Tag Archives: basics

CEH18-3 Cloud Security Alliance
#Shells#TesteraircrackbasicsBeginnersburp suiteCompletecourseCybersecurityenumerationethicalethical hackerexpertfootprintingfreehackingHacking CourseHacking For Beginnershacking tutorialinformation securityInfosecitlearn hacking in banglamacchangermetasploitnmaponlinepass the hashpenetrationpenetration testerPentesterport scanningproxychainsreport writingreverse shellSecuritySQLtestingtrainingUdemyZero to Hero

TELOS BASICS: Blockchain, Tokens, Wallets, Exchanges, & more! — URDU, HINDI
accountsArchitecturebasicsBinancebitcoinBitSharesblockblockchainBlocknetCashcryptocryptocurrencyDasheasyeosEOS CanadaEOS StockholmEOS Swedeneos.ioeosioethereumGoldiconIOTALedgerlifeLiskLitecoinMoneromoneyNEOnetworkphotographyPowerproducersQuantstampramsteemstockholmswedenswedencornetTechnologytelosTelos AirdropTelos ExchangesTelos MainnetTelos RAMTelos SwedenTelos tradingTelos WalletsTokenstradingTRONVertcoin
ID Tokens VS Access Tokens: What’s the Difference?
access tokensAuth0authentication vs authorizationAuthorizationbasicsdeveloperfor dummieshow to use an access tokenid tokensid tokens vs access tokensidentityjames quickjson web tokenjson web token authenticationjwt token tutorialloginOAuth2Oktaokta devopenid and oauth 2.0OpenID Connectopenid connect tutorialopenid connect vs oauth2secure applicationsSecuritywhat is a tokenwhere do I get an accesss tokenwhere do I get an id token

CEH16-2 Mobile Hacking tools
#Shells#TesteraircrackbasicsBeginnersburp suiteCompletecourseCybersecurityenumerationethicalethical hackerexpertfootprintingfreehackingHacking CourseHacking For Beginnershacking tutorialinformation securityInfosecitlearn hacking in banglamacchangermetasploitnmaponlinepass the hashpenetrationpenetration testerPentesterport scanningproxychainsreport writingreverse shellSecuritySQLtestingtrainingUdemyZero to Hero

Cloud Computing Basics | What is Cloud Computing | Introduction to Cloud | AWS, Azure, GCP| English
AAASAWSaws basicsazureazure basicsBaaSbasicscloudcloud basicsCloud Computingcloud computing explainedcloud computing tutorial for beginnerscloud learningCloud offering modelscloud service modelsDRAASgitIaaSkubeneteslearning cloudNAASpaasSaaSServerlessTerraformWhat is AWSwhat is azurewhat is cloudwhat is cloud computingwhat is gcpwindows 2019
CEH 15 FERN wifi cracker
#Shells#TesteraircrackbasicsBeginnersburp suiteCompletecourseCybersecurityenumerationethicalethical hackerexpertfootprintingfreehackingHacking CourseHacking For Beginnershacking tutorialinformation securityInfosecitlearn hacking in banglamacchangermetasploitnmaponlinepass the hashpenetrationpenetration testerPentesterport scanningproxychainsreport writingreverse shellSecuritySQLtestingtrainingUdemyZero to Hero
CEH2-3 Google Hacking Dorking
2015additionsaircrackbasicsBeginnersblackclicommandCompletecoursecrackcrackingenvironmentethicalexpertfootprintingforfreegreyguesthackhackerHacker (Interest)hackershackingHackshathdinstallinterfaceitKalikeylearn hacking in banglalineLinuxliveloggersmacchangernetworknmaponlinepenetrationprivateproxychainsreaverSecurityskillsSQLtermstestingtrainingUdemyvirtualvirtualboxVirtualBox (Software)vpnvpswhitewifiWindowswpawpa2
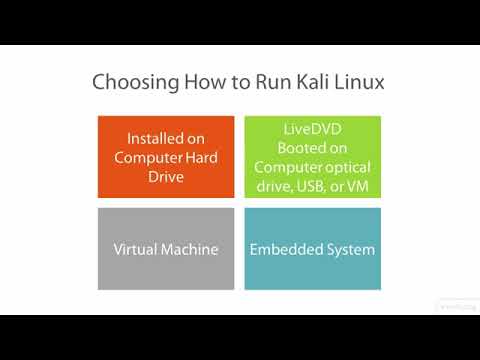
Kali Linux – vid 7 – Getting Started with Kali Linux Forensics – Linux Academy
2017AcademyaircrackandroidApplicationsbackdoorbacktrackbasicsBeginnersbotnetbrutecommandComputercourseeliEnglishethicalfacebookforforcefullgamegnuhackerhackinghowtoindustryinstagraminstallitKalikdelearnLessonLinuxMacMsnMyspacepcpenpenetrationproSecurityskillsoftwaretesttestingtoolstuttutorialsupworkvideovirtualboxvmwarewifiyahooyoutube

CEH1-1 Introduction to hacking
2015additionsaircrackbasicsBeginnersblackclicommandCompletecoursecrackcrackingenvironmentethicalexpertfootprintingforfreegreyguesthackhackerHacker (Interest)hackershackingHackshathdinstallinterfaceitKalikeylearn hacking in banglalineLinuxliveloggersmacchangernetworknmaponlinepenetrationprivateproxychainsreaverSecurityskillsSQLtermstestingtrainingUdemyvirtualvirtualboxVirtualBox (Software)vpnvpswhitewifiWindowswpawpa2
Recent Posts
- OWASP top 5 web application security risks 2021|Cyber security awareness training |Security Quotient
- Network Security News Summary for Thursday October 10 2019
- DFS101: 2.2 How hackers hack
- length Method Of String Class In Java |Part124| Core Java By Java Professional
- Profiling Java applications in a Kubernetes cluster
