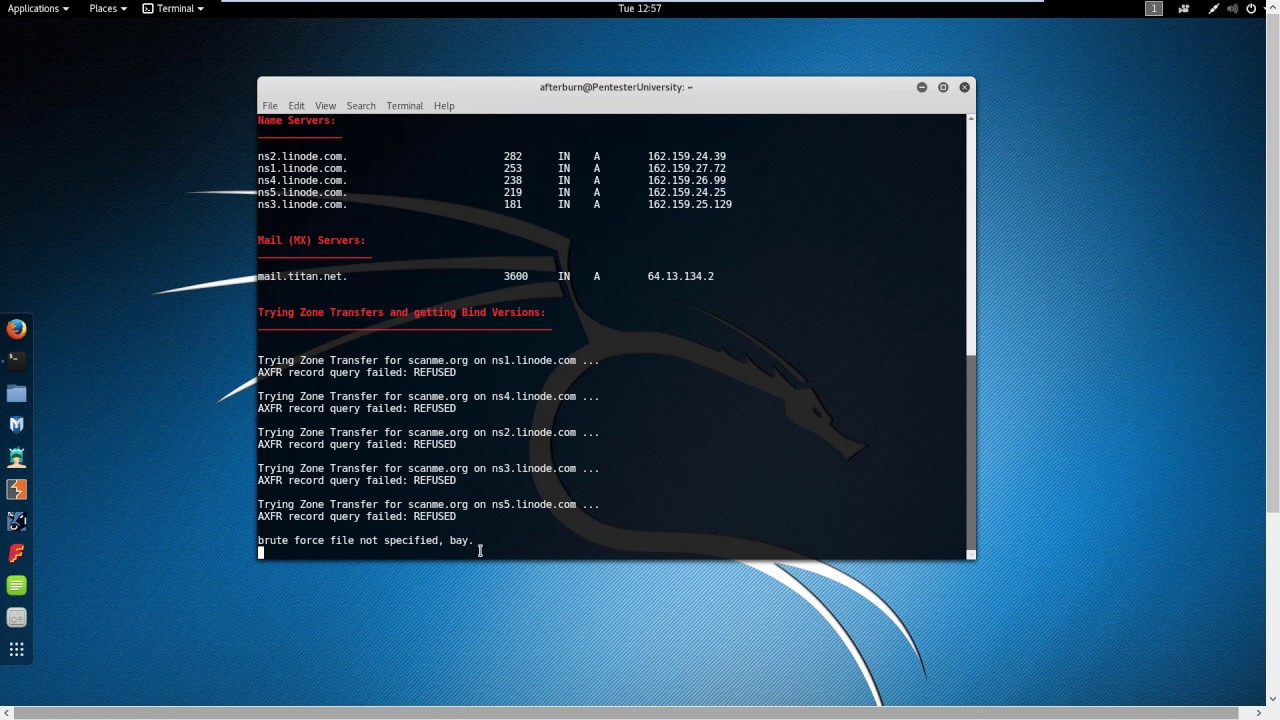
Tag Archives: Pentester

CEH18-3 Cloud Security Alliance
#Shells#TesteraircrackbasicsBeginnersburp suiteCompletecourseCybersecurityenumerationethicalethical hackerexpertfootprintingfreehackingHacking CourseHacking For Beginnershacking tutorialinformation securityInfosecitlearn hacking in banglamacchangermetasploitnmaponlinepass the hashpenetrationpenetration testerPentesterport scanningproxychainsreport writingreverse shellSecuritySQLtestingtrainingUdemyZero to Hero


CEH16-2 Mobile Hacking tools
#Shells#TesteraircrackbasicsBeginnersburp suiteCompletecourseCybersecurityenumerationethicalethical hackerexpertfootprintingfreehackingHacking CourseHacking For Beginnershacking tutorialinformation securityInfosecitlearn hacking in banglamacchangermetasploitnmaponlinepass the hashpenetrationpenetration testerPentesterport scanningproxychainsreport writingreverse shellSecuritySQLtestingtrainingUdemyZero to Hero
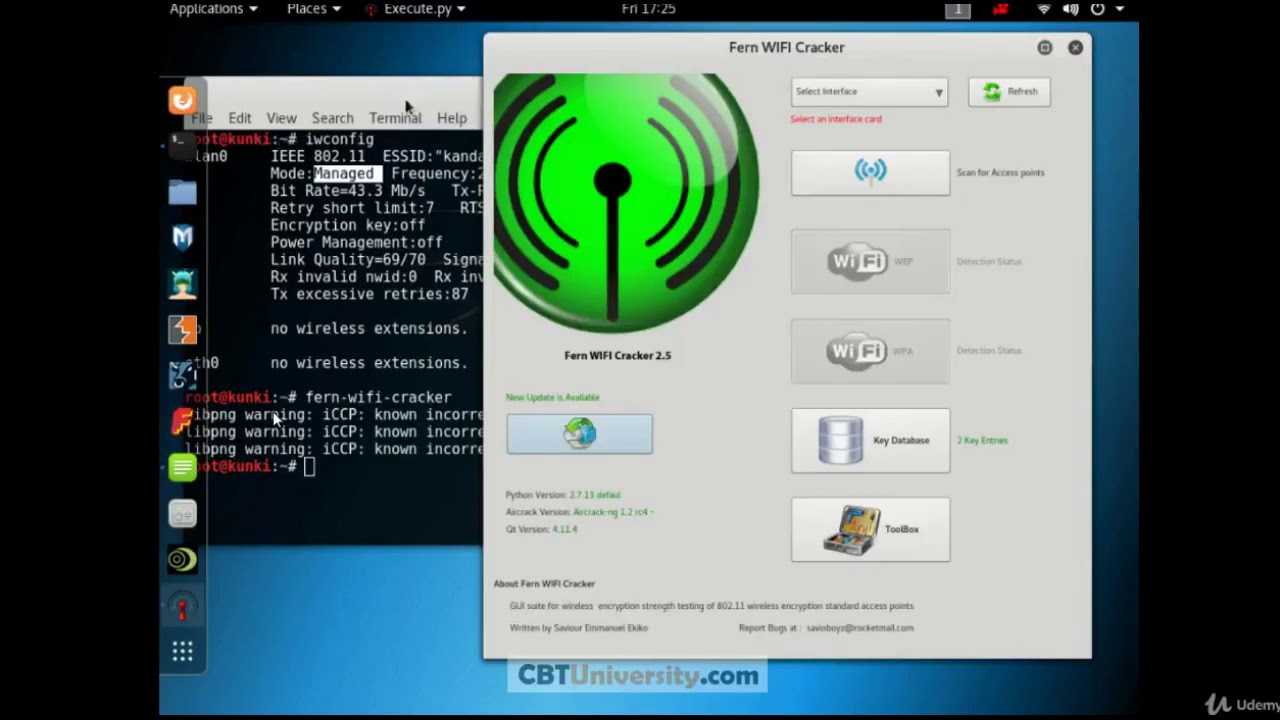
CEH 15 FERN wifi cracker
#Shells#TesteraircrackbasicsBeginnersburp suiteCompletecourseCybersecurityenumerationethicalethical hackerexpertfootprintingfreehackingHacking CourseHacking For Beginnershacking tutorialinformation securityInfosecitlearn hacking in banglamacchangermetasploitnmaponlinepass the hashpenetrationpenetration testerPentesterport scanningproxychainsreport writingreverse shellSecuritySQLtestingtrainingUdemyZero to Hero

Security Operations Center Training (SOC | SIEM) – The Hacktivists
arcsightAT&Tauditingblueteamcyber securityCybersecurityelearnsecurityevent managementExabeamfortinethackershoneypotIBM QRadarIncident responceinformation securityInfosecLogRhythmmalicious trafficmalware analysisMcAfeeMcAfee ESMMicro Focusoffensive securityoscpPentesterQRADARRapid7redteamrsaSecurity informationSecurity information and event managementSecuronixSIEMSIEM SolutionSOCSplunkspoofingTHREAT HUNTINGtrainingvulnerabilities


Hackers type Learn Ethical Hacking With Kali Linux | Ethical Hacking Tutorial | Kali Linux Tutorial
#Burpsuite#Cpasswords#Ethicalhacker#Ethicalhackingtutorials#Gpp#Hackingcourse#Hackingforbeginners#Hackingtutorial#Hackthebox#Informationsecurity#Kerberoasting#Llmnrpoisoning#M4v3r1ck#Mobilephonehacking#Nikto#Notekeeping#Ntlmrelay#Passthehash#Penetrationtester#Portscanning#Psexec#Reportwriting#Reverseshell#Shells#Smbrelay#Tester#Tokenimpersonation#ZerotoheroenumerationhackingInfosecmetasploitnmaposcppentestPentesterpivotingpythontesting