Tag Archives: wpa2

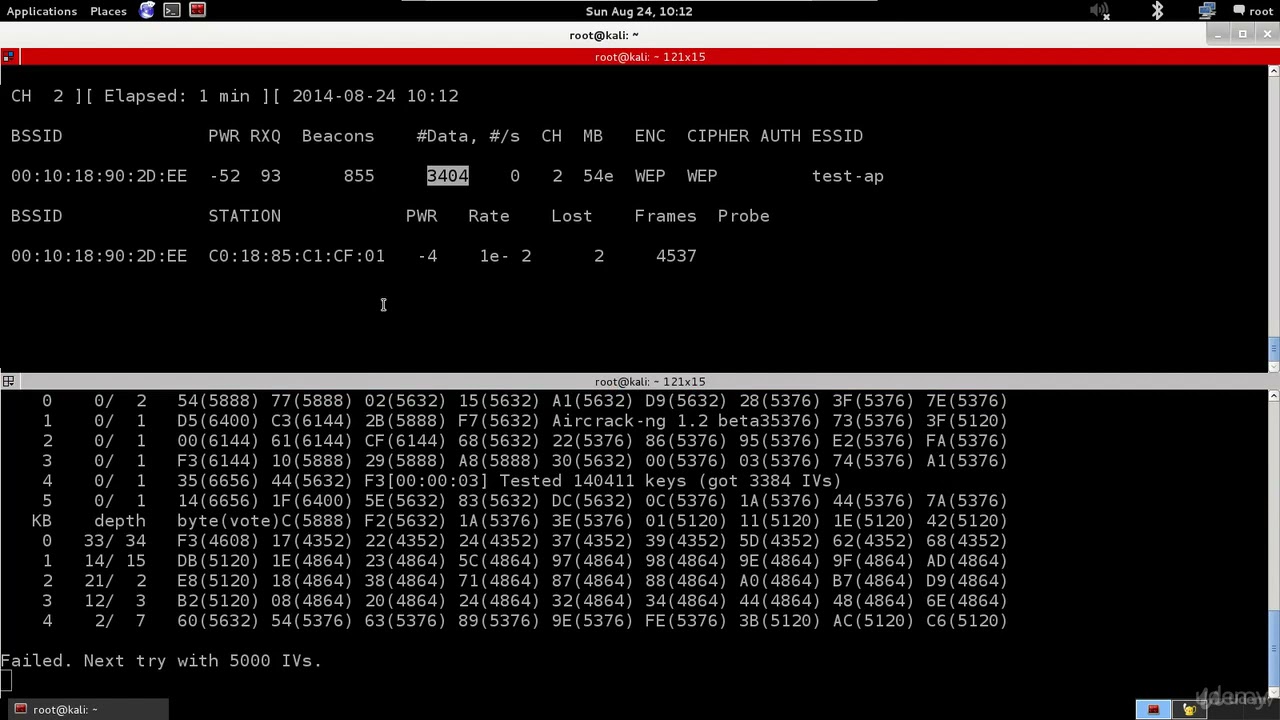
032. Vulnerability scanning with Kali Linux | Hacking With Kali Linux
ethical hackinghack форумhackerhackinghow to hack wifi passwordKalikali linuxkali linux installKali Linux Tutorialkali nethunterLinuxnethunterTERMUXubuntuvpn tor socks vpswi-fiwifiwifi crackingwifi hackingwifi passwordwifitewpa2wpa2 crackingwpa3взломвпн тор сокс васкак стать хакеромкак установить кали линукслинукснастройка кампьютера для анонимность в сетинастройка компьподключение к дёдикухакерхакеры

004. Preferred: Install Kali Using Pre-built Virtual Machine | Hacking With Kali Linux
ethical hackinghack форумhackerhackinghow to hack wifi passwordKalikali linuxkali linux installKali Linux Tutorialkali nethunterLinuxnethunterTERMUXubuntuvpn tor socks vpswi-fiwifiwifi crackingwifi hackingwifi passwordwifitewpa2wpa2 crackingwpa3взломвпн тор сокс васкак стать хакеромкак установить кали линукслинукснастройка кампьютера для анонимность в сетинастройка компьподключение к дёдикухакерхакеры
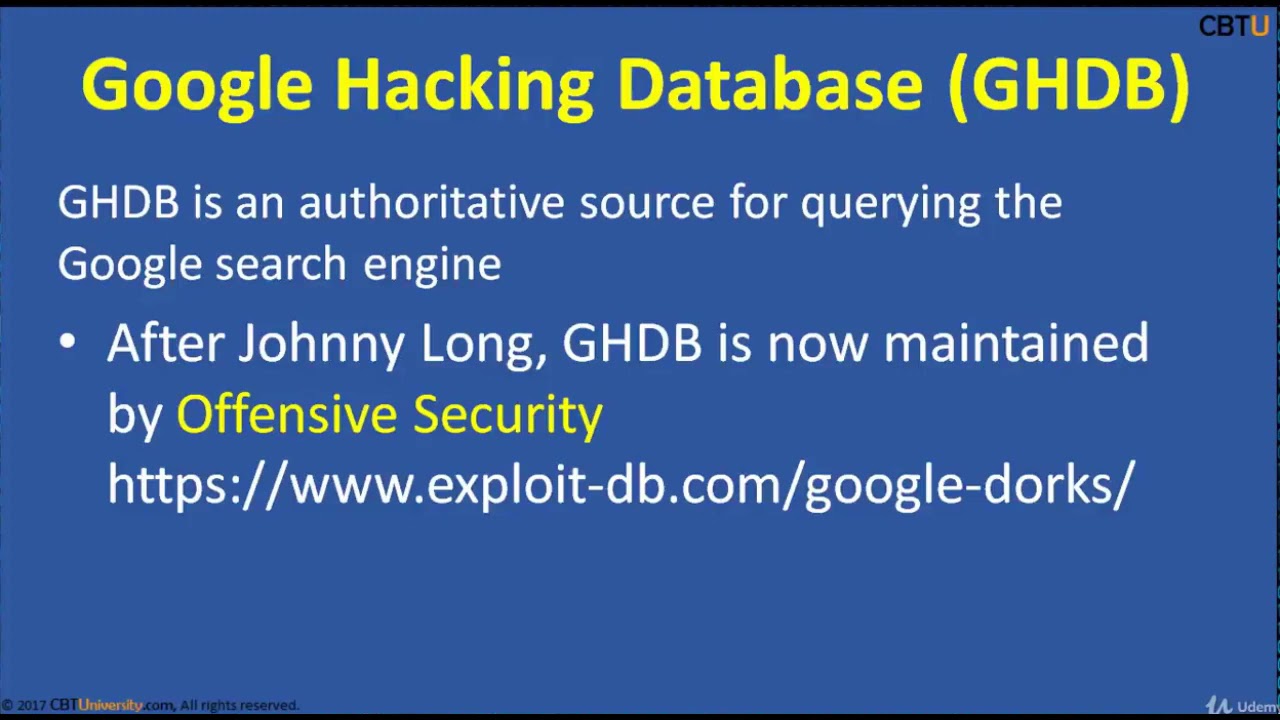
CEH2-3 Google Hacking Dorking
2015additionsaircrackbasicsBeginnersblackclicommandCompletecoursecrackcrackingenvironmentethicalexpertfootprintingforfreegreyguesthackhackerHacker (Interest)hackershackingHackshathdinstallinterfaceitKalikeylearn hacking in banglalineLinuxliveloggersmacchangernetworknmaponlinepenetrationprivateproxychainsreaverSecurityskillsSQLtermstestingtrainingUdemyvirtualvirtualboxVirtualBox (Software)vpnvpswhitewifiWindowswpawpa2

CEH1-1 Introduction to hacking
2015additionsaircrackbasicsBeginnersblackclicommandCompletecoursecrackcrackingenvironmentethicalexpertfootprintingforfreegreyguesthackhackerHacker (Interest)hackershackingHackshathdinstallinterfaceitKalikeylearn hacking in banglalineLinuxliveloggersmacchangernetworknmaponlinepenetrationprivateproxychainsreaverSecurityskillsSQLtermstestingtrainingUdemyvirtualvirtualboxVirtualBox (Software)vpnvpswhitewifiWindowswpawpa2
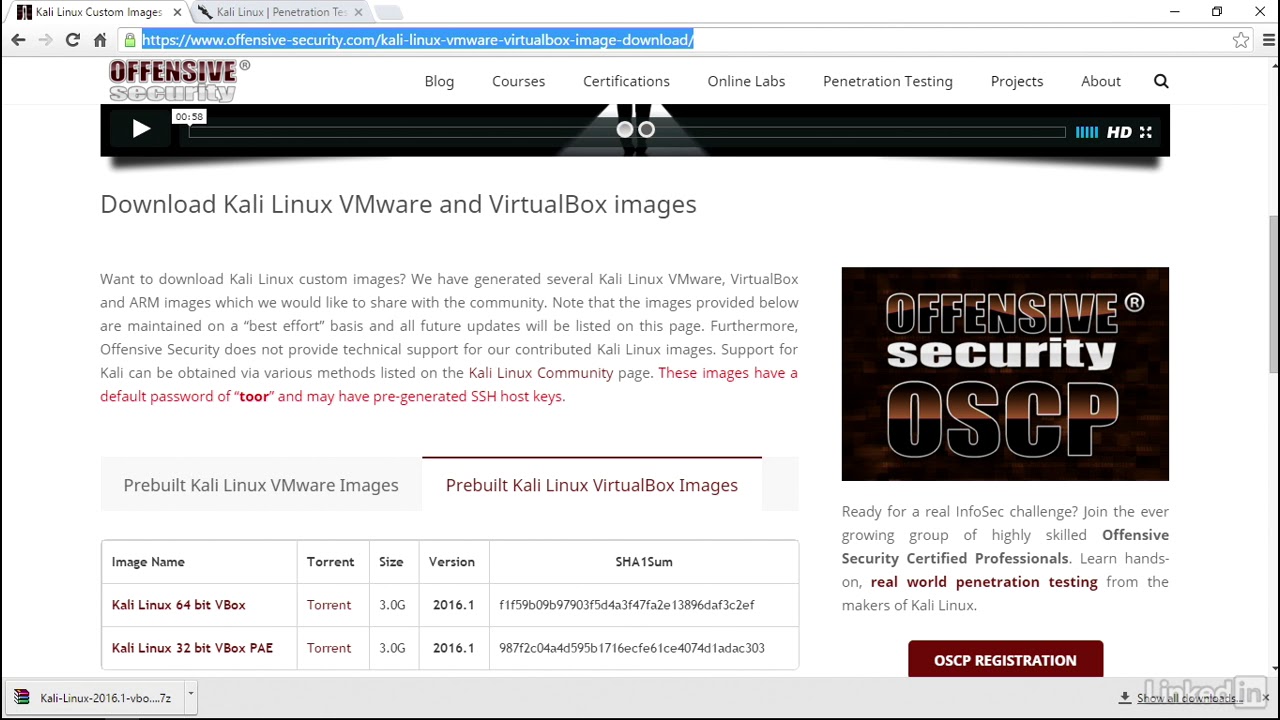
5 Installing appliances | Ethical Hacking
access pointaircrack-ngalfa cardapbacktrack linuxciscoComputercomputer securityencryptionfor beginnershackerhacking kalihacking wirelessInjectionKalikali linuxkali linux 2.0kali linux 2017.1kali linux 2017.2kali linux androidkali linux wifiklai linux 2017.2linksysLinuxlinux installmonitor modepasswordpassword crackingrouterSecuritytutorialwalkthroughwirelesswpa2

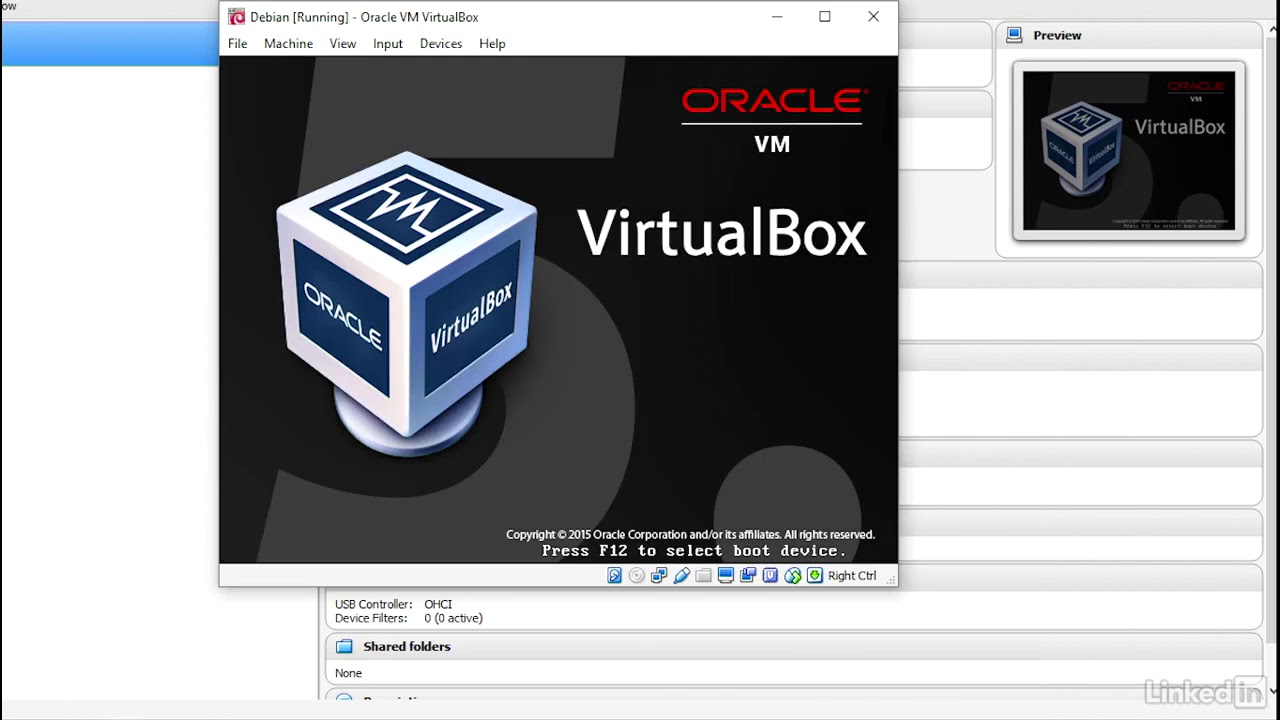
4 Installing virtual machines | Ethical Hacking
access pointaircrack-ngalfa cardapbacktrack linuxciscoComputercomputer securityencryptionfor beginnershackerhacking kalihacking wirelessInjectionKalikali linuxkali linux 2.0kali linux 2017.1kali linux 2017.2kali linux androidkali linux wifiklai linux 2017.2linksysLinuxlinux installmonitor modepasswordpassword crackingrouterSecuritytutorialwalkthroughwirelesswpa2
3 Setting up a virtual lab | Ethical Hacking
access pointaircrack-ngalfa cardapbacktrack linuxciscoComputercomputer securityencryptionfor beginnershackerhacking kalihacking wirelessInjectionKalikali linuxkali linux 2.0kali linux 2017.1kali linux 2017.2kali linux androidkali linux wifiklai linux 2017.2linksysLinuxlinux installmonitor modepasswordpassword crackingrouterSecuritytutorialwalkthroughwirelesswpa2
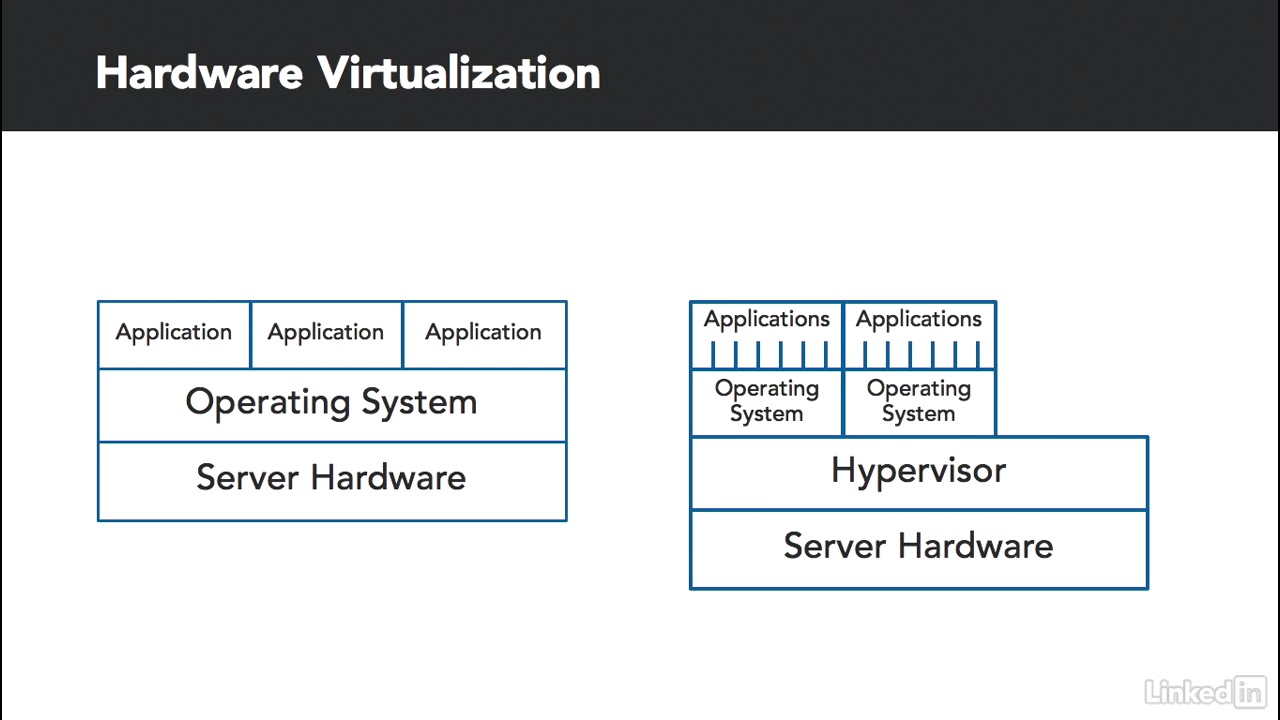
2 Introduction to virtualization | Ethical Hacking
access pointaircrack-ngalfa cardapbacktrack linuxciscoComputercomputer securityencryptionfor beginnershackerhacking kalihacking wirelessInjectionKalikali linuxkali linux 2.0kali linux 2017.1kali linux 2017.2kali linux androidkali linux wifiklai linux 2017.2linksysLinuxlinux installmonitor modepasswordpassword crackingrouterSecuritytutorialwalkthroughwirelesswpa2
