Tag Archives: metasploit
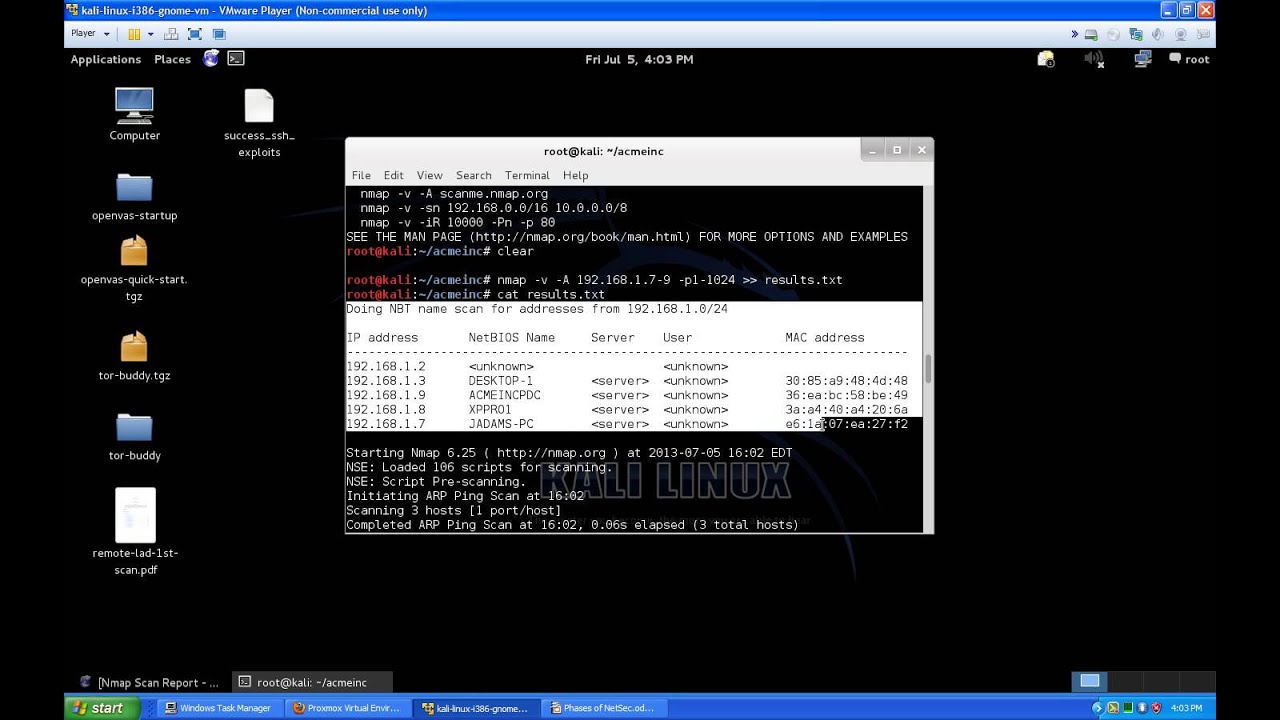
Network Security Phases Introduction For Beginners PT.3 Recon.
ArmitageComputerConfigurationdebianethicalexploithackerHacker (Character Power)hackingHow tohowtointroductionkali linuxLabLinuxmetasploitMicrosoft Windows (Operating System)networkNetwork Security (Organization Sector)nmappenetration testerpentestProxmoxProxmox VEProxmox Virtual EnvironmentSecurityServerTipstutorialvirtualvulnerabilityWindowszenmap

CEH16-2 Mobile Hacking tools
#Shells#TesteraircrackbasicsBeginnersburp suiteCompletecourseCybersecurityenumerationethicalethical hackerexpertfootprintingfreehackingHacking CourseHacking For Beginnershacking tutorialinformation securityInfosecitlearn hacking in banglamacchangermetasploitnmaponlinepass the hashpenetrationpenetration testerPentesterport scanningproxychainsreport writingreverse shellSecuritySQLtestingtrainingUdemyZero to Hero
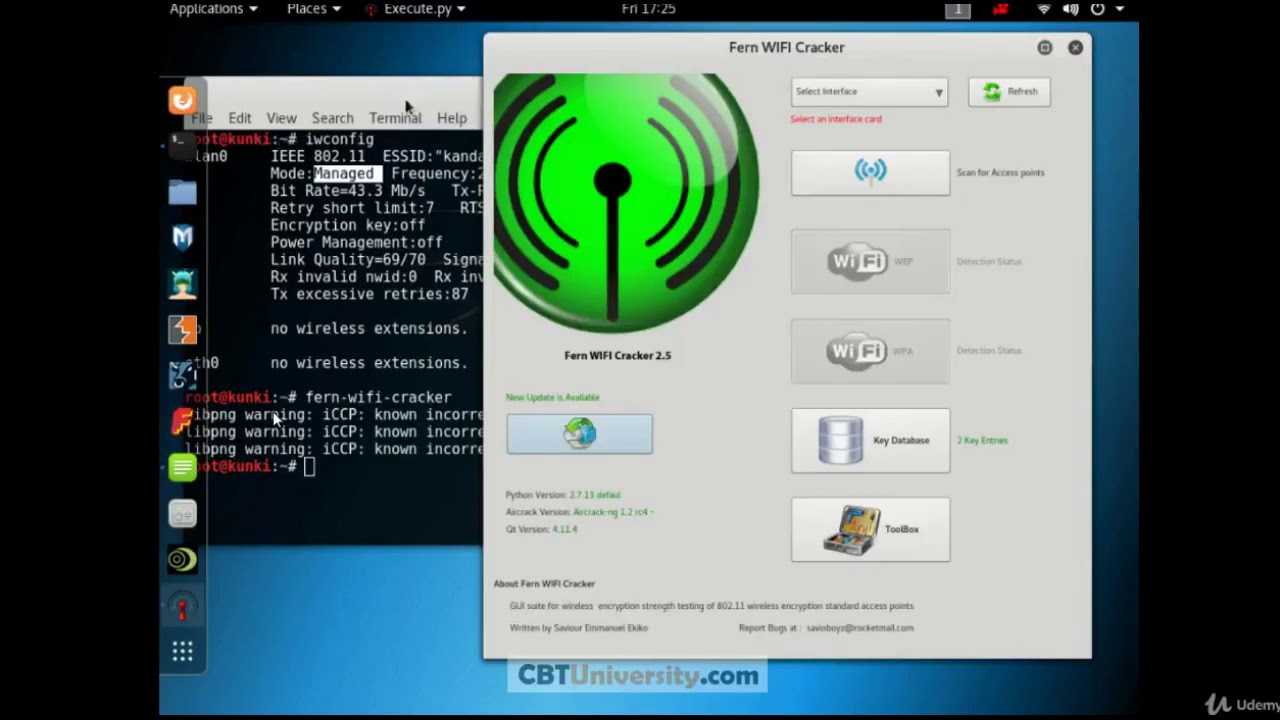
CEH 15 FERN wifi cracker
#Shells#TesteraircrackbasicsBeginnersburp suiteCompletecourseCybersecurityenumerationethicalethical hackerexpertfootprintingfreehackingHacking CourseHacking For Beginnershacking tutorialinformation securityInfosecitlearn hacking in banglamacchangermetasploitnmaponlinepass the hashpenetrationpenetration testerPentesterport scanningproxychainsreport writingreverse shellSecuritySQLtestingtrainingUdemyZero to Hero

Hackers type Learn Ethical Hacking With Kali Linux | Ethical Hacking Tutorial | Kali Linux Tutorial
#Burpsuite#Cpasswords#Ethicalhacker#Ethicalhackingtutorials#Gpp#Hackingcourse#Hackingforbeginners#Hackingtutorial#Hackthebox#Informationsecurity#Kerberoasting#Llmnrpoisoning#M4v3r1ck#Mobilephonehacking#Nikto#Notekeeping#Ntlmrelay#Passthehash#Penetrationtester#Portscanning#Psexec#Reportwriting#Reverseshell#Shells#Smbrelay#Tester#Tokenimpersonation#ZerotoheroenumerationhackingInfosecmetasploitnmaposcppentestPentesterpivotingpythontesting

Ethical Hacking | Part 2 | What is metasploit? | How to install metasploit on termux?
#ethical hacking on android#how to install metasploit on android using termux?#how to install metasploit-framework#how to install metasploit?#illustration#metasploit-framework#searchingandroidethical hackinggooglehackingHow tohow to use metasploitinstallmetasploitMetasploit projectSearch Engine OptimizationTERMUXtutorialtutorialsUCcjs0KK6V1YRqBPlo6aIpigwhite hat hackersyoutube

RED TEAM HACKING | CyberForce 2018
adwarebackdoorblack hatboot2rootbrute forcebuffer overflowcommand injectionCross-site scriptingcyberCybersecuritydenial of servicedictionary attackempireeternal blueexploitforkbombhackingkeyloggerlocal file inclusionmalwareman in the middlemetasploitpenetration testpentestphishingpivotingprivilege escalationpwnred teamremote shellshellshocksql injectionuse after freevirusvulnerabilitywhite hatzero day
Recent Posts
- Microsoft Chairman John Thompson on CEO Satya Nadella
- Lightning Talk: Best Practices on Organizing GitOps Repositories – Konstantinos Kapelonis, Codefresh
- 2023 10 03 Jenkins Infra Meeting
- Healthcare Integration | Opening the Doors to Communication
- How ICAN Tax Group Post Paved My Path to AFM Success Through the Financial Modeling Academy FMA
