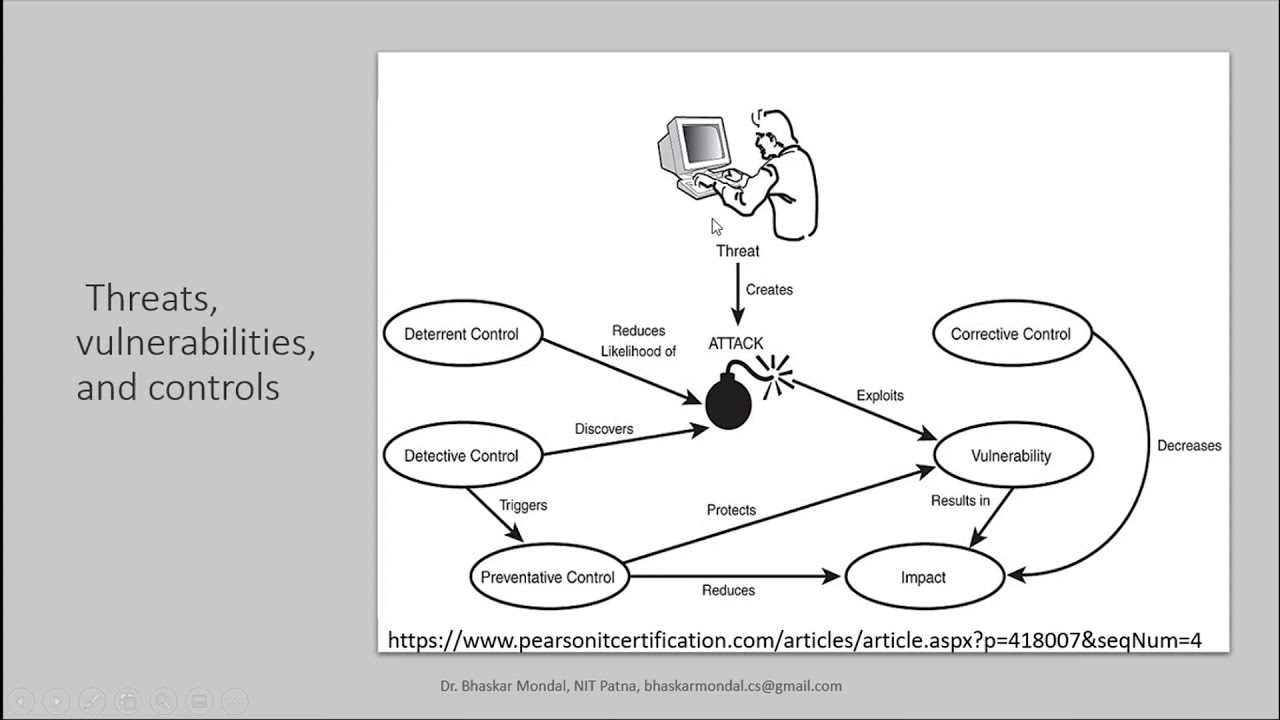
Threats, vulnerabilities, and controls in Information Security
Access ControlAESAIassignmentcode for beginners tutorialcomputecrypto systemcryptographycyber attackcyber securityDBMSdecryptiondeep learningDESdiyECCencryptionFLATguideHow toIDSinformation securityinstallintrusion detectionLATEXlearn to programlecturemachine learningMLNetwork Securityprivate keyprogrammingpublic keypythonrsascientific computingSecuritySHASQLTOCtutorial“computer laboratory” computer science GATE
