Tag Archives: cyber security

Cryptography and Cyber Security || Full Course
block ciphersblockcypherblockcypher tutorialcryptographycryptography basicscryptography tutorialcyber securitycyber security careerCyber Security Coursecyber security training for beginnersDESdes exampledes example (encryption + decryption)des example in cryptographyDigital Certificatesencryptionencryption explainednumbers theoryopensslpasswordspublic keyPublic-key Cryptographyrsarsa algorithmrsa key generationSecuritystream cyphers
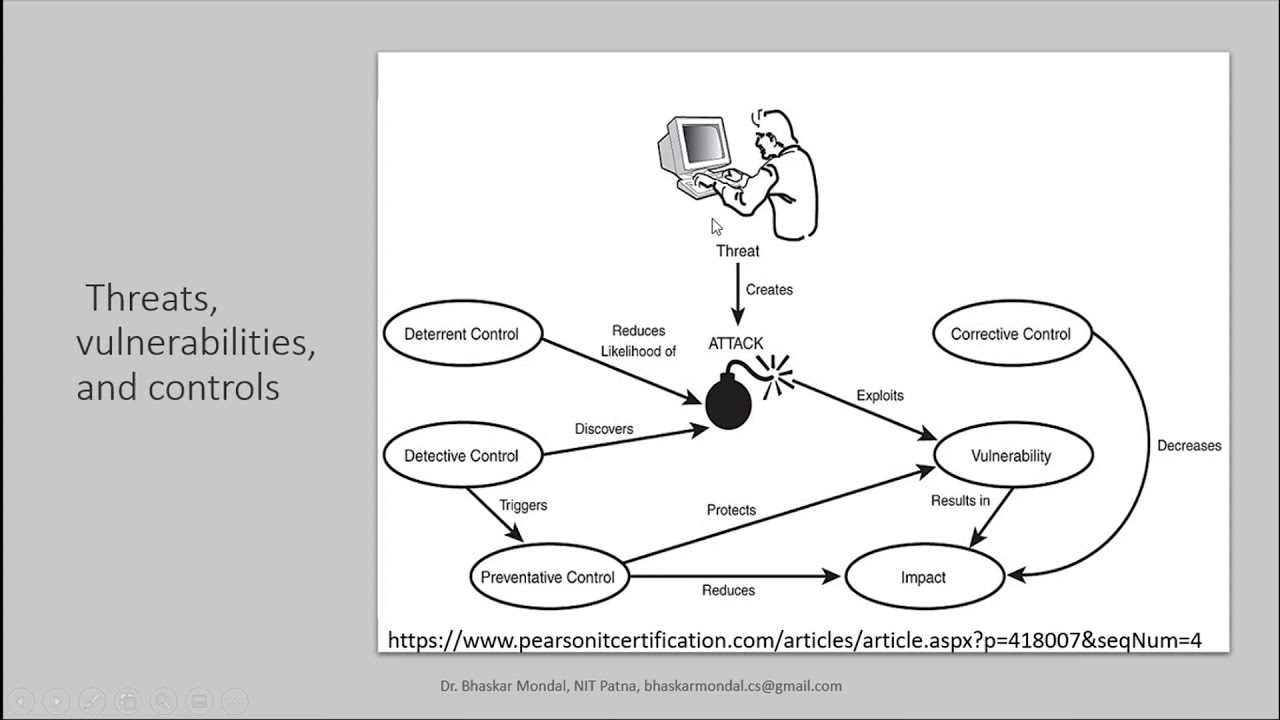
Threats, vulnerabilities, and controls in Information Security
Access ControlAESAIassignmentcode for beginners tutorialcomputecrypto systemcryptographycyber attackcyber securityDBMSdecryptiondeep learningDESdiyECCencryptionFLATguideHow toIDSinformation securityinstallintrusion detectionLATEXlearn to programlecturemachine learningMLNetwork Securityprivate keyprogrammingpublic keypythonrsascientific computingSecuritySHASQLTOCtutorial“computer laboratory” computer science GATE



What is Information Security in Ethical Hacking? | 04
cyber securitycyber security for workcyber security trainingCybersecurityData SecurityEthical Hacking Courseethical hacking tutorialhacking 101Identity Theft (Crime Type)info secInformation Security (Software Genre)information security traininginformation security training 2017Information Technology (Industry)Informationssicherheitkali linuxkali linux hindipreventing cyber crimevideos that explainwhat is ethical hackingwyntkसूचना सुरक्षा

Introduction to CyberSecurity | How to become Cybersecurity Analyst
cyber securitycyber security basicsCyber Security Coursecyber security full tutorial for beginnerscyber security trainingcyber security training for beginnersCyber Security TutorialCybersecurityCyberSecurity 101cybersecurity for beginnerscybersecurity fundamentalsedureka cyber securitygetting started with cyber securityintroduction to cyber securityintroduction to cyber security coursewhat is cyber securityyt:cc=on

Cyber Security Full Course / Ethical Hacking Complete Tutorial
BE A CERTIFIED ETHICAL HACKERCREATIVE COMMON LICENSECYBER CRIME & ITS SOLUTIONcyber securityCYBER SECURITY CERTIFICATEcyber security full courseCyberspaceDIGITAL LITERACYEMAIL HACKINGethical hackingETHICAL HACKING COURSE IN ENGLISHethical hacking for beginnersETHICAL HACKING FREE DOWNLOADFACEBOOK HACKINGFREE DOWNLOAD CYBER SECURITY COURSEHACKING AND ITS FUNDAMENTALSPen-testingREUSABLE VIDEOUPLOAD THIS VIDEO ON YOUR CHANNELWHATS APP HACKING


Security Operations Center Training (SOC | SIEM) – The Hacktivists
arcsightAT&Tauditingblueteamcyber securityCybersecurityelearnsecurityevent managementExabeamfortinethackershoneypotIBM QRadarIncident responceinformation securityInfosecLogRhythmmalicious trafficmalware analysisMcAfeeMcAfee ESMMicro Focusoffensive securityoscpPentesterQRADARRapid7redteamrsaSecurity informationSecurity information and event managementSecuronixSIEMSIEM SolutionSOCSplunkspoofingTHREAT HUNTINGtrainingvulnerabilities
Recent Posts
- How To Create AWS EC2 INSTANCE PLACEMENT GROUP?
- Private Key JWT authentication in WSO2 Identity Server #Identityin15
- Are you using a rubbish password | Computer Security | CyberSecurity | Dark Web | Cyber Awareness |
- Cyber Security with Cal-CSIC Commander Jonathan Nunez
- Tech Degree Tier List (Best Technology Majors Ranked)
