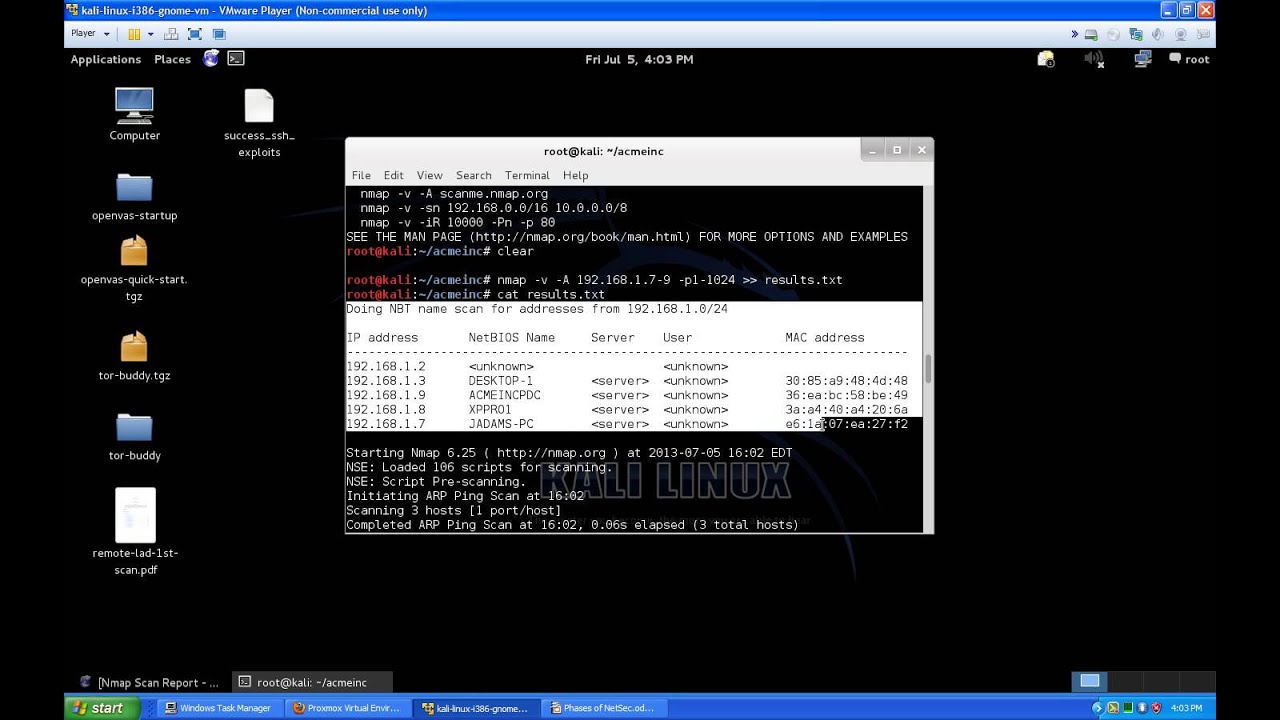
Network Security Phases Introduction For Beginners PT.3 Recon.
ArmitageComputerConfigurationdebianethicalexploithackerHacker (Character Power)hackingHow tohowtointroductionkali linuxLabLinuxmetasploitMicrosoft Windows (Operating System)networkNetwork Security (Organization Sector)nmappenetration testerpentestProxmoxProxmox VEProxmox Virtual EnvironmentSecurityServerTipstutorialvirtualvulnerabilityWindowszenmap
Recent Posts
- Risk Assessment Internal Control COSO Framework.
- 12 7 Create Risk Assessment Report
- Judge: Trump Lacks Presidential Immunity in Hush Money Case, Conviction Stands Pending Appeal
- Ask the Experts: What Security Teams Need to Focus on Now
- STACKLEAK: A Long Way to the Linux Kernel Mainline – Alexander Popov, Positive Technologies
