Tag Archives: cybersecurity for beginners

Internet Security for Beginners – Full Course
cyber securityCyber Security Coursecyber security trainingCyber Security TutorialCybersecuritycybersecurity for beginnersinternet hacksInternet securityinternet security 2021internet security 2022internet security antivirusinternet security courseinternet security for beginnersinternet security guideinternet security kasperskyinternet security keyinternet security key 2021internet security protocolsinternet security tutorialitlearnzMorioh


Full Free Tutorial in Cyber Security for Beginners ( 5 hours ) – High Tech Solutions Platform – p720
complete cyber security tutorialCyber Security Coursecyber security explainedcyber security for beginnerscyber security full coursecyber security simplilearncyber security trainingcyber security training for beginnerscyber security tutorial for beginnerscyber security tutorials for beginnerscybersecurity for beginnersethical hacking course for beginnerslearn cyber securitynetwork security tutorial for beginnerswhat is cyber security
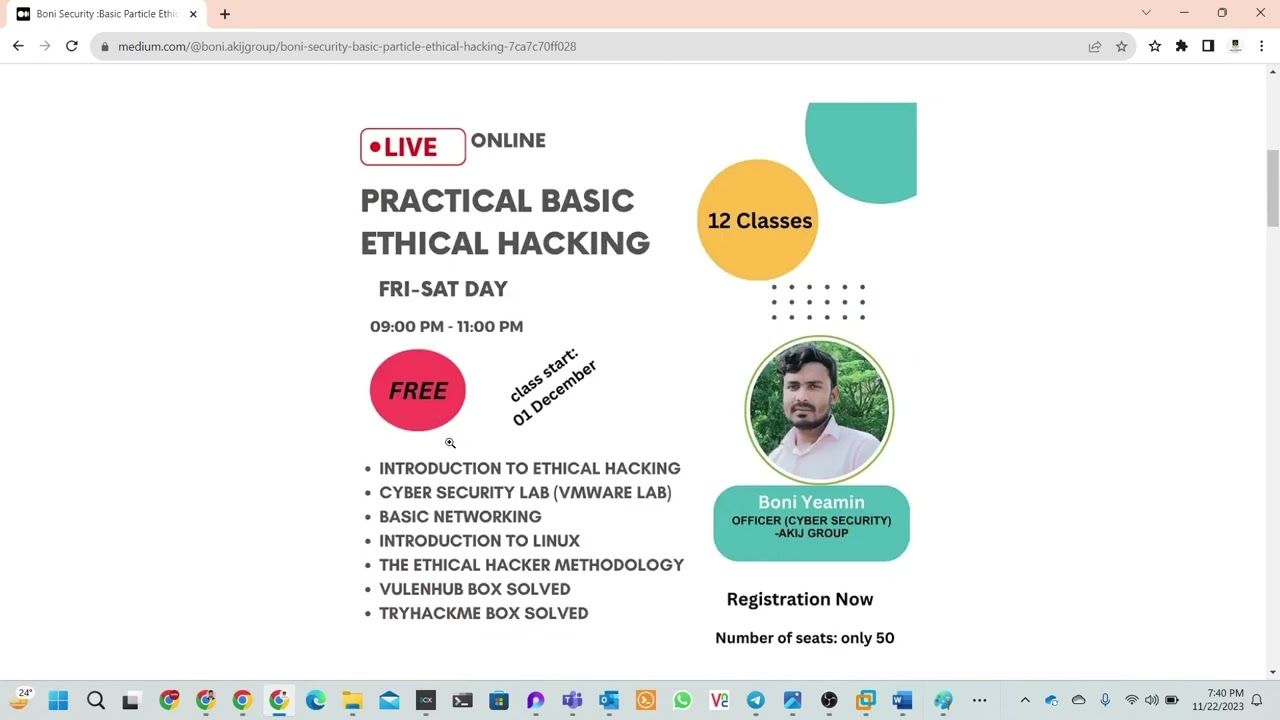
01 : Overview of the course outline | Basic Particle Ethical Hacking
bonisecuritybonyeamincyber securitycyber security classes for beginnerscyber security complete courseCyber Security Coursecyber security full course for beginnerscyber security projectscyber security training for beginnersCyber Security TutorialCybersecurityCyberSecurity Coursecybersecurity for beginnerslearn cyber securitylearn cyber security course freelearn cyber security freelearn cyber security from scratchlearn cyber security step by step

How to make your career in ethical hacking in 2020|Courses and Job opportunities|Tamil|Tech Tamizhan
career in hackingceh examceh exam questionsCybersecuritycybersecurity careerscybersecurity for beginnersethical hackingethical hacking books for beginnersethical hacking careerethical hacking career in tamilEthical Hacking Courseethical hacking for beginnersethical hacking jobsethical hacking jobs in tamilethical hacking tutorialethical hacking tutorial 2020hackingHacking CourseHacking Websitesipl 2020tamiltamizhantechtechtamizhan

Security Assessment & Testing Tutorial for Beginners
assessmentcissp security operationscodequscyber securitycyber security assessmentCyber Security Coursecyber security full coursecyber security testingCybersecuritycybersecurity assessmentCyberSecurity Coursecybersecurity for beginnerscybersecurity full coursecybersecurity testinginformation securityMoriohSecuritysecurity assessmentsecurity assessment & testing tutorial for beginnerssecurity assessment and testingsecurity testingtesttesting

Ethical Hacking Using Kali Linux: A Beginner’s Guide to Command Line Mastery
Command Line TutorialCyber Threats SecurityCybersecurity Basicscybersecurity for beginnersCyberSecurity TrainingDigital Defenseethical hackingethical hacking tutorialhacking toolsinformation securityIT Securitykali linuxKali Linux Commandslearn hackingNetwork SecurityOnline securitypenetration testingstep by step guide
How it Works Cybersecurity
careerscareers in cybersecuritycomputerscybercyber securitycyber security basicsCyber Security Coursecyber security jobscyber security trainingcyber security training for beginnersCyber Security TutorialCybersecuritycybersecurity careerscybersecurity edurekacybersecurity for beginnerscybersecurity jobsEnglishhackhackerhackinghow to start a career in cybersecurityinformation securityinformation technologyInfosecjobsTechnologytedxtalks

