Tag Archives: Threats

Getting a Fix on What Your Logs Aren't Telling You
best practicesBrennan O'HaraComplianceDark ReadingdataEricka ChickowskiEvent DatahipaaInformationWeekInGuardianinsider threatIT SecurityJohn SawyerLogsMicro FocusmicrofocusNetIQPCIRegulationSecuritySecurity LogsSecurity MonitoringSecurity PostureSIEMState of SecuritySystem LogsThreatsTipstricksWebcast

CSA Saudi talk AWS Certified Security
#engineeralliancearabiaArchitectureAWScertificatecertificationCertifiedchaptercloudcloudingcomputingcyberCybersecuritydecryptiondefendingdesignencryptionengineeringExamFirewallinfonetworknetworkingorganizationsaudisecSecuritysessionspecialtySummittalktechTechnicalThreatsTransformationwafWebinarأمناختبارالحوسبةالسحابيةالسعوديةالعربيةالمملكةامازونامن المعلوماتامن سيبرانيتجمعتحالفتصميمتقنيتقنيةحديثدردشةشرحشهادةفرعفصلمجتمعمرخصمنظمنقاض
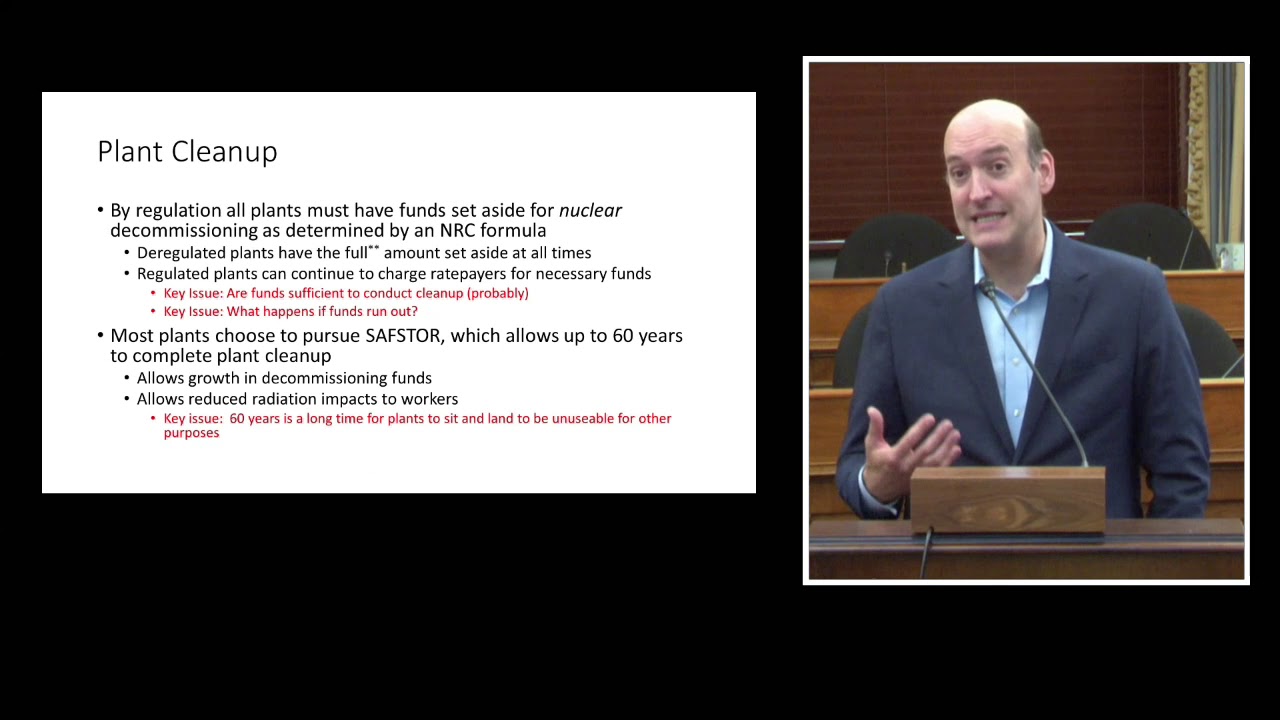
Decommissioning: A New Era for Nuclear Power; a Need for Congressional Oversight
Beyond NuclearConsolidated Interim Storage (CIS)DecommissioningDinéEESIEnvironmental and Energy Study Institutenational securityNatural Resources Defense CouncilNavajoNew MexicoNuclearNuclear Information and Resource ServiceNuclear Issues Study GroupNuclear Power PlantsNuclear WasteOversightRadioactive WasteRadioactive Waste Management AssociatesRadioactivityRisksSan Onofre Nuclear Generating StationThreatsYucca Mountain

Recent Posts
- Managing API Security at Scale With Gluu and Tyk
- Azure AI Insights: Understanding the Core Principles of AI-900 (Part 1)
- Cloud Native Live: Gear up for performance – Leveraging eBPF on Openshift with Project Calico
- Dapr Community Call – April 17th 2024 (#101)
- Sharepoint: Enforce File Naming Convention in a Folder inside a Document Library SharePoint Online
