Tag Archives: white hat hacker
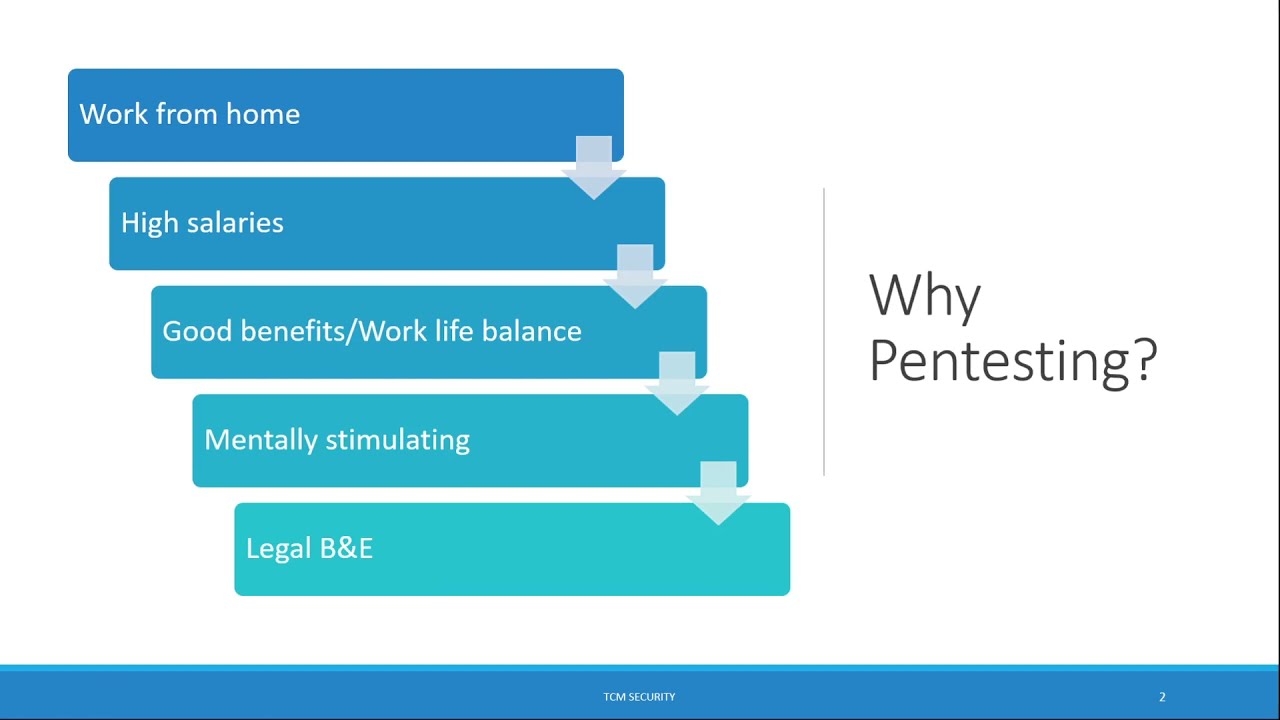
4 Introduction – A Day in the Life of an Ethical Hacker
anonymouscomputer hackingcyber securityCybersecurityethical hackerethical hackingEthical Hacking Courseethical hacking for beginnersethical hacking tutorialethical hacking tutorials for beginnershackhackerhackershackingHacking Coursehacking tutorialhow to be a hackerhow to hackInfoseckali linuxlearn hackingmetasploitmr.robotow to become a hackerpassword crackingpenetration testingSecuritytechTechnologytop 10white hat hacker

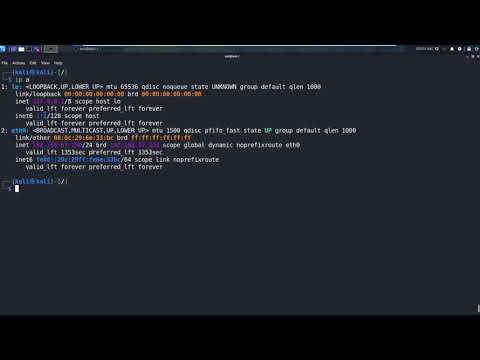
6 Introduction to Linux – Network Commands Update
anonymouscomputer hackingcyber securityCybersecurityethical hackerethical hackingEthical Hacking Courseethical hacking for beginnersethical hacking tutorialethical hacking tutorials for beginnershackhackerhackershackingHacking Coursehacking tutorialhow to be a hackerhow to hackInfoseckali linuxlearn hackingmetasploitmr.robotow to become a hackerpassword crackingpenetration testingSecuritytechTechnologytop 10white hat hacker
What is KALI LINUX | KALI LINUX क्या है | हर हैकर का सपना | क्यों हर हैकर KALI LINUX पसंद करते हैं |
all about kali linuxbest kali linux guideblack hat hackerCertified Ethical Hacker (Ceh)facebook idgeek insaangrey hat hackerhow to hackhow to hack email idhow to use kali linuxinstall kali linuxjai maa kalikalkali linux 2020.2kali linux begineer guidekali linux better than windowskali linux osKali Linux Tutorialoperating systemwhat is kali linuxwhidows vs linuxwhite hat hackerwhy ethical hacker use kali linuxwhy to use kali linux
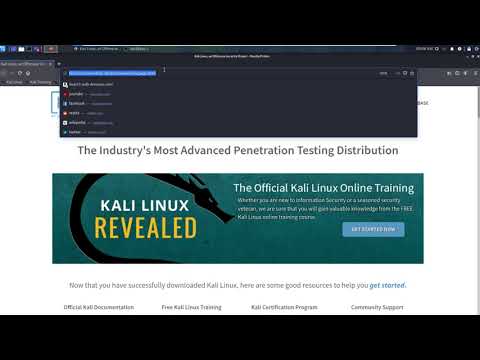
7 Introduction to Linux – Installing and Updating Tools
anonymouscomputer hackingcyber securityCybersecurityethical hackerethical hackingEthical Hacking Courseethical hacking for beginnersethical hacking tutorialethical hacking tutorials for beginnershackhackerhackershackingHacking Coursehacking tutorialhow to be a hackerhow to hackInfoseckali linuxlearn hackingmetasploitmr.robotow to become a hackerpassword crackingpenetration testingSecuritytechTechnologytop 10white hat hacker
Recent Posts
- Dapr’s Road Ahead: GenAI APIs, Distributed Scheduling at Scale and What It Means for… Y. Schneider
- Akamai Regains Control Over Their Cloud
- Building portable cloud applications with Quarkus, Azure Radius, Skupper, and Backstage
- 2 Hour Data Analyst Interview Masterclass | Interview Better Than The Competition
- Difference between Clustered Columnstore Index Table in Azure SQL and Table in Azure Data Warehouse
