Tag Archives: private
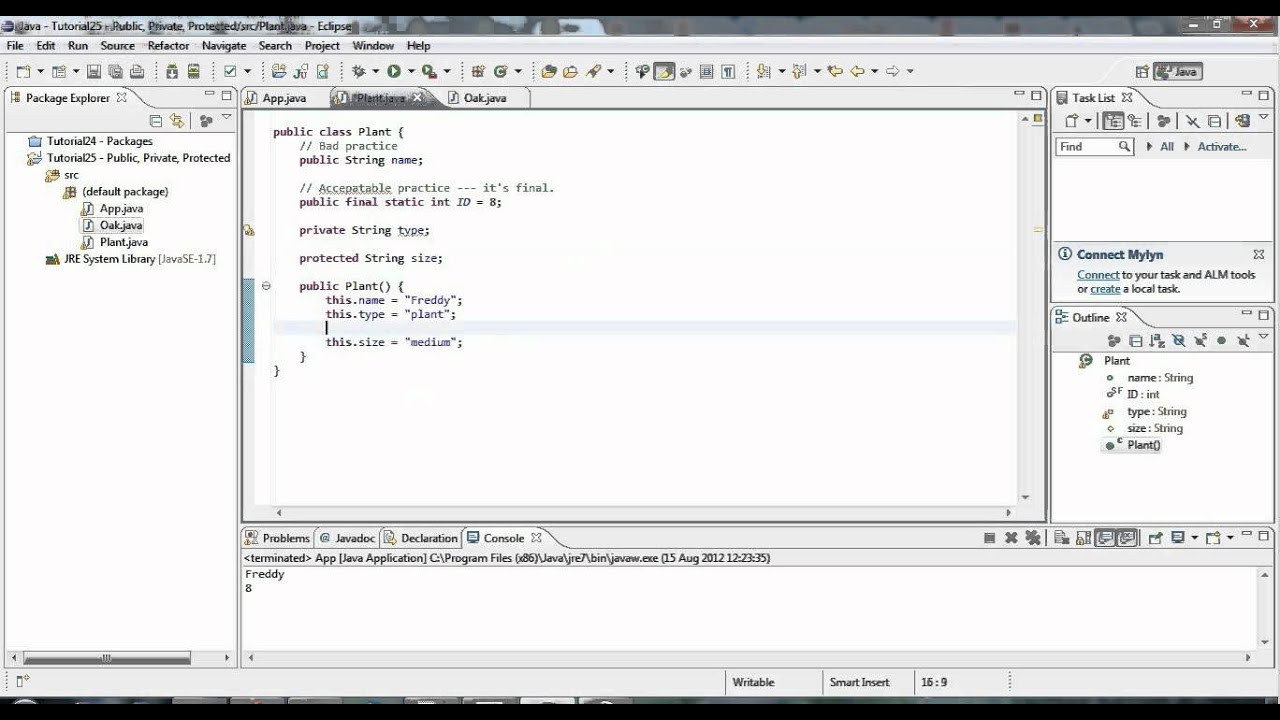


NSX T with Neutron and Kubernetes Advanced Integration and Best Practices
Centos Operating SystemcloudCloud Computingcloud hostingcloud nativecloud storageclustercnaContainersdata centerdefinedDevopsDockerinformationkubectlkuberneteslearningminikubenetworkingNSXnsx-tnsx-vOpenStackOpenStack (Software)privatepublicrdoRed Hat Software (Venture Funded Company)SDDCsdnsoftwaresoftware industrytrainingvirtual machineVirtualizationvmwarevmware nsx
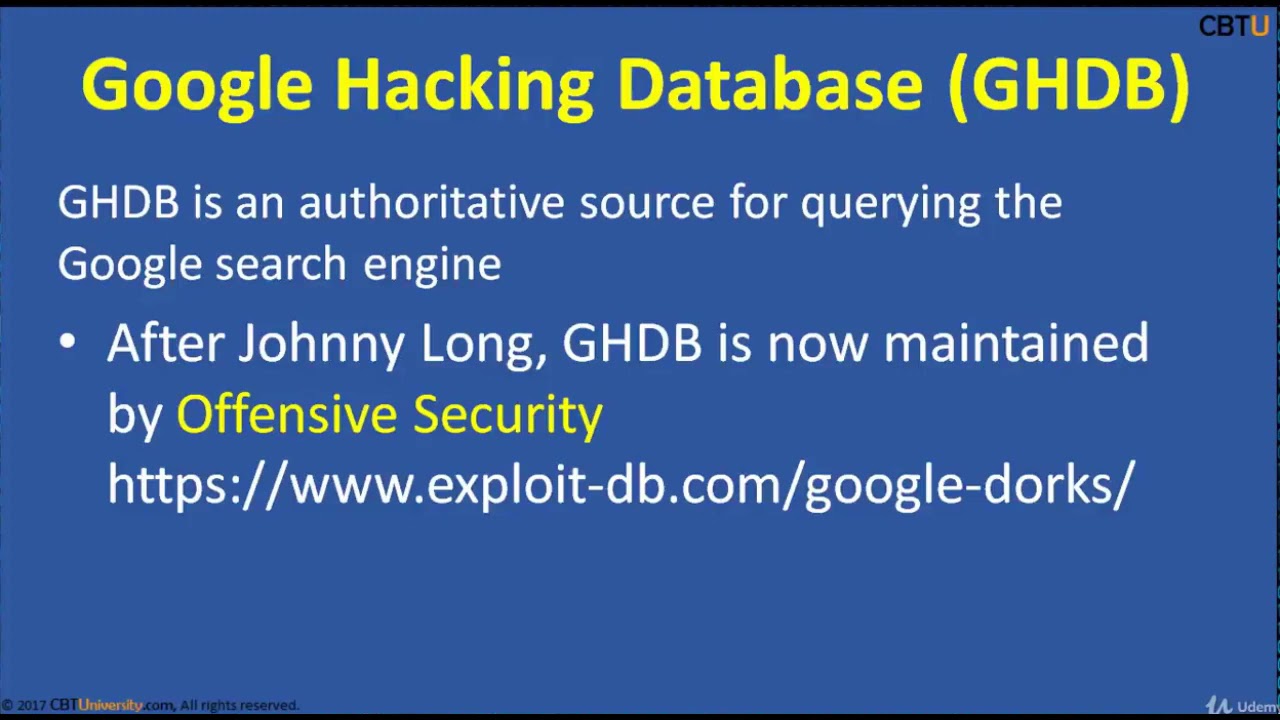
CEH2-3 Google Hacking Dorking
2015additionsaircrackbasicsBeginnersblackclicommandCompletecoursecrackcrackingenvironmentethicalexpertfootprintingforfreegreyguesthackhackerHacker (Interest)hackershackingHackshathdinstallinterfaceitKalikeylearn hacking in banglalineLinuxliveloggersmacchangernetworknmaponlinepenetrationprivateproxychainsreaverSecurityskillsSQLtermstestingtrainingUdemyvirtualvirtualboxVirtualBox (Software)vpnvpswhitewifiWindowswpawpa2

CEH1-1 Introduction to hacking
2015additionsaircrackbasicsBeginnersblackclicommandCompletecoursecrackcrackingenvironmentethicalexpertfootprintingforfreegreyguesthackhackerHacker (Interest)hackershackingHackshathdinstallinterfaceitKalikeylearn hacking in banglalineLinuxliveloggersmacchangernetworknmaponlinepenetrationprivateproxychainsreaverSecurityskillsSQLtermstestingtrainingUdemyvirtualvirtualboxVirtualBox (Software)vpnvpswhitewifiWindowswpawpa2
