Tag Archives: Access Management


Introduction to WSO2 Identity Server 7.0 | an Overview
Access ManagementAPI authorizationAPI Securityapp authenticationapp user authorizationAsgardeoB2B capabilitiesb2b CIAMdigital identity managementEnterprise SecurityIAM solutioniam tutorialIdentity Managementidentity management tutorialidentity securityIdentity Server 7.0identity server tutorialsecurity solutionssocial login integrationWSO2 Identity ServerWSO2 tutorial
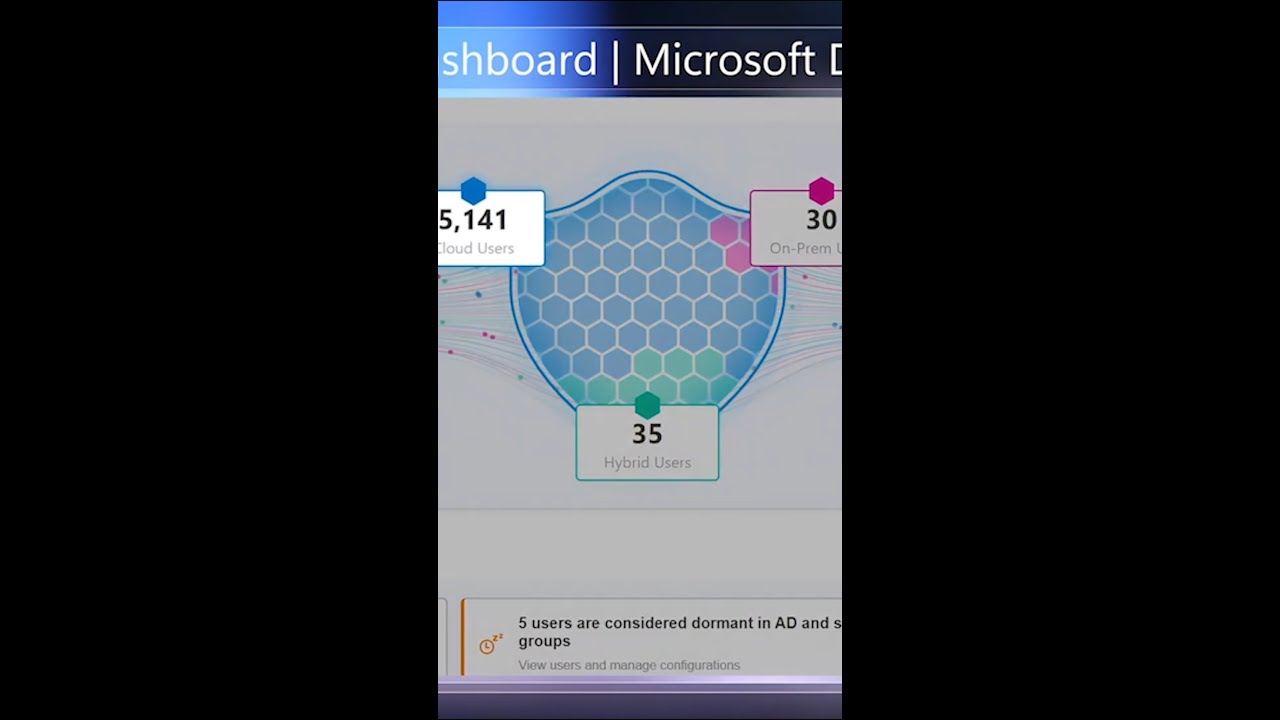
Protect against identity-based attacks.
Access ManagementActive Directoryadvanced huntingCloud SecurityConditional Access PoliciesCopilotCopilot for Securitycyber attackcyber securityIAMIdentity and Access Managementidentity based attacksIdentity Postureidentity securityIdentity threat detectionidentity threat detection and responseITDRMicrosoft Defender XDRMicrosoft EntraMicrosoft securityprivileged identitysecure score in microsoft defender for cloudthreat detectionXDR
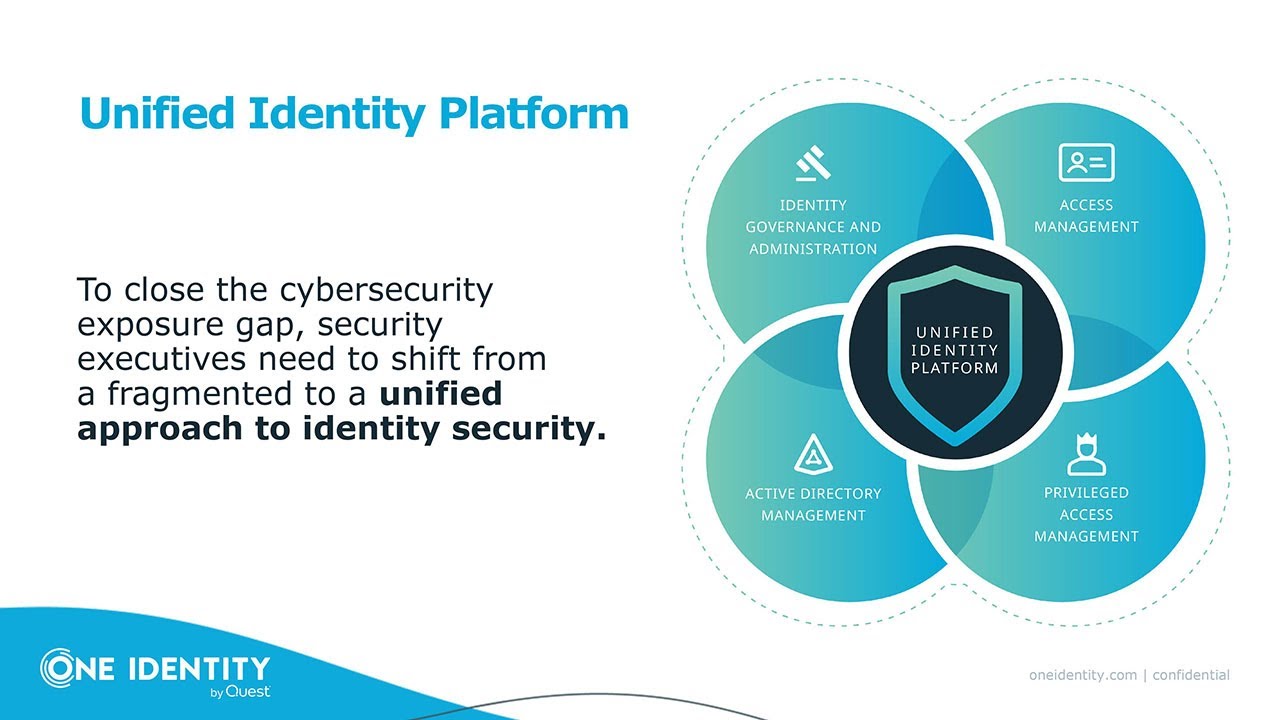
One Identity e la gestione unificata delle identità
Access Managementactive rolesamApplication Securitycloudcyber gangCybersecuritygestione unificata identitàIAMIdentity & Access Managementidentity correlationidentity governance administrationidentity securityidentity sprawligajust-in-time privilegedmassimiliano micuccimicrosoft active directory managementone identitypampar-tecprivileged access managementproliferazione identitàRansomwareSaaSsafeguardunified identity platformzero trust

ITGC Basics
Access Managementapplication controlsbackup managementChange ManagementControlsdata recoveryincident managementInformation technology general controlsITGCITGC domainslogical accesspenetratingpenetrating testingphysical accessSDLCSecurity Incidentsystem development life cycleVAPTvulnerabilityVulnerability management


Sam, the IT Admin, Figures out Advanced Authentication
Access GovernancemAccess ManagementAdvanced Authenticationadvanced authentication frameworkBreachcard readerChallenge and ResponseCIOCredit Card DatafraudHackedID Badgeidentity theftIT SecurityMicro FocusmicrofocusMobile ComputingMobile WorkersMulti-Factor AuthentifactionMultifactor AuthenticationNetIQone-time-passwordpasswordsproximity cardsSecuritysmart cardsSmart PhonesSMS Passwordsunauthorized accessUsernames

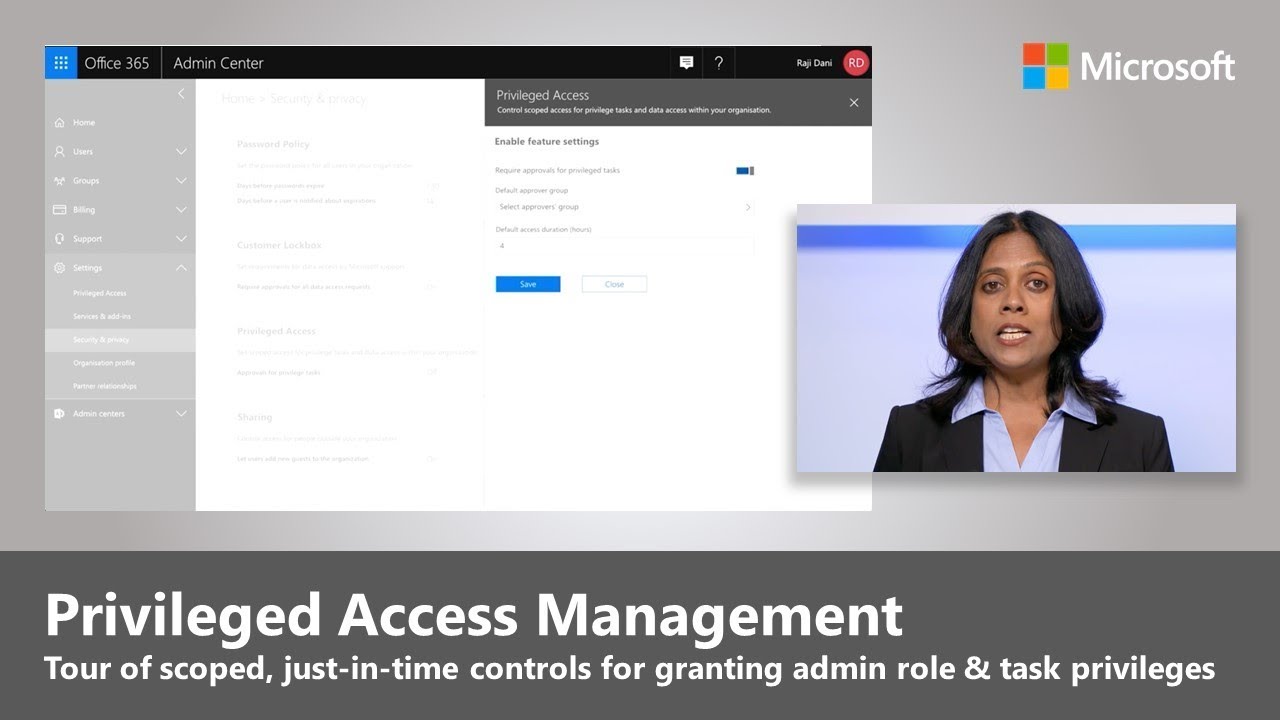
Introducing privileged access management in Office 365
Access ManagementAdminadministratorapprovalapproveAudit'azure adCloud SecurityCybersecurityData SecuritydemodemonstrationguideHow toidamidentityinformation securityIT SecurityJITjust enough accessjust in timelockboxOffice 365privilegeprivileged accountsSecuritystep-by-steptasktutorialzero standing accesszero standing privilege
Recent Posts
- IAM4NFDI quickly explained
- Steganography (1/2) BsidesCT CTF 2018
- Pentagon calls Turkish drone shot down in Syria by US forces a ‘regrettable incident’
- Sodinokibi Ransomware Encrypts Hundreds of Dental Practices via IT Provider PerCSoft.
- #19 Method in Java | what is method overloading in java | Tutorials for beginners
