Tag Archives: computer security class
Day 1 Part 6: Rootkits: What they are, and how to find them
bootkitsclassescomputer securitycomputer security classcyber securityDKOMeducationhookingHost SecurityIAT hookingIDT hookinginline hooksIRP hookingKOHmalwaremalware detectionmulti-day-classmulti-day-trainingOpenSecurityTraining.inforootkit detectionRootkitsSSDT hookingstealth malwaretrainingWindows rootkitsx86 assembly
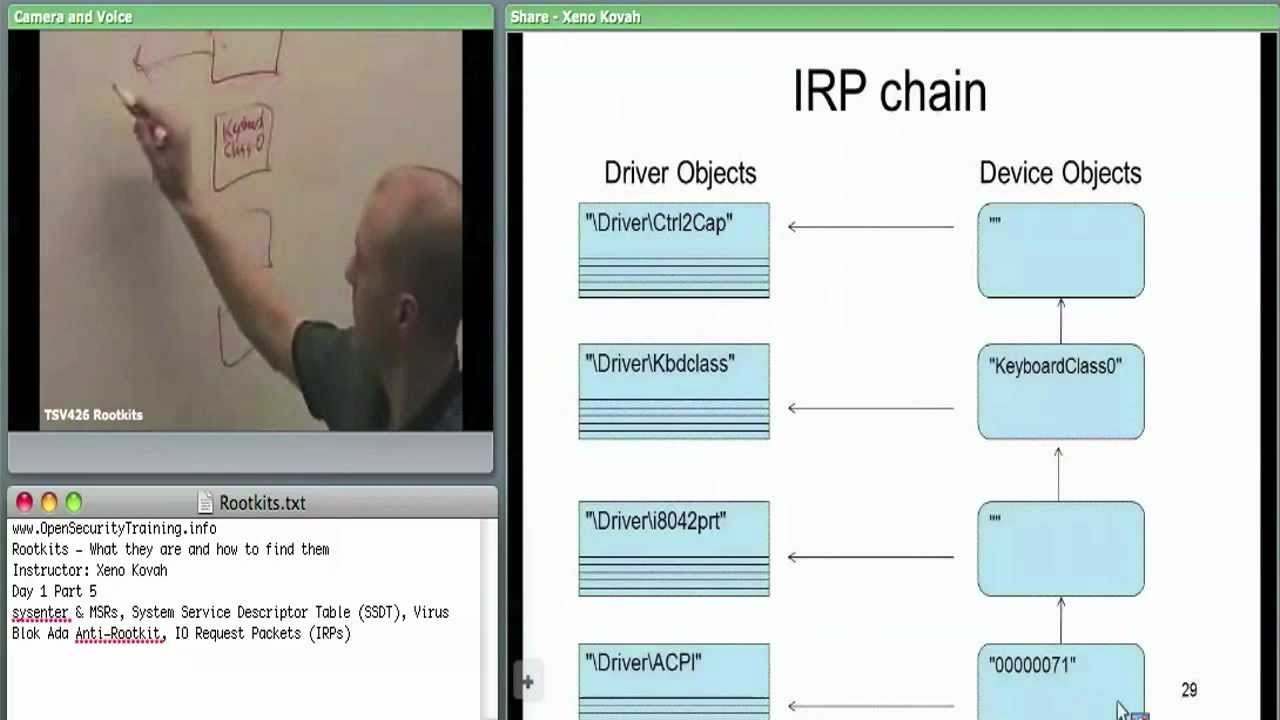
Day 1 Part 5: Rootkits: What they are, and how to find them
bootkitsclassescomputer securitycomputer security classcyber securityDKOMeducationhookingHost SecurityIAT hookingIDT hookinginline hooksIRP hookingKOHmalwaremalware detectionmulti-day-classmulti-day-trainingOpenSecurityTraining.inforootkit detectionRootkitsSSDT hookingstealth malwaretrainingWindows rootkitsx86 assembly

Day 1 Part 2: Intro Trusted Computing
attestationAuthenticationclassesComputercomputer securitycomputer security classcryptographycyber securityCybersecuritydecryptiondigital signaturesDRTMdynamic root of trusteducationencryptionOpenSecurityTraining.infoPCRPCRsSecuritySRTMstatic root of trustTPMtrainingtrustTrusted ComputingTrusted Computing Grouptrusted hardwareTrusted Platform Module
Recent Posts
- DevOps & SysAdmins: Trying to use Azure AD as LDAP server with Cisco Catalyst IP Base
- Understanding Microsoft Azure AD SSO with non-persistent VDI (Instant Clones)
- How to host AspNet MVC app for free in #Azure #AppServices || Bangla Tutorial
- Raspberry Pi: Connect Raspberry Pi to Azure IoT Hub
- .NET Core Reporting Tools: print and export a report without preview from code (2022)
