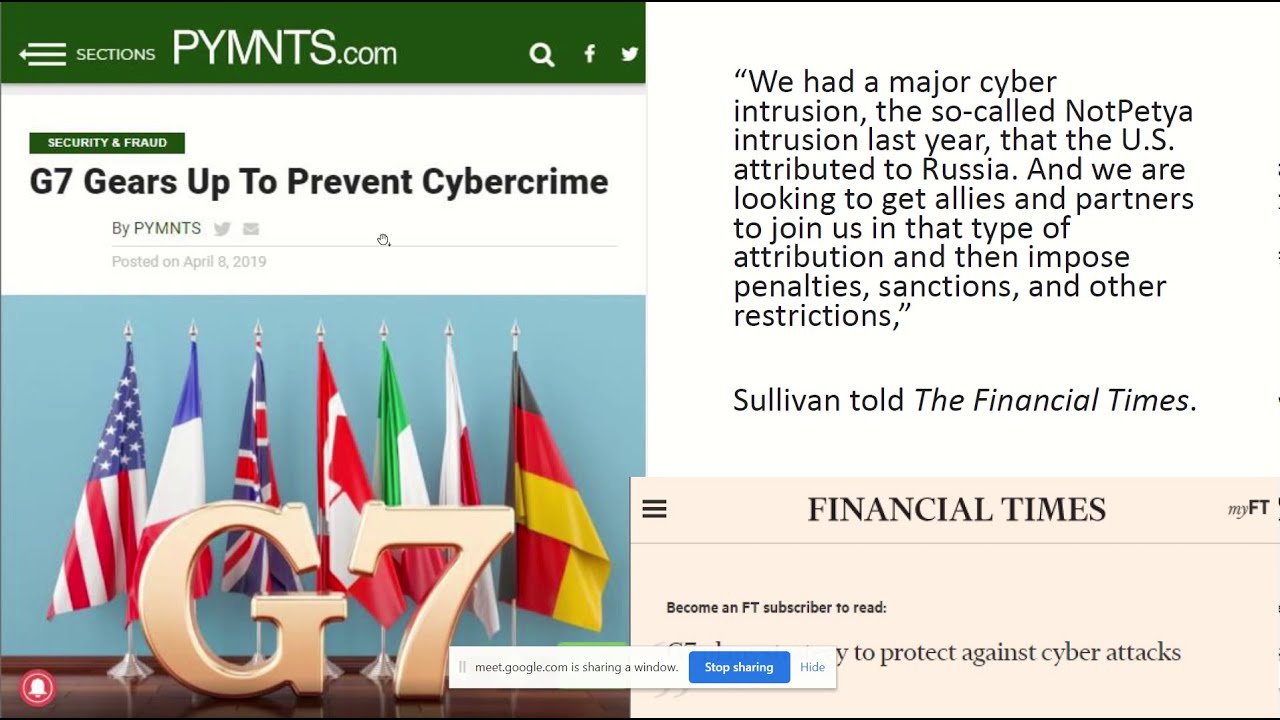
Keynote Talk on Cyber Security and Symmetric Key Encryption
Access ControlAESAIassignmentcode for beginners tutorialcomputecrypto systemcryptographycyber attackcyber securityDBMSdecryptiondeep learningDESdiyECCencryptionFLATguideHow toIDSinformation securityinstallintrusion detectionLATEXlearn to programlecturemachine learningMLNetwork Securityprivate keyprogrammingpublic keypythonrsascientific computingSecuritySHASQLTOCtutorial“computer laboratory” computer science GATE
Recent Posts
- uPortal Q3 2018 Quarterly OSS Briefing
- Sharepoint: Querying Sharepoint Online From C# CSOM Console App
- How to generate FedAuth / RTFA cookies to make sharepoint online requests when using…
- Azure virtual machine lab#youtubevideo #youtube
- Azure #interview #youtubeshorts #shortsvideo #azuretraining #tutorialvideo #azure #multiplechoice
