Tag Archives: walkthrough
4 Installing virtual machines | Ethical Hacking
access pointaircrack-ngalfa cardapbacktrack linuxciscoComputercomputer securityencryptionfor beginnershackerhacking kalihacking wirelessInjectionKalikali linuxkali linux 2.0kali linux 2017.1kali linux 2017.2kali linux androidkali linux wifiklai linux 2017.2linksysLinuxlinux installmonitor modepasswordpassword crackingrouterSecuritytutorialwalkthroughwirelesswpa2
3 Setting up a virtual lab | Ethical Hacking
access pointaircrack-ngalfa cardapbacktrack linuxciscoComputercomputer securityencryptionfor beginnershackerhacking kalihacking wirelessInjectionKalikali linuxkali linux 2.0kali linux 2017.1kali linux 2017.2kali linux androidkali linux wifiklai linux 2017.2linksysLinuxlinux installmonitor modepasswordpassword crackingrouterSecuritytutorialwalkthroughwirelesswpa2
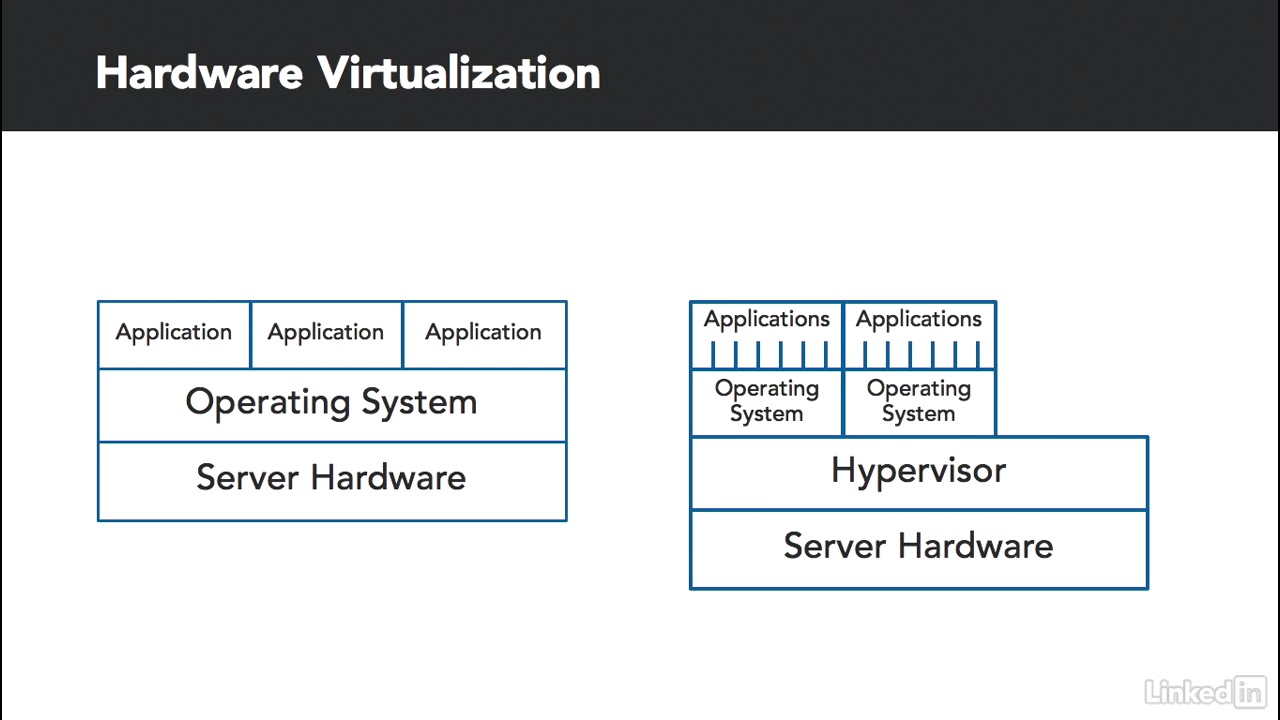
2 Introduction to virtualization | Ethical Hacking
access pointaircrack-ngalfa cardapbacktrack linuxciscoComputercomputer securityencryptionfor beginnershackerhacking kalihacking wirelessInjectionKalikali linuxkali linux 2.0kali linux 2017.1kali linux 2017.2kali linux androidkali linux wifiklai linux 2017.2linksysLinuxlinux installmonitor modepasswordpassword crackingrouterSecuritytutorialwalkthroughwirelesswpa2
Recent Posts
- DevOps & SysAdmins: Allow outbound traffic on an Azure Kubernetes cluster (3 Solutions!!)
- EKS Upgrade guide to version 1.23 | Avoid auto-updates
- Persistant data in a Node Express application
- Passing the Google Professional Cloud Architect Exam in 2023!
- AWS & AZURE for Deploying Services | Agenda for Module #02 | Episode #23
