Tag Archives: it

CEH16-2 Mobile Hacking tools
#Shells#TesteraircrackbasicsBeginnersburp suiteCompletecourseCybersecurityenumerationethicalethical hackerexpertfootprintingfreehackingHacking CourseHacking For Beginnershacking tutorialinformation securityInfosecitlearn hacking in banglamacchangermetasploitnmaponlinepass the hashpenetrationpenetration testerPentesterport scanningproxychainsreport writingreverse shellSecuritySQLtestingtrainingUdemyZero to Hero
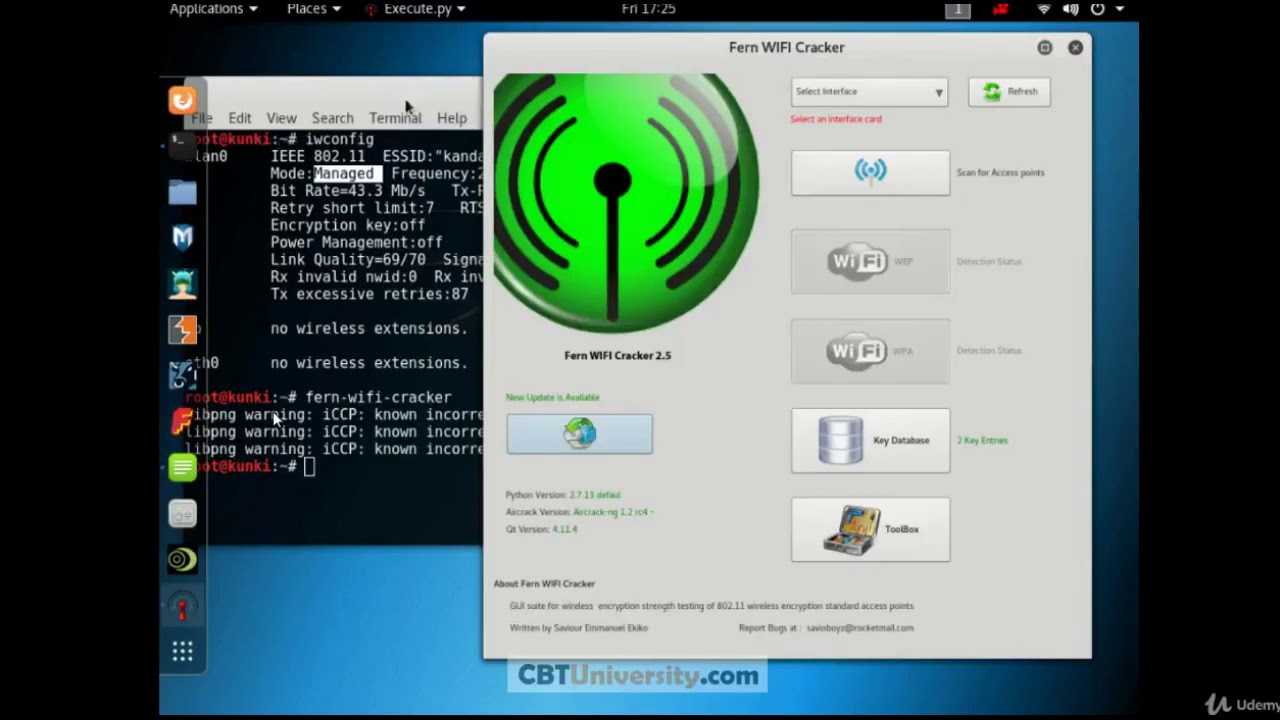
CEH 15 FERN wifi cracker
#Shells#TesteraircrackbasicsBeginnersburp suiteCompletecourseCybersecurityenumerationethicalethical hackerexpertfootprintingfreehackingHacking CourseHacking For Beginnershacking tutorialinformation securityInfosecitlearn hacking in banglamacchangermetasploitnmaponlinepass the hashpenetrationpenetration testerPentesterport scanningproxychainsreport writingreverse shellSecuritySQLtestingtrainingUdemyZero to Hero
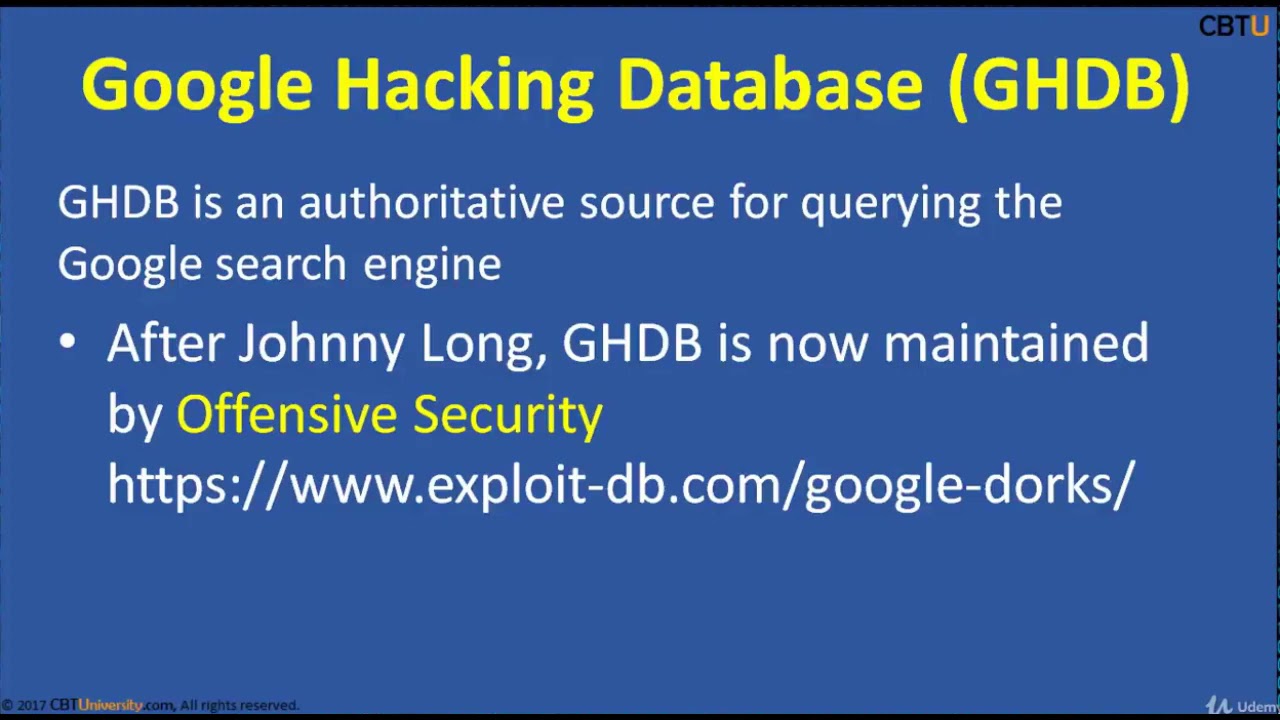
CEH2-3 Google Hacking Dorking
2015additionsaircrackbasicsBeginnersblackclicommandCompletecoursecrackcrackingenvironmentethicalexpertfootprintingforfreegreyguesthackhackerHacker (Interest)hackershackingHackshathdinstallinterfaceitKalikeylearn hacking in banglalineLinuxliveloggersmacchangernetworknmaponlinepenetrationprivateproxychainsreaverSecurityskillsSQLtermstestingtrainingUdemyvirtualvirtualboxVirtualBox (Software)vpnvpswhitewifiWindowswpawpa2
Kali Linux – vid 7 – Getting Started with Kali Linux Forensics – Linux Academy
2017AcademyaircrackandroidApplicationsbackdoorbacktrackbasicsBeginnersbotnetbrutecommandComputercourseeliEnglishethicalfacebookforforcefullgamegnuhackerhackinghowtoindustryinstagraminstallitKalikdelearnLessonLinuxMacMsnMyspacepcpenpenetrationproSecurityskillsoftwaretesttestingtoolstuttutorialsupworkvideovirtualboxvmwarewifiyahooyoutube


CEH1-1 Introduction to hacking
2015additionsaircrackbasicsBeginnersblackclicommandCompletecoursecrackcrackingenvironmentethicalexpertfootprintingforfreegreyguesthackhackerHacker (Interest)hackershackingHackshathdinstallinterfaceitKalikeylearn hacking in banglalineLinuxliveloggersmacchangernetworknmaponlinepenetrationprivateproxychainsreaverSecurityskillsSQLtermstestingtrainingUdemyvirtualvirtualboxVirtualBox (Software)vpnvpswhitewifiWindowswpawpa2

Microsoft Azure backup & recovery for nonprofits
365andAssess”AuthenticationbackupBusinessBusiness technology servicescenter”cloudcloud migrationcommunicationcomputerscomputingcreativedatadc”deploydesigndisasterFirewall and securityInformation technology servicesinstallitIT Serviceslaptops”networknetworkingOfficePCI complianceprocure”recovery”SecurityServicesSupport“acrobat“adobe“Advanced“Consult“managed“unified

Recent Posts
- Keynote: TLA+ at Microsoft: 16 Years in Production – David Langworthy
- Managing API Security at Scale With Gluu and Tyk
- Azure AI Insights: Understanding the Core Principles of AI-900 (Part 1)
- Cloud Native Live: Gear up for performance – Leveraging eBPF on Openshift with Project Calico
- Dapr Community Call – April 17th 2024 (#101)
