Tag Archives: ethical hacking

What you need to learn Ethical hacking and cyber security- Part-1
cyber securitycyber security training for beginnersdownload udemy courses for freeethical hackingethical hacking and cyber security courseethical hacking careerEthical Hacking Courseethical hacking tutorialethical hacking with python for beginnershack wifi passwordhackinghow to hack wifi passwordlearn ethical hacking and cybersecurityudemy coursesudemy courses for freeWhat you need to learn Ethical hacking and cyber security- Part-1wifi hacking
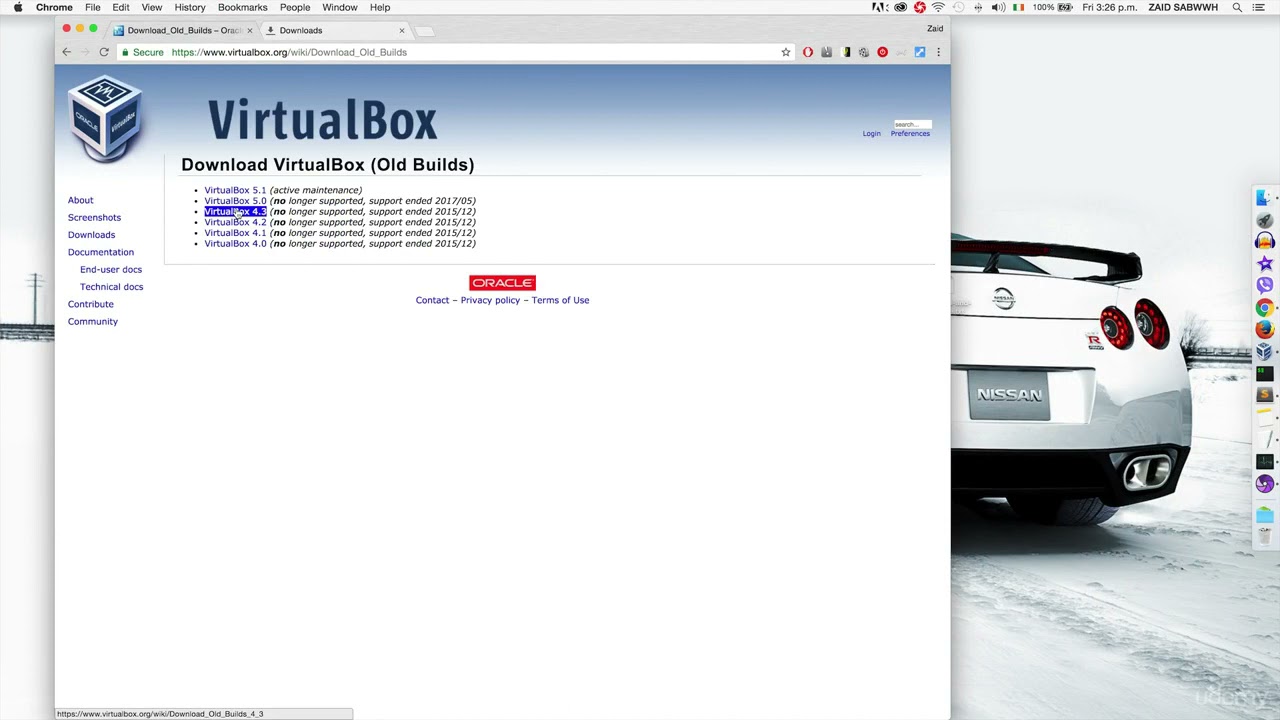
Connecting a Wireless Adapter To Kali |ETHICAL HACKING|
ethical hackingEthical Hacking Courseethical hacking tutorialethical hacking tutorial for beginnersethical hacking tutorials for beginnersfree wifihow to connect wifi without passwordincrease wifi speedKalikali do a bitchkali linuxkali linux installkali linux install windows 10Kali Linux Tutorialkali linux tutorial for beginnerskali uchis album nuevokali uchis new albumwhat is ethical hackingwifi
Blue Security Podcast – 2022-05-22 – Domain Controller Security
androidAppleblue hatblue teamcorporate itcorporate securityenterpriseenterprise itEnterprise Securityethical hackinggooglehackershackinginformation securityinformation security defendersinformation technologyInfoseciOSipadositLinuxmacosmicrosoftpersonal securitypodcastpodcastsSecurityvideo podcastsWindowswindows 10windows 11

Ethical Hacking Episode 6 Linux GUI apps #infosec #ethicalhacking #ceh #cyber
Application Securityblue teamcehclicomptiacybercyber skillsCybersecuritycybersecurity toolscybersecurity101EC-councileccouncilECSAedrpethical hackingethicalhackingethicalhacking 101hackinginformation securityInfosecLinuxmicrosoftnetwork mappingnmapnmap scriptingnmap toolpcpurpple teamsecsecplusSecuritysecurityplustechguyterminaltoolstop 10 cybersecurity skillsubuntuwhite teamwin10Windows10windows10insiderbuild

Blue Security Podcast – 2022-06-26 – Secure Authentication to Azure VMs
androidAppleblue hatblue teamcorporate itcorporate securityenterpriseenterprise itEnterprise Securityethical hackinggooglehackershackinginformation securityinformation security defendersinformation technologyInfoseciOSipadositLinuxmacosmicrosoftpersonal securitypodcastpodcastsSecurityvideo podcastsWindowswindows 10windows 11

Ethical Hacking Tutorial for Beginners – Full Course
certified ethical hackerCertified Ethical Hackingcertified ethical hacking coursecertified ethical hacking examcodequscyber securityethical hackingethical hacking careerEthical Hacking Courseethical hacking for beginnersethical hacking from scratchethical hacking full courseethical hacking pythonEthical Hacking trainingethical hacking tutorialethical hacking tutorial for beginnersitzlearn ethical hackingLearn Ethical Hacking From ScratchMorioh
Blue Security Podcast – 2022-09-04 – Cloud Security 101
androidAppleblue hatblue teamcorporate itcorporate securityenterpriseenterprise itEnterprise Securityethical hackinggooglehackershackinginformation securityinformation security defendersinformation technologyInfoseciOSipadositLinuxmacosmicrosoftpersonal securitypodcastpodcastsSecurityvideo podcastsWindowswindows 10windows 11
