Tag Archives: learn hacking

Introduction of ethical hacking | Ethical Hacking Course for Beginners – Cyber Yodha
all about hackingcyber securitycyber security full coursecyber yodhaethical hackingethical hacking careerEthical Hacking Courseethical hacking course in hindiethical hacking in 8 minutesfull ethical hacking coursehacking course in hindihacking kaise sikhehacking kya hota haihacking scopehow to learn ethical hackingIntroduction of ethical hackinglearn hackingtypes of hacktypes of hackerswhat is ethical hacking
4 Introduction – A Day in the Life of an Ethical Hacker
anonymouscomputer hackingcyber securityCybersecurityethical hackerethical hackingEthical Hacking Courseethical hacking for beginnersethical hacking tutorialethical hacking tutorials for beginnershackhackerhackershackingHacking Coursehacking tutorialhow to be a hackerhow to hackInfoseckali linuxlearn hackingmetasploitmr.robotow to become a hackerpassword crackingpenetration testingSecuritytechTechnologytop 10white hat hacker
Gaurav sharma | Ethical hacker || Bug Bounty Hunter || CEH || CCNA || ECSA || EC council
@Gaurav@lighnersCareercyber securityCyber Security Courseethical hackerethical hacker kaise baneethical hackingEthical Hacking Courseethical hacking for beginnersethical hacking for beginners hindiethical hacking in hindiethical hacking in indiaethical hacking toolsethicalh hacking vedio hacking vediohackershackingHacking Coursehacking detailskali linuxlearn hackingsalaryscopewhat is ethical hackingwhat is hacking
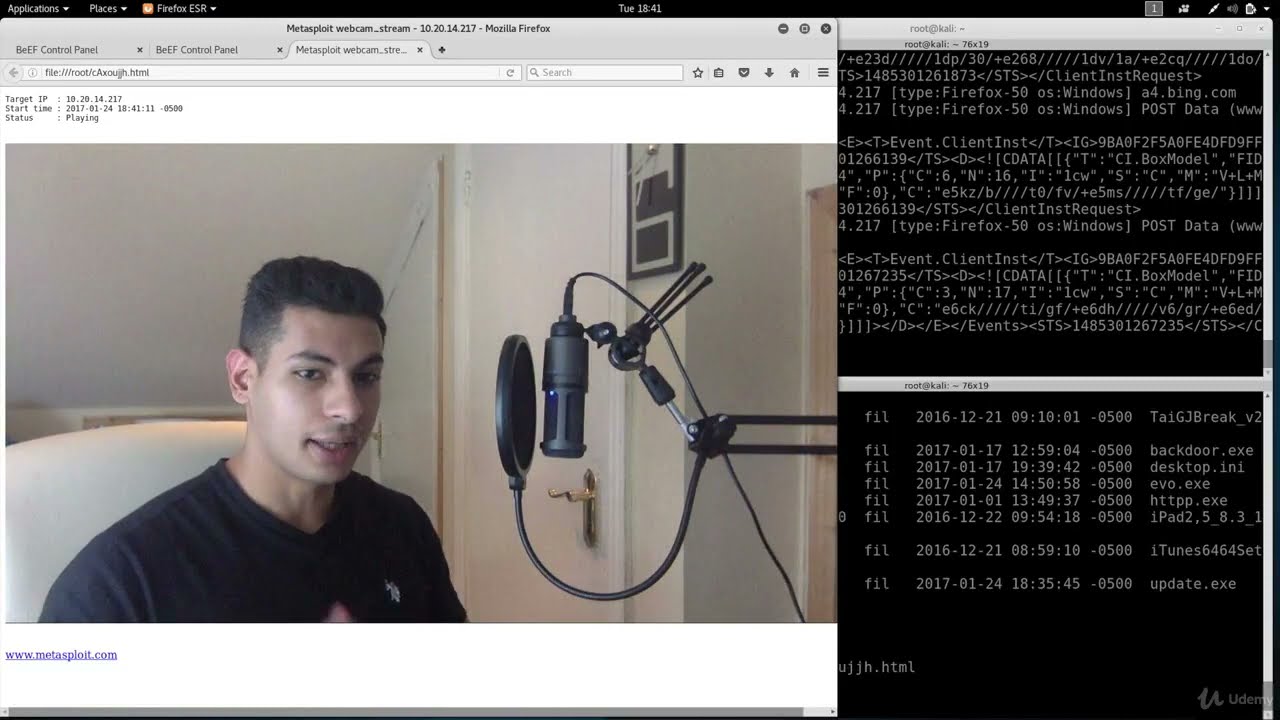

Ethical Hacking Using Kali Linux: A Beginner’s Guide to Command Line Mastery
Command Line TutorialCyber Threats SecurityCybersecurity Basicscybersecurity for beginnersCyberSecurity TrainingDigital Defenseethical hackingethical hacking tutorialhacking toolsinformation securityIT Securitykali linuxKali Linux Commandslearn hackingNetwork SecurityOnline securitypenetration testingstep by step guide

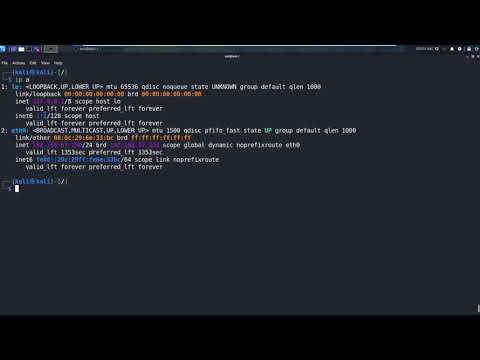
6 Introduction to Linux – Network Commands Update
anonymouscomputer hackingcyber securityCybersecurityethical hackerethical hackingEthical Hacking Courseethical hacking for beginnersethical hacking tutorialethical hacking tutorials for beginnershackhackerhackershackingHacking Coursehacking tutorialhow to be a hackerhow to hackInfoseckali linuxlearn hackingmetasploitmr.robotow to become a hackerpassword crackingpenetration testingSecuritytechTechnologytop 10white hat hacker

Best Gift for Cyber Security Students | Free ethical hacking course
Best Gift for Cyber Security Students | Free ethical hacking coursecyber securitycyber security career roadmapcyber security certificationscyber security full coursecyber security training for beginnerscyber yodhaethical hackerethical hackingEthical Hacking Courseethical hacking for beginnersfree ethical hacking coursefree giveawayfree hacking app mobilegift for happy new yearhappy new yearlearn hackingwhat is ethical hacking
7 Introduction to Linux – Installing and Updating Tools
anonymouscomputer hackingcyber securityCybersecurityethical hackerethical hackingEthical Hacking Courseethical hacking for beginnersethical hacking tutorialethical hacking tutorials for beginnershackhackerhackershackingHacking Coursehacking tutorialhow to be a hackerhow to hackInfoseckali linuxlearn hackingmetasploitmr.robotow to become a hackerpassword crackingpenetration testingSecuritytechTechnologytop 10white hat hacker
